Malicious Excel Sheet with a NULL VT Score: More Info
The maldoc Xavier mentioned in diary entry "Malicious Excel Sheet with a NULL VT Score" is indeed corrupt, and that explains its low score on VT. I believe this maldoc has been cleaned by an anti-virus program: (incomplete) deletion of VBA modules.
If we take a look with oledump.py, we see some streams related to VBA, but the module streams are missing (they contain the compressed VBA code):
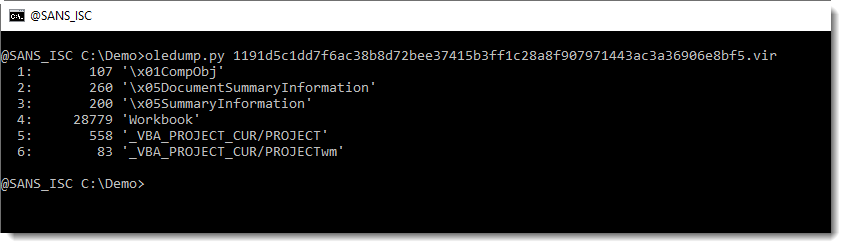
Stream PROJECT contains pure text like an INI file:
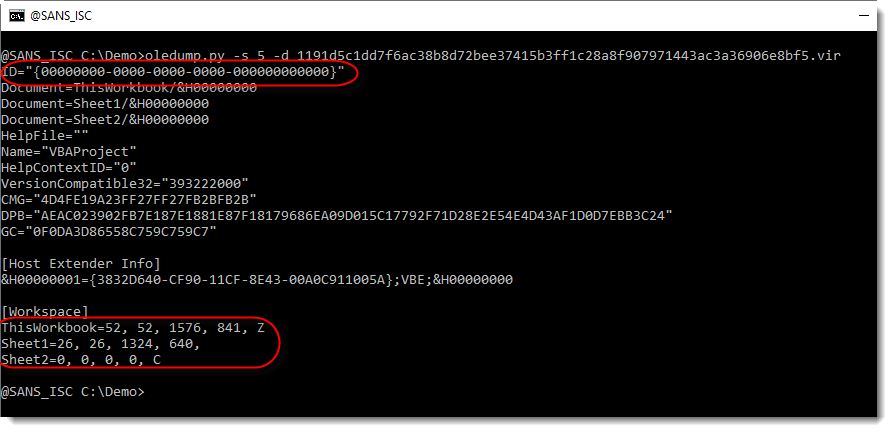
From the [Workspace] section, we can see that there are 3 module stream (ThisWorkbook, Sheet1 and Sheet2) open in the VBA IDE. These are missing in the ole file.
Remark also that the ID is a zero guid: this means that the VBA project is password protected:
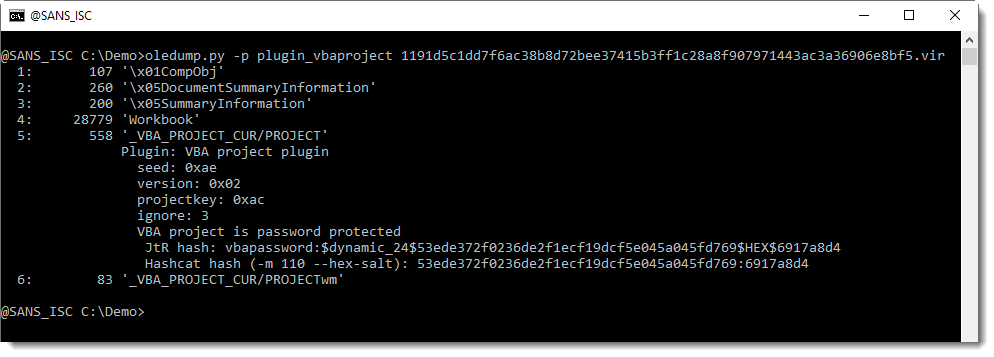
FYI: I was not able to crack the password using JtR and the Rockyou password list.
If we take a look with oledir (by @decalage2), we see that some streams have been deleted:
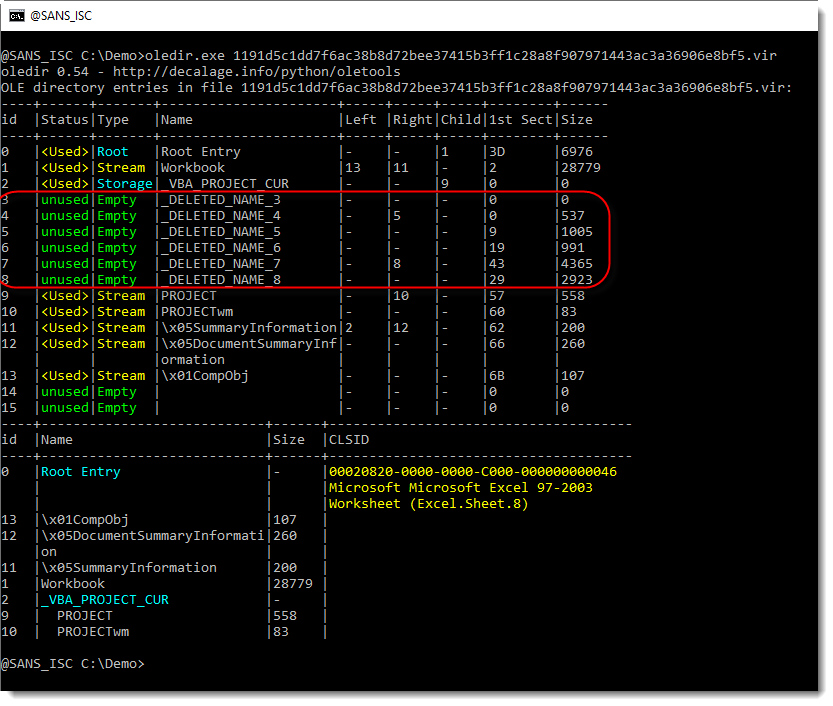
The streams have been deleted: freed (unused) and the name of the stream overwritten by _DELETED_NAME_*. But the size of the streams is not zero: there is a chance that the sectors that contain the stream content are still present (that the content is not erased).
To check this, I search for string Attribut (a normal module stream contains compressed VBA code that contains the string Attribut in the initial bytes):
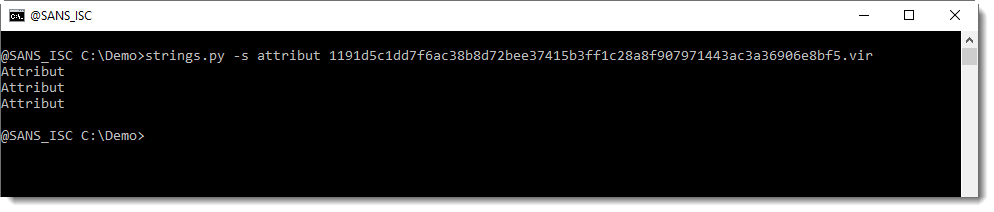
This string is indeed present, and even 3 times: exactly the same as the number of module streams we found mentioned in the PROJECT stream.
For such cases (ole files that contain VBA code that is not accessible through streams) I have option --raw in oledump. Option --raw allows you to read any file type (it doesn't get parsed like an ole file would) and then you can use option -v to search for compressed VBA code anywhere inside the file, like this:
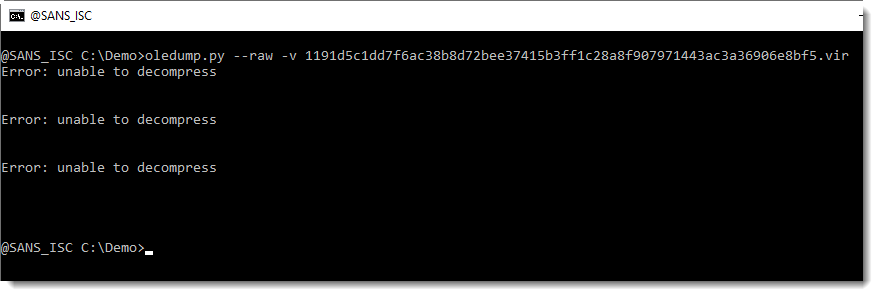
This looks promising: this means that oledump.py found 3 instances of compressed VBA code, but that it was not able to decompress the VBA code without errors. As you might guess, oledump has another option to deal with this: --vbadecompresscorrupt.
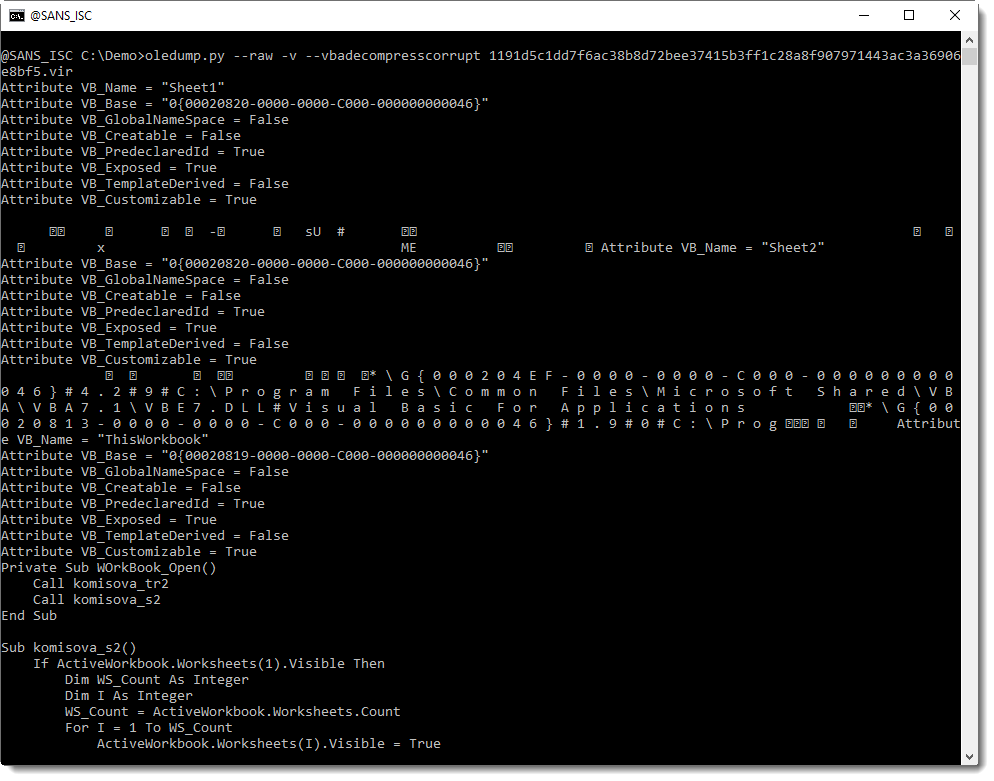
Here is the result:
.png)
And finally, we see VBA code.
It is indeed malicious: running two commands, one PowerShell and one schtasks.
Please post a comment if you know which antivirus product cleans Office documents with malicious VBA code by deleting module streams and overwriting their stream name with _DELETED_NAME_*.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com



Comments
But 2 questions/comment
1. What are the prerequests for --raw -v --vbsdecompresscorrupt
My trial did not give any resullt
2. This worked for me, but there was no url
python3 oledump.py Virus/xls/1191d5c1dd7f6ac38b8d72bee37415b3ff1c28a8f907971443ac3a36906e8bf5.zip -p plugin_biff.py
Anonymous
Aug 30th 2020
4 years ago