Some Memory Forensic with Forensic Suite (Volatility plugins)
In previous diaries we have talked about memory forensics and how important it is.
In this diary I will talk about a new volatility plugins called Forensic Suite written by Dave Lasalle.
The suite has 14 plugins and they cover different area of memory forensics
The Forensics Suite can be obtain from: http://downloads.volatilityfoundation.org/contest/2014/DaveLasalle_ForensicSuite.zip .
In this diary I will talk about some of the plugins
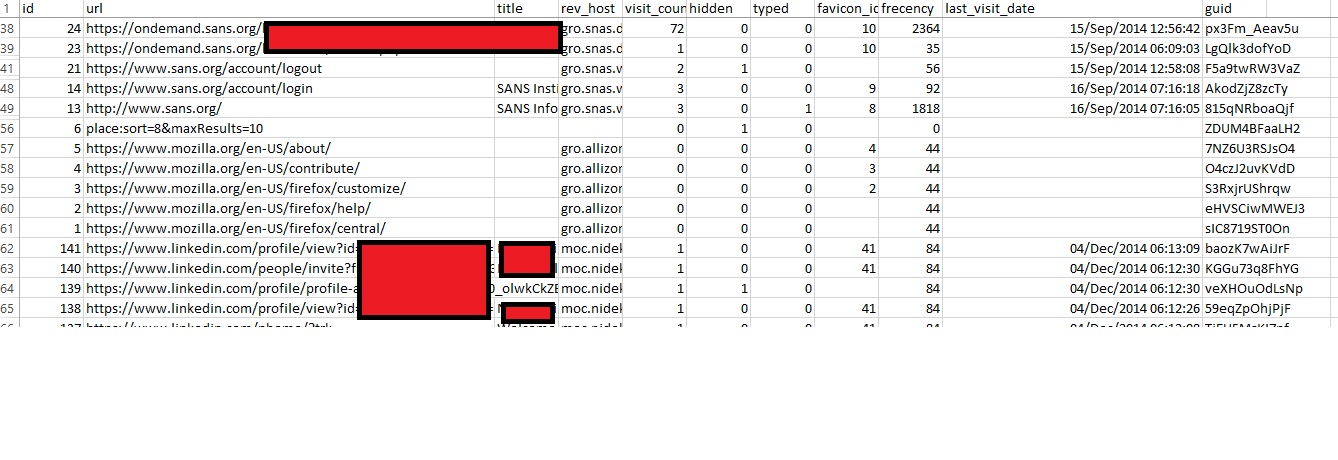
Firefox history:
To test this plugin first I browsed the internet using Firefox then I closed it to see how much data firefoxhistory plugin can obtain from the memory image that I acquired after closing firefox .
The firefoxhistory will parse the places.sqlite from the memory and show the output either on the screen or you can direct to csv file using –output=csv option. If you use the –output=csv option you will be able to play with your data using a spreadsheet software such as MS Excel
|
vol.py --plugin=plugins/ --profile=Win7SP1x86 --output=csv -f sampleimage.raw firefoxhistory > firefoxhistory.csv |
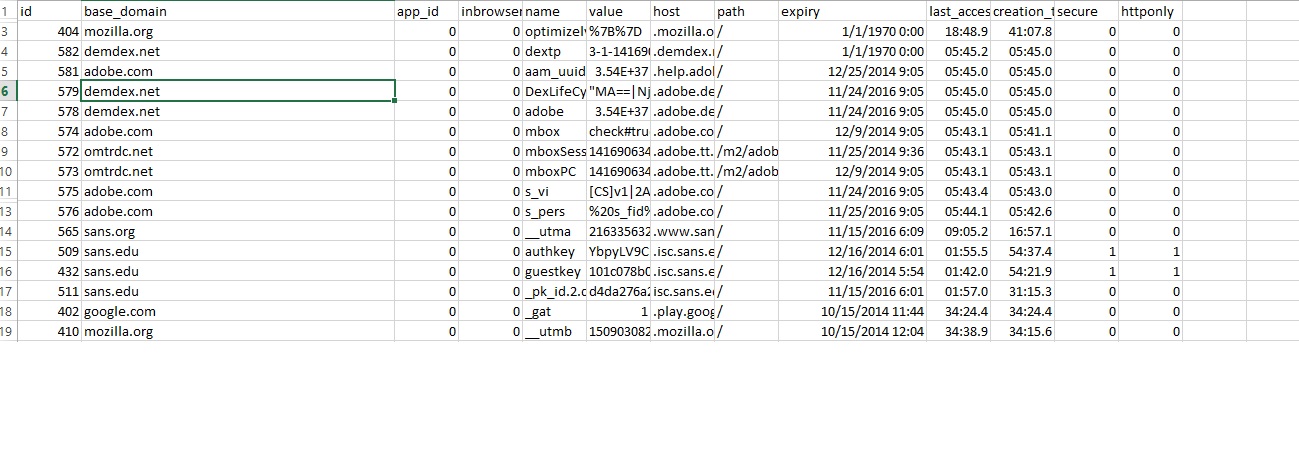
Firefoxcookies
Another Firefox forensics plugin is firefoxcookies , firefoxcookies will parse cookies.sqlite from the memory and show output to the screen or to a csv file
|
vol.py --plugin=plugins/ --profile=Win7SP1x86 --output=csv -f sampleimage.raw firefoxcookies > firefoxcookies.csv |
Forensics suite support chrome forensics as well, with the same syntax you can parse chrome history, cookies and downloads from the memory.
JAVA IDX Parser:
Many malicious jar files are coming from idx files , Forenscis suite has a plugin that will scan a memory for IDX files and it will parse it:
|
vol.py --plugin=plugins/ --profile=Win7SP1x86 -f sampleimage.raw idxparser |
And here is the output
|
Volatility Foundation Volatility Framework 2.4 Scanning for IDX files, this can take a while............. --------------------------------------------------------------------------------
[*] Section 1 (Metadata) found: Content length: 1624 Last modified date: Tue, 01 Feb 2005 18:28:24 GMT (epoch: 1107282504) Section 2 length: 270
[*] Section 2 (Download History) found: URL: http://java.com/jsp_utils/jreCheck.class IP: 137.254.16.66 content-length: 1624 last-modified: Tue, 01 Feb 2005 18:28:24 GMT content-type: application/java-vm date: Mon, 13 Feb 2012 04:21:28 GMT server: Sun-Java-System-Web-Server/7.0 -------------------------------------------------------------------------------- |

Comments