PDF + maldoc1 = maldoc2
I received another example of a PDF file that contains a malicious MS Office document. Sample (MD5 0c044fd59cc6ccc28a48937bc69cc0c4).
This time I want to focus on the analysis of such a sample.
First we run pdfid to identify the sample.
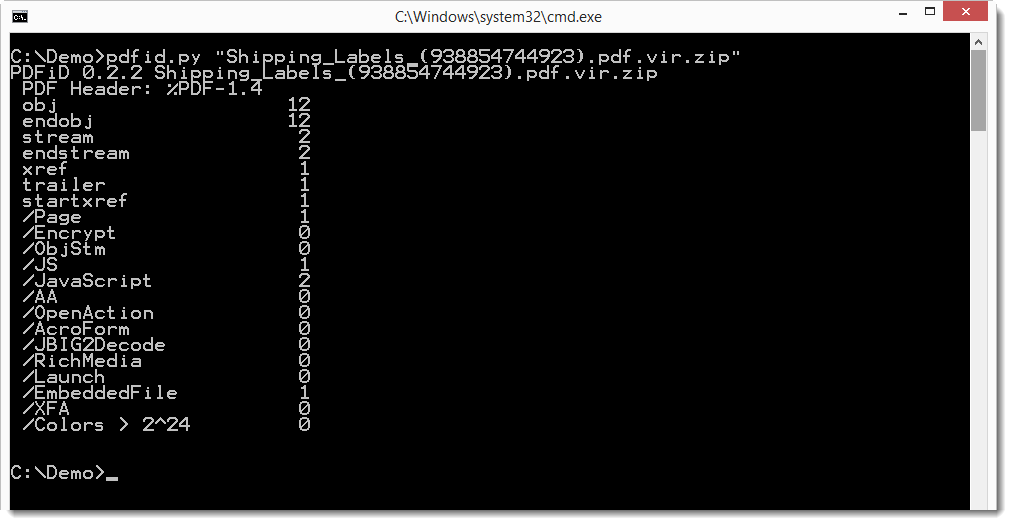
It contains JavaScript and an embedded file. Let's take a look at the JavaScript first with pdf-parser.
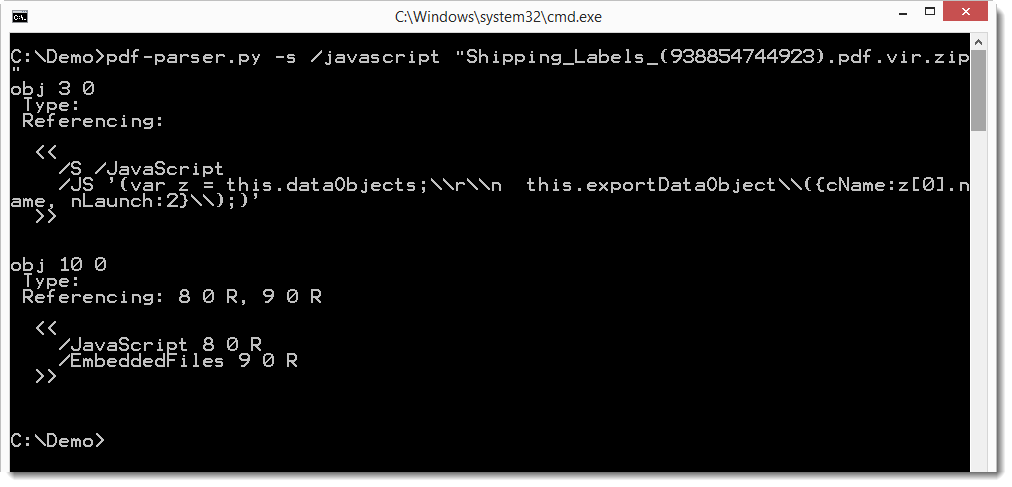
Remark that the JavaScript is not obfuscated this time. It's simple, just two lines: these 2 statements export the embedded file to a temporary folder, and then launch it (provided the user clicks OK on the warnings).
So let's take a look at the embedded file with pdf-parser. We use option -H to get more info on the streams (the embedded file), like the hashes.
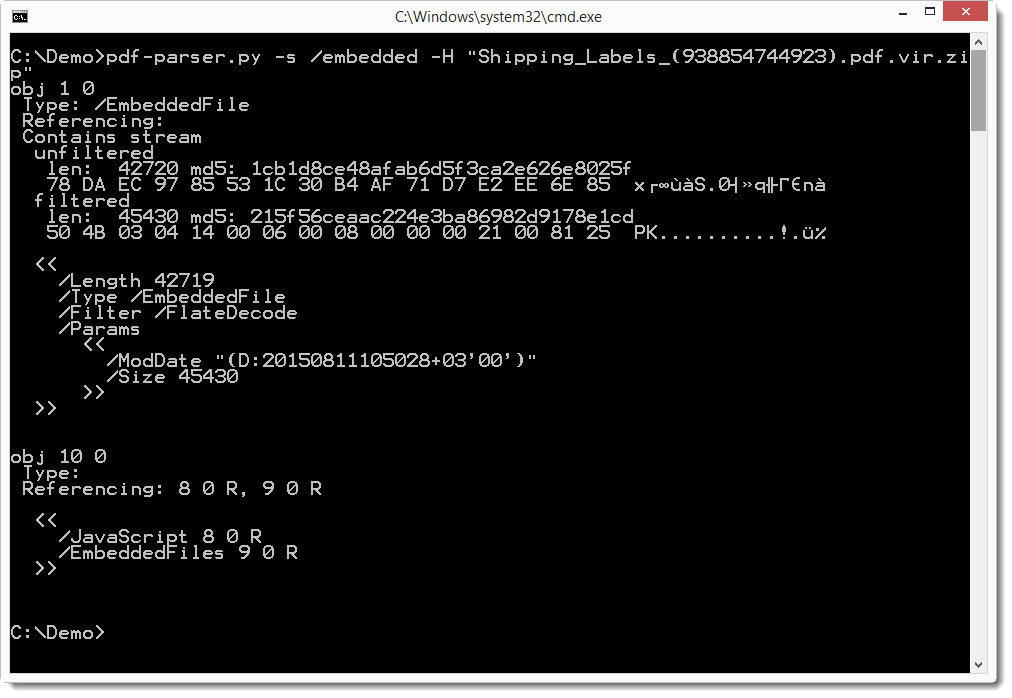
The embedded file is most likely a ZIP file (magic number PK). Looking at object 9, we see that the name is 2.docm.
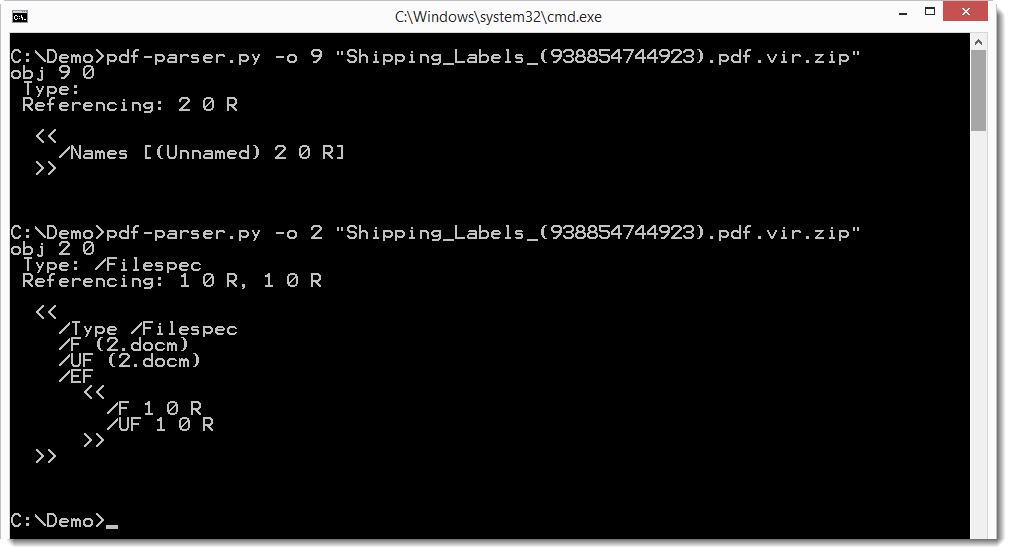
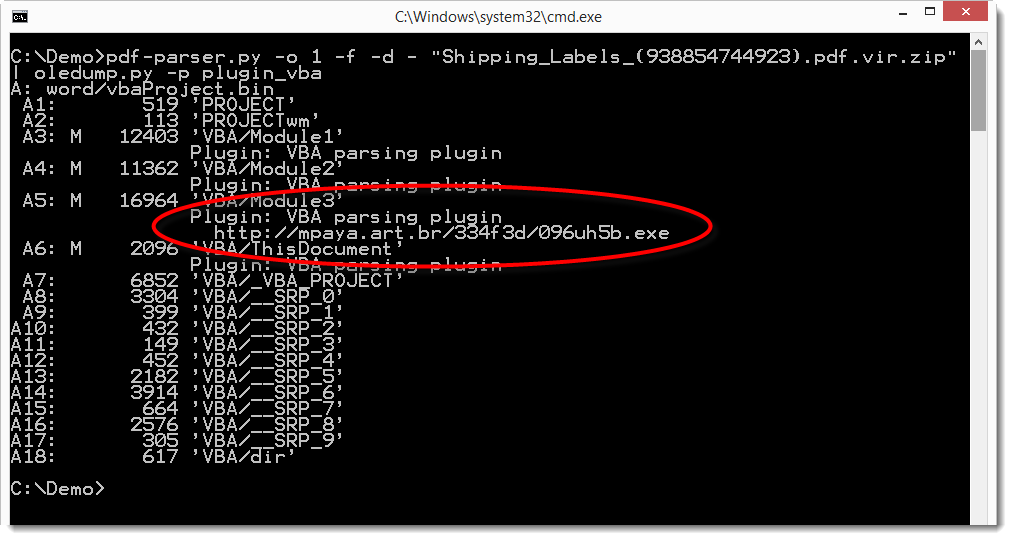
The .docm file format indicates that it is a MS Office Word document with VBA macros. We can extract it and analyze it with oledump. Here we do this with a pipe, e.g. without writing the .docm file to disk. We dump the embedded file to stdout (-d -) and pipe it into oledump which analyses it with the vba plugin.
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com


Comments
Anonymous
Aug 27th 2015
1 decade ago
And you can also block this at the PDF level by disabling JavaScript in Adobe Reader. This blocks it earlier in the kill chain, and many organizations I know are much less impacted by disabling JavaScript in Adobe Reader than disabling macros in MS Office.
We don't make malware available for download, but I shared the hash so that you can look for it on malware analysis sites like malwr.
Anonymous
Aug 27th 2015
1 decade ago