What's up with TCP 853 (DNS over TLS)?
I was looking at some of our data lat last week and noticed an increase probes on tcp port 853. For those of you who aren't aware, tcp port 853 is assigned to DNS over TLS as defined in RFC 7858. DNS over TLS (or DoT) was defined in 2016 as a way of hiding the contents of DNS requests from prying eyes on the network since DNS normally occurs in the clear over port 53. Of course, over the last few months all of the discussion has actually been about an alternative to DoT, DNS over HTTPS (or DoH) defined in RFC 8484, since the major web browser vendors (Google and Mozilla) have announced that they are or will be supporting DoH within the browser in the near future. For the moment, I'll stay out of the debate about the merits of DoT vs. DoH. But, back to this story, since I noticed the increase on port 853, let's discuss DoT. Because DoT requires setting up a TLS connection, it was defined as a TCP protocol (where DNS was primarily UDP). There was a subsequent RFC 8094 which defined DNS over DTLS which moved this back to UDP, but obviously required more traffic to set up the initual TLS encryption, though once established could then potentially be pretty efficient. I had actually setup DoT on my home (bind9) DNS server just a few weeks ago using stunnel as described in the docs from isc.org, to do some testing, so seeing this increase got my attention (though I hadn't actually opened 853 to the internet, just to my internal network). I haven't setup a netcat listener or honeypot to capture the traffic, but you can see that while there were a couple of brief spikes in the number of targets late last year and then a ramping up starting around the beginning of September, the big jump including new scanners has just ramped up since the beginning of Oct. This first graph is 365 days.
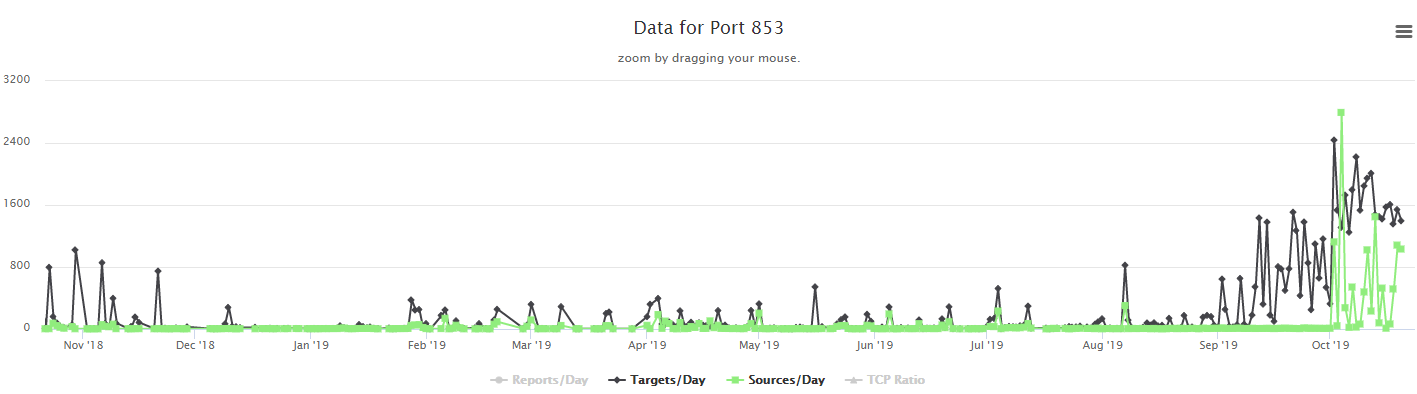
And here I've zoomed into about the last 90 days.
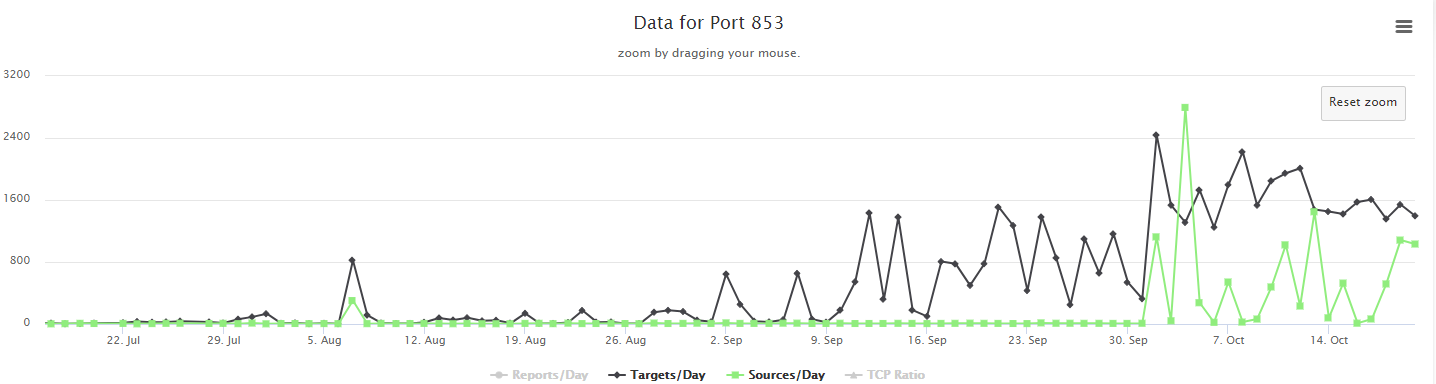
Since this is all TCP traffic (though I'm not showing the TCP ration on that graph, but I did look at the data), I doubt that this is actually a search for DDoS reflectors, but I don't really know what it is that they are looking for here. I hope to get a honeypot up in the next couple of days to see if I can figure it out, but in the meantime if any of our readers have any insights into what is going on here, please let us know in the comments or via our contact page.
---------------
Jim Clausing, GIAC GSE #26
jclausing --at-- isc [dot] sans (dot) edu
| Reverse-Engineering Malware: Malware Analysis Tools and Techniques | Online | Japan Standard Time | Mar 9th - Mar 14th 2026 |


Comments
Anonymous
Oct 22nd 2019
6 years ago