Psst. Your Browser Knows All Your Secrets.

This is a "guest diary" submitted by Sally Vandeven. We will gladly forward any responses or please use our comment/forum section to comment publically. Sally is currently enrolled in the SANS Masters Program.
I got to wondering one day how difficult it would be to find the crypto keys used by my browser and a web server for TLS sessions. I figured it would involve a memory dump, volatility, trial and error and maybe a little bit of luck. So I started looking around and like so many things in life….all you have to do is ask. Really. Just ask your browser to give you the secrets and it will! As icing on the cake, Wireshark will read in those secrets and decrypt the data for you. Here’s a quick rundown of the steps:
Set up an environment variable called SSLKEYLOGFILE that points to a writable flat text file. Both Firefox and Chrome (relatively current versions) will look for the variable when they start up. If it exists, the browser will write the values used to generate TLS session keys out to that file.
The file contents looks like this:

64 byte Client Random Values
96 byte Master Secret
16 byte encrypted pre-master secret
96 bytes pre-master secret
The Client_Random entry is for Diffie-Hellman negotiated sessions and the RSA entry is for sessions using RSA or DSA key exchange. If you have the captured TLS encrypted network traffic, these provide the missing pieces needed for decryption. Wireshark can take care of that for you. Again, all you have to do is ask.
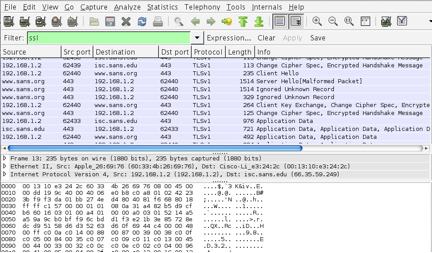
This is an encrypted TLS session, before giving Wireshark the secrets.
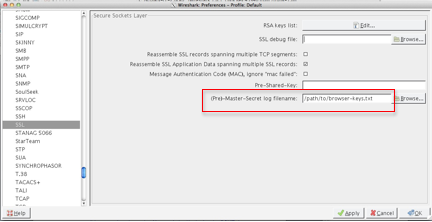
Point Wireshark at your file $SSLKEYLOGFILE. Select Edit -> Preferences -> Protocols -> SSL and then OK.
To see the decrypted data, use the display filter “ssl && http”. To look at a particular TCP session, right click on any of the entries and choose to “Follow SSL Stream”. This really means “Follow Decrypted SSL Stream”. Notice the new tab at the bottom labeled “Decrypted SSL data”. Incidentally, if you “Follow TCP Stream” you get the encrypted TCP stream.
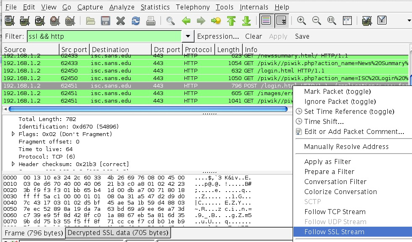
Wireshark’s awesome decryption feature.
Below is a sample of a decrypted SSL Stream. It contains a login attempt with username and password, some cookies and other goodies that web servers and browsers commonly exchange.
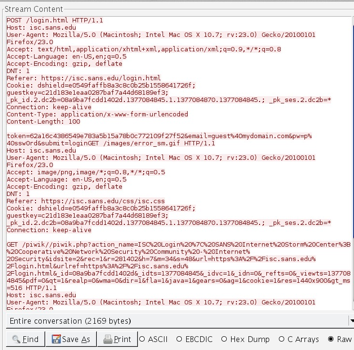
Remember: if you have a file with keys in it and the captured data on your system then anyone that can get their hands on these can decrypt too. Hey, if you are a pen-tester you might try setting be on the lookout for an $SSLKEYLOG variable on your targets. Interesting.
Give it a try but, as always, get written permission from yourself before you begin. Thanks for reading.
This exploration turned into a full blown paper that you can find here:
http://www.sans.org/reading-room/whitepapers/authentication/ssl-tls-whats-hood-34297


Comments
Anonymous
Aug 22nd 2013
1 decade ago
I just tried to set the environment variable in windows 8 system. Then i ran firefox 23.0 and started browsing in webpages as facebook, or email that uses SSL. Nevertheless no file with SSLKEYLOGFILE data was created...
Anonymous
Aug 29th 2013
1 decade ago
I just installed FF 23 on a Windows 8 VM and tried it. It seems to work fine. I tried both user environment variable and system environment variable. If you set the variable from the command line only the command shell will see it, not the browser. To set my variable, I brought up Control Panel and searched for "environment". Here you can add a user variable and it takes effect immediately and can be accessed by the browser. It also writes it to the registry in HKCU\Environment.
Sally
Anonymous
Aug 30th 2013
1 decade ago
You are right, i just had to set the system enviroment variable frome the control panel and not just in the command prompt.
Now it works fine.
Anonymous
Sep 3rd 2013
1 decade ago
Anonymous
Sep 11th 2013
1 decade ago
There's a good discussion in http://sharkfest.wireshark.org/sharkfest.12/presentations/MB-1_SSL_Troubleshooting_with%20_Wireshark_Software.pdf
When I tried with Apache, only certain ciphers were decryptable. The SSLv2 ones, and "EXP-*" ciphers in TLS1 and SSLv3, were not. In order to ensure that only decryptable ciphers (or vice-versa) are used, you can set options in Apache or preferences in Firefox.
Sorry for being vague, it's been a while. Thanks for the tip re. the environment variable.
Anonymous
Sep 19th 2013
1 decade ago
I am a newbie and I don't know how to set up an environment variable called SSLKEYLOGFILE that points to a writable flat text file on a windows 8.1 machine. Could you please show me step by step how to do it? Thanks in advance
Anonymous
Nov 24th 2014
1 decade ago
Anonymous
Apr 16th 2015
1 decade ago