Quick Tip: Extracting all VBA Code from a Maldoc
"How can I extract all VBA code with oledump from this malicious Word document?".
It's a question I get from time to time.
The answer: "oledump.py -s a -v sample.vir".
With -s a, you select all streams. And with -v, you decompress VBA code. The combination "-s a -v" makes that all module streams are selected and thier VBA code is decompressed:
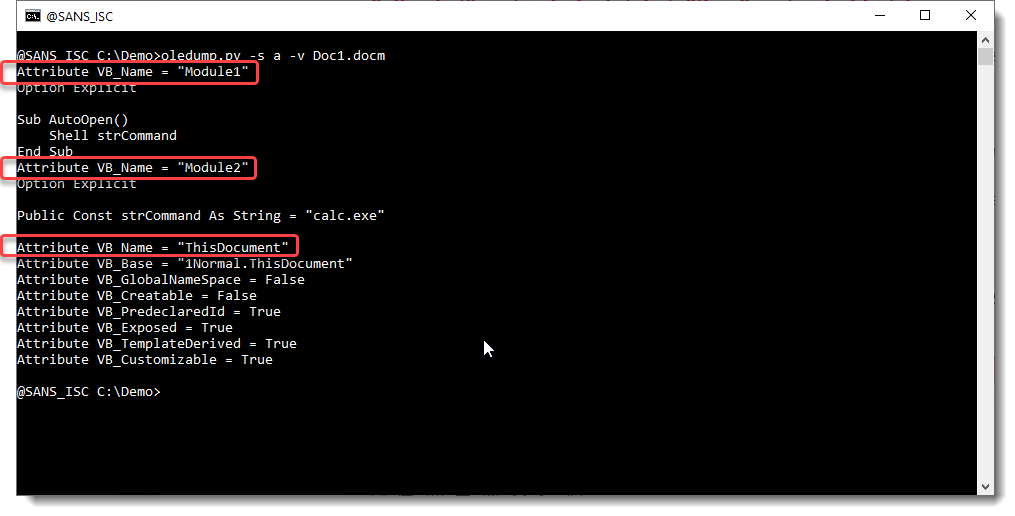
If you need to know when each module starts, look for a line starting with "Attribute VB_Name = ".
One can also select all streams, and output their content as JSON data. I'll make a small update to oledump to add JSON output of VBA code.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com
×
![modal content]()
Diary Archives


Comments