Video: Stego & Cryptominers
A couple of months ago, I read a blog post about malware, cryptominers and WAV file steganography: malware authors are concealing cryptominers in sound files (WAV) using steganography. Each bit of the cryptominer executable is stored as the least-significant bit of each Pulse Code Modulation value (16-bit values in this example).
Here is the start of a WAV file embedding a cryptominer executable via steganography:
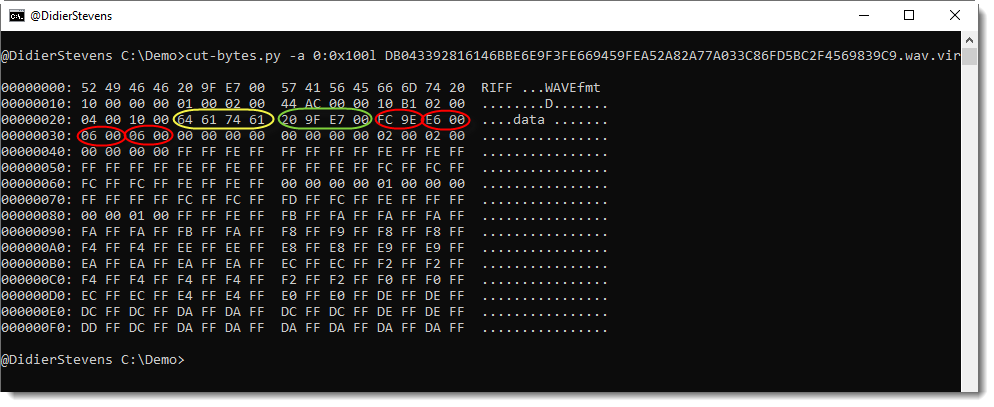
The byte values highlighted in red (and following), are signed 16-bit, little-endian values that encode PCM data. The least-significant bit of each 16-bit value encodes a single bit of the cryptominer executable.
When the least-significant bit is changed, the PCM value is only slightly different from the original value, and this change will not be perceptible to the human ear when the sound file is played.
I adapted my format-bytes.py program to be able to extract bit streams from arbitrary data.
In this video, I show step-by-step how to extract the embedded executable (PE file) from the WAV file. The command I use in the video is:
./format-bytes.py -d -f "bitstream=f:<h,b:0,j:<" "#c#['data']+8:" DB043392816146BBE6E9F3FE669459FEA52A82A77A033C86FD5BC2F4569839C9.wav.vir | ./pecheck.py -l P
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com


Comments