Malspam pushing Trickbot gtag rob13
Introduction
Trickbot malware has been a relatively constant presence in the cyber threat landscape so far this year. We've seen activity continue this week, and today's diary reviews an infection I generated on Wednesday 2021-02-17.
The infection chain of events:
The email
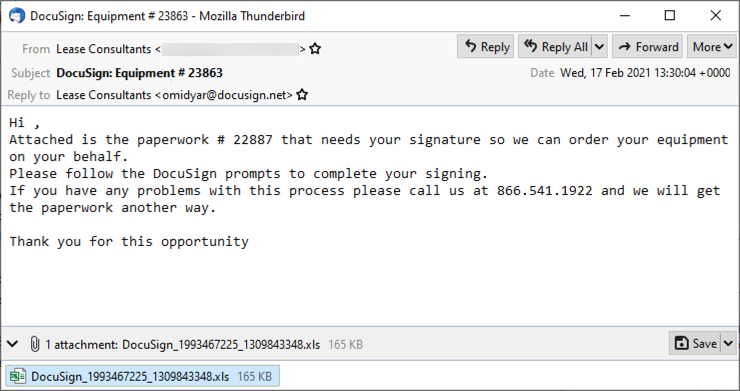
Shown above: Screenshot from an example of malspam seen earlier today (Wednesday 2021-02-17).
The spreadsheet
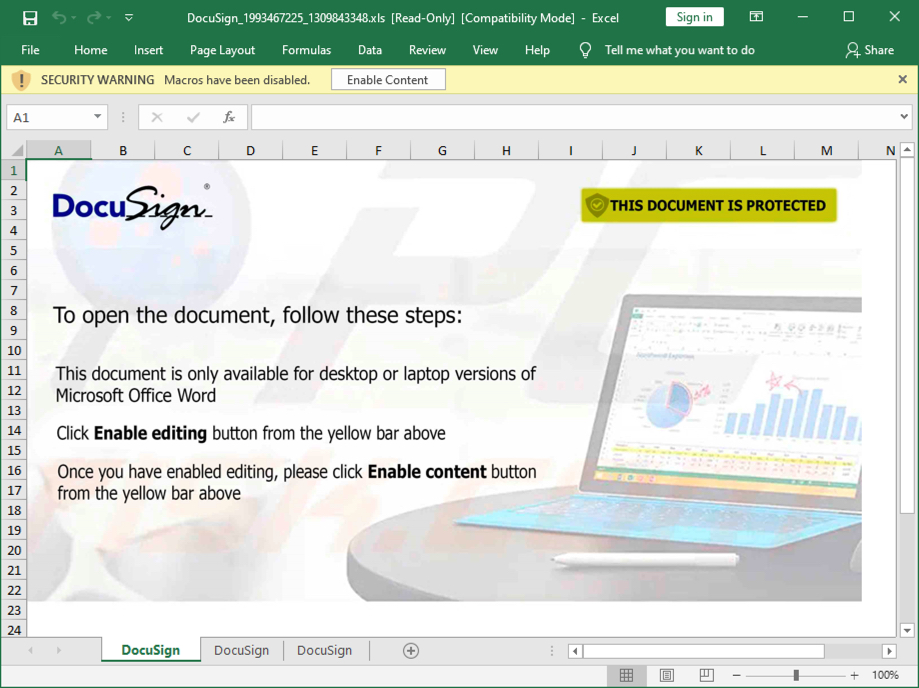
Shown above: Screenshot of the attached Excel spreadsheet with macros for Trickbot.
Infection traffic
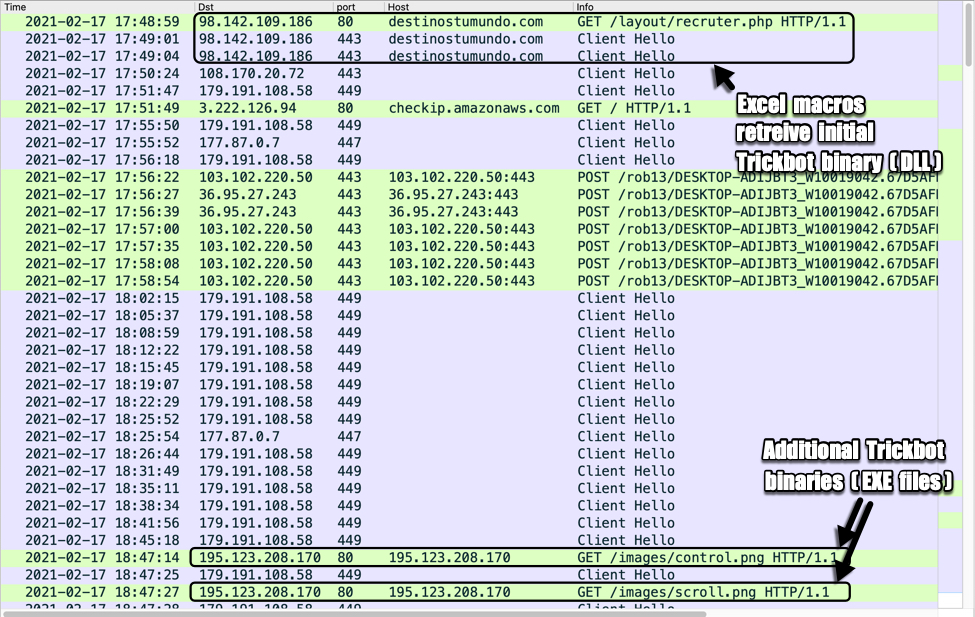
Shown above: Traffic from an infection filtered in Wireshark.
Forensics on an infected Windows host
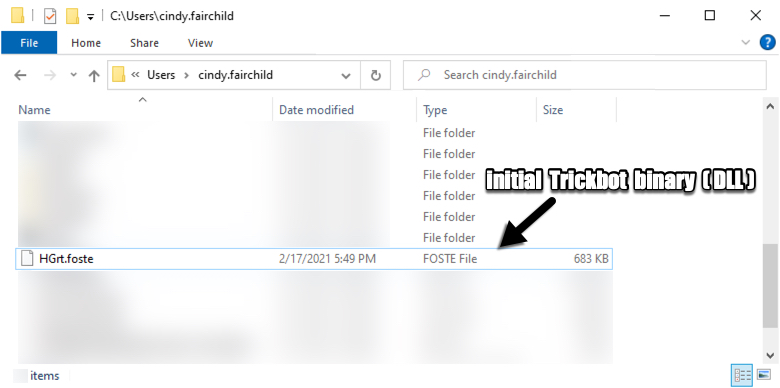
Shown above: Initial Trickbot binary retrieved by the Excel macro.
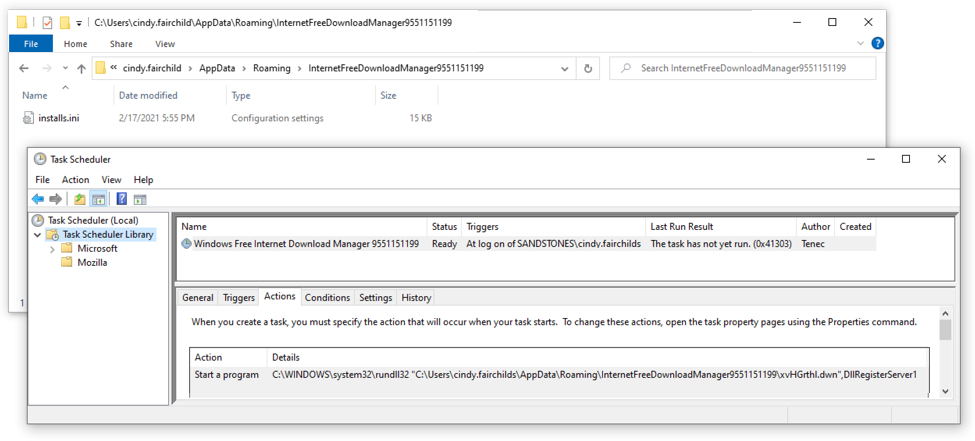
Shown above: Scheduled task for Trickbot.
In the above image (double-click on it to get a higher-resolution picture), you can see the Trickbot DLL is not where the scheduled task points to. When I restarted the infected host, it gave me an error saying it couldn't run the task. I've noticed this during the past several months from Trickbot infections that use a DLL file as the initial binary. Unfortunately, I don't know why this happens.
Indicators of Compromise (IOCs)
EXAMPLES OF SUBJECT LINES AND REPLY-TO ADDRESSES:
- Subject: DocuSign: Equipment # 1332
- Subject: DocuSign: Equipment # 9448
- Subject: DocuSign: Equipment # 9722
- Subject: DocuSign: Equipment # 12169
- Subject: DocuSign: Equipment # 23863
- Reply-To: Lease Consultants <[email protected]>
- Reply-To: Lease Consultants <[email protected]>
- Reply-To: Lease Consultants <[email protected]>
- Reply-To: Lease Consultants <[email protected]>
- Reply-To: Lease Consultants <[email protected]>
- Note: Sending addresses may have been from email accounts that were compromised.
FILE HASHES FROM ATTACHMENTS SUBMITTED TO VIRUSTOTAL:
393bc60e292c3e24ab70c459ba1c595daaae68df94a75ebe571d3e75a0fe8109 DocuSign_484590053_1220881832.xls
64392b7c699791e4dddde1a1754d157c284dcc4d54e9cb8974ea661f6443ce86 DocuSign_463828509_1320623172.xls
713a539daad692c8e284718ad73c128128e8257b3c41b233d2f810717df873b7 DocuSign_2026401106_1090792446.xls
99316adbb0514f099d44bf8655486c2332eb5f3f821b80b2c0a6a85b652312e6 DocuSign_649568847_1582762946.xls
9bf4196e8fb7c4ac3be72f79f13697656145ee1cc93bb7c7a31d93ea75bbcae3 DocuSign_1264755469_604175183.xls
9fbbb8b4025b2e46429594b946d2ba74ce381e4c2968966e9a65ffd81791baa1 DocuSign_1283716068_336411873.xls
bc033032b6d2afcea2a07f4b5eb5de3137c9fc83c1302fe28a781137168884eb DocuSign_1993467225_1309843348.xls
bc47683422d0021b2b27b551d81058213fa4d000c544b617adf1bb7b94d5f4a9 DocuSign_558551337_1625623689.xls
f391892523950617f98dd08c5e1e8ffa58f8985f7527d5ffe735944db72a312f DocuSign_1237489607_947076939.xls
MALWARE FROM AN INFECTED WINDOWS HOST:
SHA256 hash: bc033032b6d2afcea2a07f4b5eb5de3137c9fc83c1302fe28a781137168884eb
- File size: 168,960 bytes
- File name: DocuSign_1993467225_1309843348.xls
- File description: Excel spreadsheet with macros for Trickbot gtag rob13
SHA256 hash: e1b67bd8b15bcd422fcbc74fa3b691c40c527ffedc951a6bb8e67ca257240d16
- File size: 698,880 bytes
- File location: hxxps://destinostumundo[.]com/layout/recruter.php
- File location: C:\Users\[username]\HGrt.foste
- File description: Initial Trickbot gtag rob13 binary (DLL file)
- Run method: rundll32.exe [file name],DllRegisterServer1
SHA256 hash: 24bd33f4ba457d77d796620a2cd4b7a3e38d63e2286fec752d898ab7c5204e4b
- File size: 864,256 bytes
- File location: hxxp://195.123.208[.]170/images/control.png
- File description: Follow-up Trickbot EXE file, gtag tot43
SHA256 hash: f0391039f888fb30566295365420868ac8539075e25a690ac4400a8bb91eb803
- File size: 864,256 bytes
- File location: hxxp://195.123.208[.]170/images/scroll.png
- File description: Follow-up Trickbot EXE file, gtag lib43
TRAFFIC TO RETRIEVE THE INITIAL TRICKBOT BINARY (A DLL FILE):
- 98.142.109[.]186 port 80 - destinostumundo[.]com - GET /layout/recruter.php
- 98.142.109[.]186 port 443 (HTTPS) - destinostumundo[.]com - GET /layout/recruter.php
POST-INFECTION TRAFFIC FOR TRICKBOT:
- 108.170.20[.]72 port 443 - HTTPS traffic
- 179.191.108[.]58 port 449 - HTTPS traffic
- port 80 - checkip.amazonaws.com - GET /
- 177.87.0[.]7 port 447 - HTTPS traffic
- 103.102.220[.]50 port 443 - 103.102.220[.]50:443 - POST /rob13/[string with host and infection info]/81/
- 36.95.27[.]243 port 443 - 36.95.27[.]243:443 - POST /rob13/[string with host and infection info]/81/
- 103.102.220[.]50 port 443 - 103.102.220[.]50:443 - POST /rob13/[string with host and infection info]/83/
- 36.95.27[.]243 port 443 - 36.95.27[.]243:443 - POST /rob13/[string with host and infection info]/90
TRAFFIC CAUSED BY TRICKBOT'S PROPAGATION MODULES TO RETRIEVE ADDITIONAL TRICKBOT BINARIES (RETURNED EXE FILES):
- 195.123.208[.]170 port 80 - 195.123.208[.]170 - GET /images/control.png
- 195.123.208[.]170 port 80 - 195.123.208[.]170 - GET /images/scroll.png
ATTEMPTED TCP CONNECTIONS CAUSED BY THE INFECTED WINDOWS HOST:
- 45.14.226[.]115 port 443
- 169.239.45[.]42 port 449
- 92.242.214[.]203 port 449
- 94.158.245[.]54 port 443
- 38.132.99[.]174 port 80
Final words
A pcap of the infection traffic and the associated malware can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments