When was the last time you checked your Comcast cable modem settings?
Many ISPs manage user's modems, be it DSL or Cable. Even if the ISP doesn't own the modem, they typically push configuration or firmware updates to the modem to keep it up to date and connected to their network. Overall, this isn't a bad idea. Keeping the firmware and configuration up to date would be rather difficult to end users. However, as some users have experienced with Comcast, these changes are not always in the customer's best interest.
For example, if you do use a Comcast provided modem with Comcast's "Business Class" access, your modem will be assigned a set of static IP addresses, but in addition, you will also receive a DHCP assigned address. This address isn't really used for any of your traffic. But, the address is reachable, and the modem's configuration screen is accessible via http (port 80/tcp) if someone connects to the address. The default (and widely known) password doesn't appear to work to log in in this case, but any bugs present in the configuration may be exposed. It wouldn't be the first time that a web based admin interface includes an authentication bypass vulnerability.
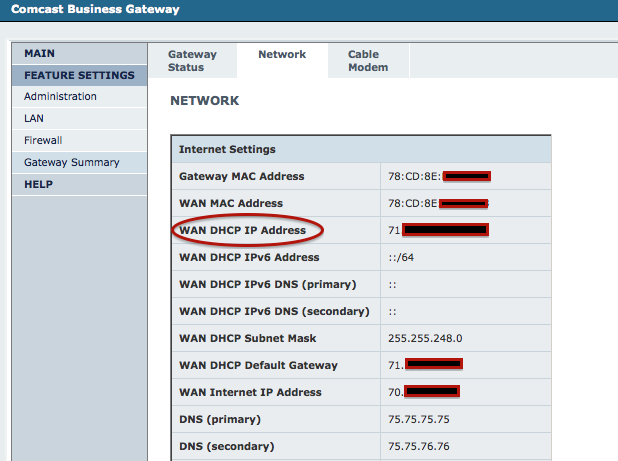
Luckily, the "dynamic" IP address that exposes the admin screen does not appear to be derived from the static address assigned to you by Comcast. So an attacker would have to scan all of Comcast's address space and would have no simple way to figure out who owns which dynamic address.
If you want to be a bit more secure, you can try and change the password from the default. However, be aware: As soon as the firmware is updated again, your new password will no longer work, neither will the default password. You will need to call Comcast support to have them reset the password.
Secondly, Comcast apparently started to enable public WiFi hotspots on cable modems that support the feature. In addition to charging users a rental fee for the modem, Comcast went ahead and turned the modems into public hotspots that can be used by other Comcast customers who happen to be in the area.
To turn off the public WiFi feature, you will need to connect to the Comcast customer portal (http://customer.comcast.com) and need to remove the option. After logging in, find the "Users & Preferences" option at the top of the screen
Then, find the "Manage Wifi" link (very small font, just below your address)
It is also a good idea to not use the default LAN IP range (e.g. 192.168.100.0/24 or 192.168.1.0/24). Instead, pick your own "random" range within RFC1918 space.
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |


Comments
http://www.peterlewis.com/2014/05/30/comcastic/
I think every Comcast customer just got a free "plausible deniability" card for any bad activity originating from their network.
"Wasn't me, must've been one of Comcast's free wifi users..."
Anonymous
Jun 1st 2014
1 decade ago
Anonymous
Jun 1st 2014
1 decade ago
Due to a recent relocation, I am now in Charter's territory. They seem to be following Comcast's model. They seem to delay "feature" introduction a bit. Probably allowing Comcast to be the testbed of customer reaction.
My service with both ISP's is/was residential class so I do not see the same leveraging of resources as the business class customers.
Anonymous
Jun 1st 2014
1 decade ago
It is much like a VoIP hardphone. You might own the phone, but when you place it on a network the VoIP central server controls it.
Anonymous
Jun 2nd 2014
1 decade ago
Comcast is happy to switch the cable modem over to bridging mode, which allows you to put a firewall that *you* completely control at your boundary. This makes the device somewhat more difficult to remotely crack and also (as far as I can determine) disables the "public hotspot" feature.
Standard DHCP is used for the public IP address. I expect the static IP configuration for a business-class account would not be affected.
Anonymous
Jun 2nd 2014
1 decade ago
The ISP needs full control of the WAN configuration of the device.
It would be nice if there would be modems available where the WAN device would be a separate encapsulated 'modem module' within the overall device -- the WAN module alone being the DOCSIS device. And no ISP control of the LAN side, possible ability to hot swap WAN modules; in order to allow the device to be used as a trusted firewall, with no possibility of ISP interference.
The user's webui and management should have connectivity from the LAN network alone.
The ISP's management should reside inside the WAN module alone, and it should include some TTL-based security protection.
Anonymous
Jun 2nd 2014
1 decade ago
I'm not sure how Comcast works but over here in Blighty one of our ISPs (BT) also offers free WiFi hotspots for fellow customers as default (BTFon) however the hotspot runs on a different IP to the customers connection so it is very easy for BT to distinguish which is customer traffic and which is a HotSpotter, and so the plausable deniability goes out of the window.
Our laws are also geared towards the account holder being responsible for all traffic to and from the connections regardless of who is using it, so if you leave your AP open or on the default WPA auth setting and someone does something nefarious with your connection then you as the account holder are responsible for that.
Anonymous
Jun 2nd 2014
1 decade ago
-- from a now-retired IBM-mainframe CPE (Computer Performance Evaluation) specialist.
So, if you have a COMCAST modem, produce some metrics:
1. disable the WiFi "option"
2. measure your download/upload speeds with your home-computer
3. enable the WiFi "option"
4. connect a wireless laptop to that HotSpot
5. singly, measure your download/upload speeds with your laptop
6. singly, measure your download/upload speeds with your home-computer
7. simultaneously, measure your download/upload speeds with both computers
Do steps #2 and #5 and #6 and #7 report same or different speeds?
End the speculation about separate/shared channels, by reporting your results.
QED
Anonymous
Jun 3rd 2014
1 decade ago
While hardware isolation within a single device would be nice, having the ISP switch the cable modem to bridging mode will get you *most* of the way there. Then you can configure your standalone firewall behind it to alert if its public IP address assigned by DHCP is in a nonrouteable range (i.e. the ISP switched the modem back to "router" mode and your firewall is suddenly talking to *its* DHCP server rather than the one at Comcast Central, and is getting a 192.168.x.x address).
Anonymous
Jun 3rd 2014
1 decade ago
Anonymous
Jun 21st 2015
1 decade ago