Next up, what's up with TCP port 26?
Whenever I sign up for another shift, if I don't already have a diary topic in mind, I take a look at the top 10 ports in the dashboard when I login to isc.sans.edu. For the last few weeks, I've noticed port 26 showing up, so I decided to see if I could figure out what was going on there.
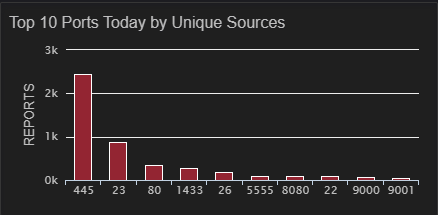
In this case much of the top 10 is stuff to be expected, port 445 is perpetually near or at the top of this chart (please don't leave it open to the internet), port 23 has been there since Mirai first hit more than 3 years ago, 80 and 8080 are web servers and proxies, port 22 (ssh) is not at all unusual, port 5555 is the Android Debug Bridge which has been popular for a few months, but that port 26 just is really strange and it is sitting at number 5. So, let's take a look at the last year of port 26 traffic and see what we can see.
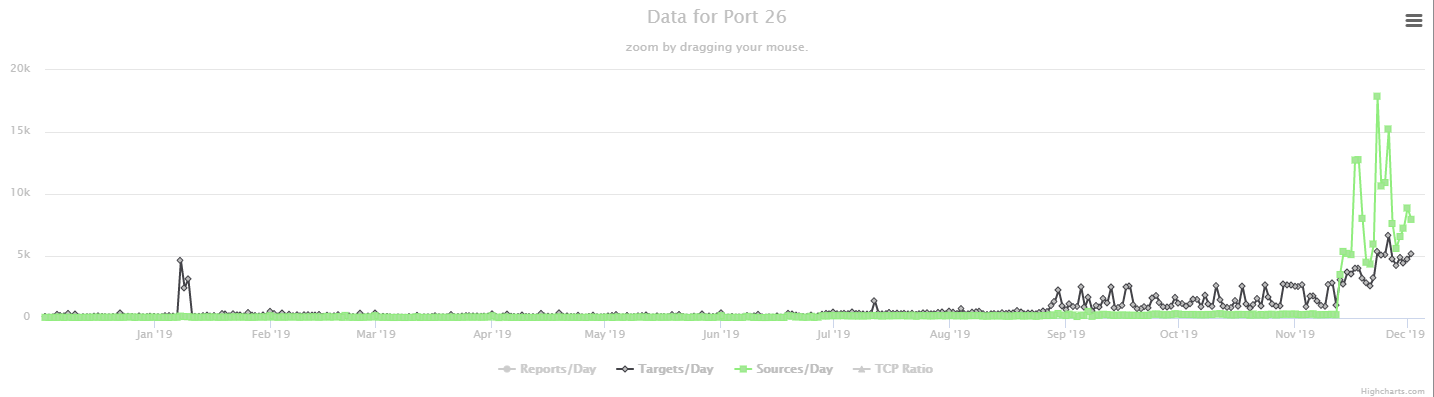 Okay, with the exception of a brief spike in targets last January, there was hardly any traffic on port 26 until September and even then, the number of sources was very small until about the second week of November. So what are they looking for? Well, there is no service officially assigned that port by IANA, so my next thought was to take a look at Shodan and see, what tends to be running there. A quick look there suggests that port 26 is most often used as an alternate SMTP port.
Okay, with the exception of a brief spike in targets last January, there was hardly any traffic on port 26 until September and even then, the number of sources was very small until about the second week of November. So what are they looking for? Well, there is no service officially assigned that port by IANA, so my next thought was to take a look at Shodan and see, what tends to be running there. A quick look there suggests that port 26 is most often used as an alternate SMTP port.
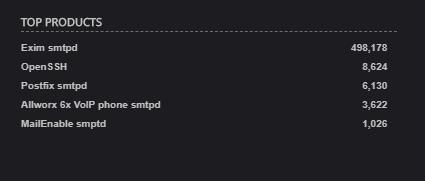
Okay, I suppose there might be reasons for that, you often find web servers running on port 81, so why not SMTP on port 26? In fact, most often it is Exim which has had a couple of vulnerabilities lately. Most recently, a remote code execution vulnerability in September. So, maybe the attackers are looking for vulnerable Exim servers. Now that I have an hypothesis, it is time to test it. A few weeks ago, when I noticed the increase in traffic on port 853, I wasn't able to setup a honeypot before my shift to try to capture some of the traffic, but this time, since I actually noticed this several weeks ago and signed up for the shift last week, I figured I should actually capture some of the traffic to test my hypothesis. I decided to try out fellow handler, Didier Steven's tcp-honeypot (something I've been meaning to play with for months). So, I set it up on a couple of VPSen that I have scattered around and... things didn't work. So, I talked to Didier and discovered that despite the comments in the code to the contrary, the version currently in github (as of 30 Dec 2019 anyway) did not, in fact, work with Python 3. Oops, he'll get that straightened out shortly. Fortunately, it worked with Python 2 (>= 2.7.12, anyway, didn't seem to work with 2.7.8). Okay, that allowed me to fire up several honeypots scattered around where I figured they would get scanned. I copied the config for port 25 and modified it to send back the Exim banners that I saw on Shodan, like these
.png)
And... I didn't get (much) SMTP scanning. In fact, I got exactly 1 SMTP probe, 2 SSH probes (from the connection string, it looks like python scripts using paramiko) and lots and lots of apparent telnet connections (IPs obscured to protect the guilty).
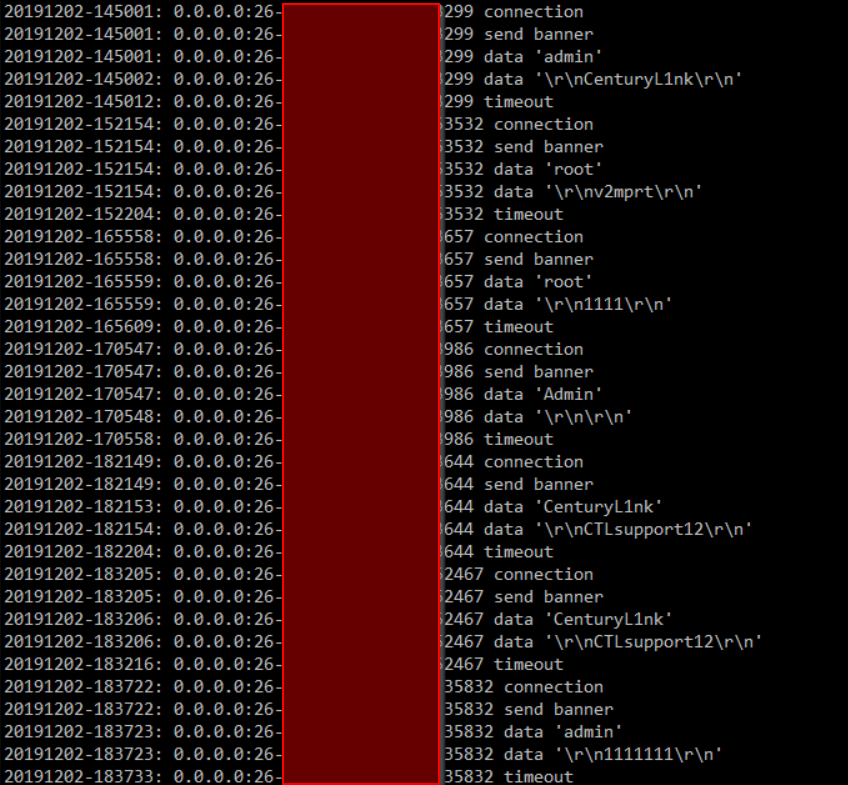
I'm not sure what this tells us. There must be some devices out there that are running telnet (or similar) on port 26 because there is a whole lot of scanning and brute force password guessing going on there, but apparently it isn't attempting to take advantage of and Exim RCE vulnerabilities. If any of our dear readers know what they are actually looking for, I'd love to hear about it, you can let us know in the comments below, via e-mail, or via our contact page, Now that I see it is apparently telnet, I'm very tempted to put up a cowrie instance and see what they do once they get in, but I'll save that for a weekend where I don't have other stuff going on.
---------------
Jim Clausing, GIAC GSE #26
jclausing --at-- isc [dot] sans (dot) edu
| Reverse-Engineering Malware: Malware Analysis Tools and Techniques | Online | Japan Standard Time | Mar 9th - Mar 14th 2026 |


Comments
https://twitter.com/adulau/status/1199971233154174976
It's most probably the management port of a vulnerable device running Telnet/SSH on that port instead of default ports.
Anonymous
Dec 2nd 2019
6 years ago
Anonymous
Dec 2nd 2019
6 years ago
> Proxmox Mail Gateway Administration Guide
> pmg.proxmox.com ? pmg-docs ? pmg-admin-guide
>
> Configure your e-mail server to send all outgoing messages through your
> Proxmox Mail Gateway (Smart Host, port 26 by default)
Anonymous
Dec 9th 2019
6 years ago
Anonymous
Dec 9th 2019
6 years ago