Testing TLSv1.3 and supported ciphers
Few months ago I posted a series (well, actually 2) diaries about testing SSL/TLS configuration – if you missed them, the diaries are available here and here.
Recently I needed to test several brand new servers which were running TLSv1.3 (among the other protocols). As I use nmap as my main SSL/TLS configuration verification tool, I quickly found out that the scripts I described in previous diaries do not yet support TLSv1.3. This made me look for other options.
Since the TLSv1.3 standard has been published as a RFC, and is available at https://tools.ietf.org/html/rfc8446 we can expect that this protocol will be used more and more. However, things are not that simple: since the TLS Working Group published various draft versions, there have been different implementations published as well. In other words, these implementations, which are based on different draft versions do not work with each other!
While the nmap scripts do not work yet, there are several other options, let’s take a look at them.
1) OpenSSL
OpenSSL version 1.1.1 includes support for TLSv1.3 – the easiest way is to check s_client options of your openssl binary, if the -tls1_3 option is there, you are good to go and can test if it works ok with Cloudflare, as shown below:
$ openssl s_client -tls1_3 -connect www.cloudflare.com:443
CONNECTED(00000003)
depth=1 C = US, O = DigiCert Inc, OU = www.digicert.com, CN = DigiCert ECC Extended Validation Server CA
…
---
New, TLSv1.3, Cipher is TLS_AES_256_GCM_SHA384
Server public key is 256 bit
Secure Renegotiation IS NOT supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
Early data was not sent
Verify return code: 20 (unable to get local issuer certificate)
---
Looking good, however we still need to somehow check which ciphers are supported. Luckily for us, the TLSv1.3 RFC supports only 5 cipher suites that you can see below:
+------------------------------+-------------+
| Description | Value |
+------------------------------+-------------+
| TLS_AES_128_GCM_SHA256 | {0x13,0x01} |
| TLS_AES_256_GCM_SHA384 | {0x13,0x02} |
| TLS_CHACHA20_POLY1305_SHA256 | {0x13,0x03} |
| TLS_AES_128_CCM_SHA256 | {0x13,0x04} |
| TLS_AES_128_CCM_8_SHA256 | {0x13,0x05} |
+------------------------------+-------------+
As you can see above, these are all strong ciphers, but our job should be still to check which ones are supported. We can do that with a little bit of scripting and by using the openssl binary, this time with the -ciphersuites option that allows us to define that cipher suite(s) which will be used for connection. Those of you using openssl already probably noticed that this option is different from the commonly used one, -cipher. The -ciphersuites option must be used with TLSv1.3, while -cipher can be used with any other SSL/TLS protocol.
Here is our script:
$ for cipher in TLS_AES_128_GCM_SHA256 TLS_AES_256_GCM_SHA384 TLS_CHACHA20_POLY1305_SHA256 TLS_AES_128_CCM_SHA256 TLS_AES_128_CCM_8_SHA256 ; do openssl s_client -tls1_3 -ciphersuites $cipher -connect www.cloudflare.com:443 < /dev/null > /dev/null 2>&1 && echo "$cipher" ; done
This script will loop through all 5 supported TLSv1.3 ciphersuites and will try to connect to the target server (I’m using Cloudflare for testing here). If the connection was successfully established, the first command (openssl) will result in true and the echo will print the cipher that worked. These are results from Cloudflare:
TLS_AES_128_GCM_SHA256
TLS_AES_256_GCM_SHA384
TLS_CHACHA20_POLY1305_SHA256
2) Testssl.sh
Our other option is to use the amazing testssl.sh script that I already wrote about before as well. You will need the very latest version of testssl.sh for TLSv1.3 support, so the best way to get it is to clone the repository from git:
$ git clone --depth 1 https://github.com/drwetter/testssl.sh.git
Once you’ve done that, you can test supported ciphers per protocol with the -E option, as shown in the figure below:
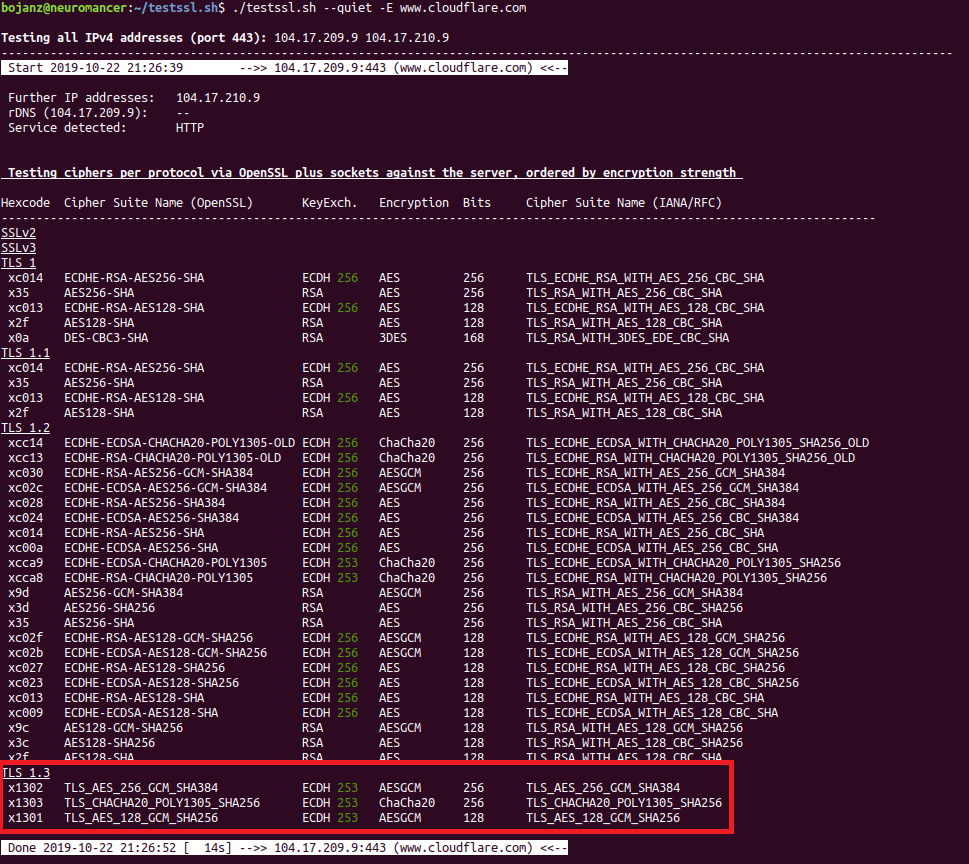
Time to go test support for TLSv1.3!
| Web App Penetration Testing and Ethical Hacking | London | Mar 2nd - Mar 7th 2026 |


Comments
Anonymous
Oct 23rd 2019
6 years ago