Protecting Home Office and Enterprise in 2021
Because of COVID, 2020 saw a major shift from working at the "office" to working at home which led to shift the attacks to the user @home. Everything points that 2020 was a year for ransomware and COVID-19 themed campaigns. Without exceptions, phishing emails have been the most prolific initial attack vector targeting organizations and home users. This will likely get worse and more disruptive this coming year.
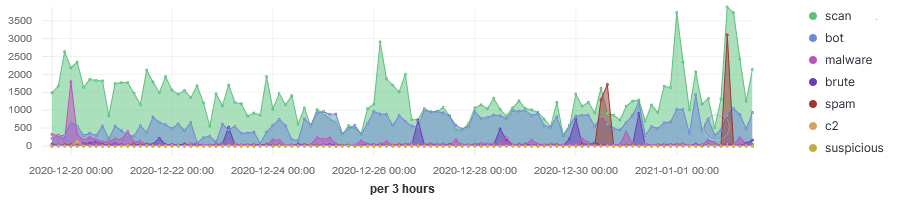
Past 14 Days - My IP Threat Intel Activity
Every year there are prediction on what we should expect in the coming year and what to watch for. Instead, what can be done to secure the enterprise?
- Implement multi-factor authentication
- Extending security to a remote force
- Review cloud security policies
- Better protection for IoT
- Must ensure backups are secure and cannot be reached to prevent attackers from finding and delete them
- Equally important - regularly test backups to ensure the data can be recovered
- Use and share Threat Intel to track suspicious activity [1][2]
- Better network analytics and log collection [3][4][5]
- Monitor host and network activity [3][4][5]
- Better detection and prevention against phishing email attacks [10]
- Review and test employees against security awareness program [11]
- Apply system security update as soon as appropriate
- Keep antivirus software current
Over the past year, one of the most difficult tasks has been how to detect and prevent being compromised by unmanaged devices. With a large population of employees working from a home office, some forced to use their personal devices, if compromised, have the potential of exploiting other systems in their home network as well as the enterprise connected network (i.e. VPN access to employer network). This challenge will continue for the forceable future.
Share your predictions for 2021, what is going to keep you up at night?
[1] https://www.anomali.com/resources/staxx
[2] https://otx.alienvault.com
[3] https://www.elastic.co
[4] http://rocknsm.io
[5] https://securityonionsolutions.com
[6] https://us-cert.cisa.gov
[7] https://cyber.gc.ca
[8] https://www.ncsc.gov.uk
[9] https://www.enisa.europa.eu/topics/csirts-in-europe
[10] https://cyber.gc.ca/en/assemblyline
[11] https://www.sans.org/security-awareness-training?msc=main-nav
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu


Comments