Maldoc: Payloads in User Forms
When malicious Office documents leveraging VBA code became popular again with malware authors, they soon started to look for different places to hide their payload (URLs, commands, shellcode, EXEs, ...). User Forms were one of the first components they turned to.
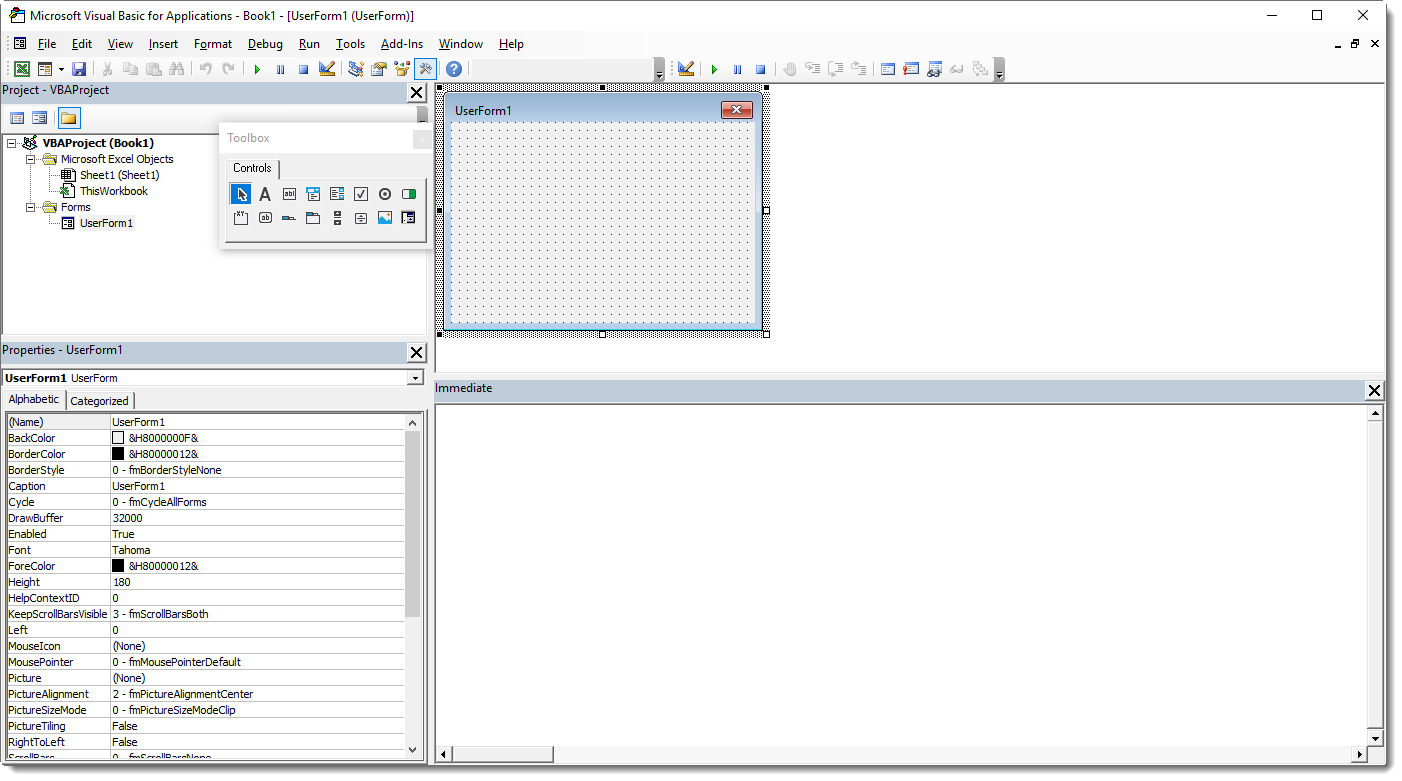
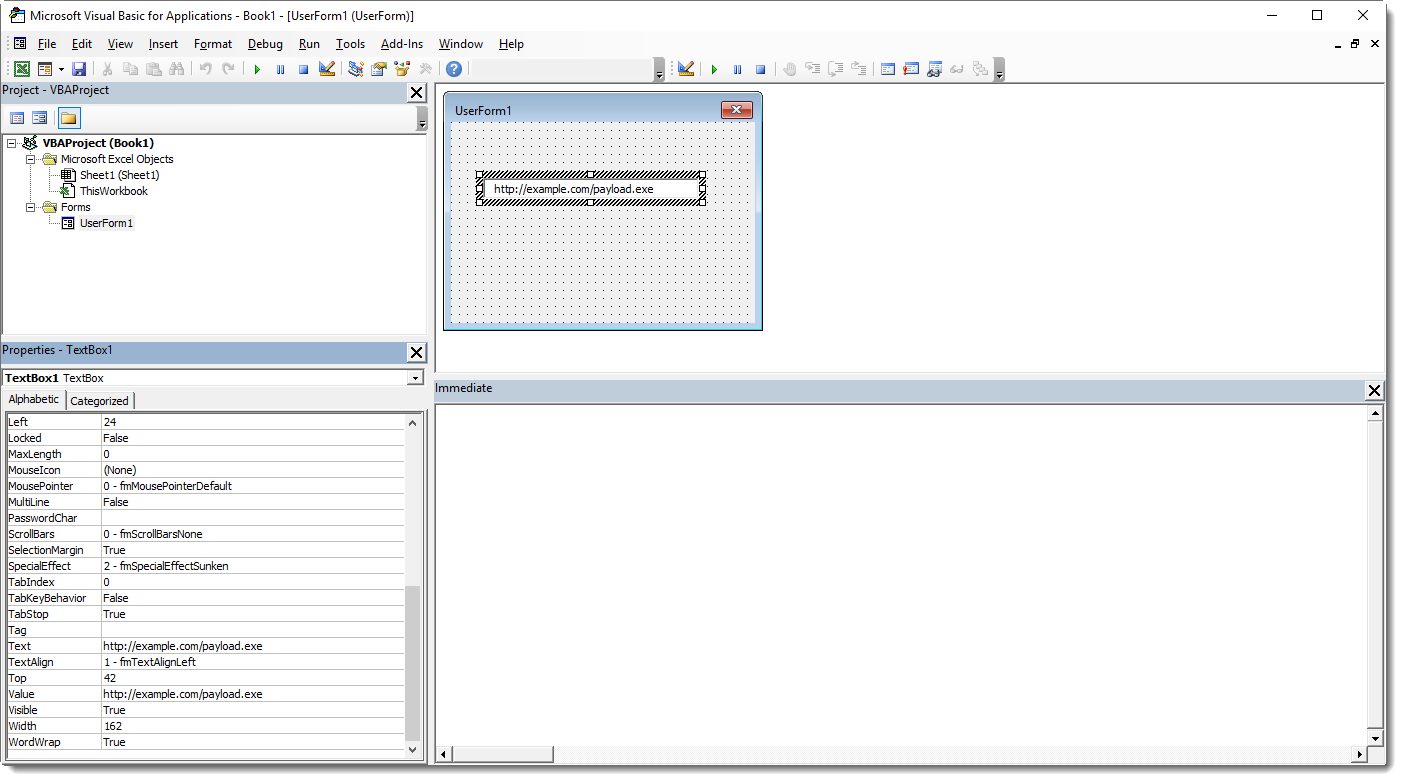
In this example, I add a user form (UserForm1) with a text box (TextBox1). And I "hide" a URL inside the text box.
This results in 4 extra streams under storage UserForm1. Here is the output of oledump.py:
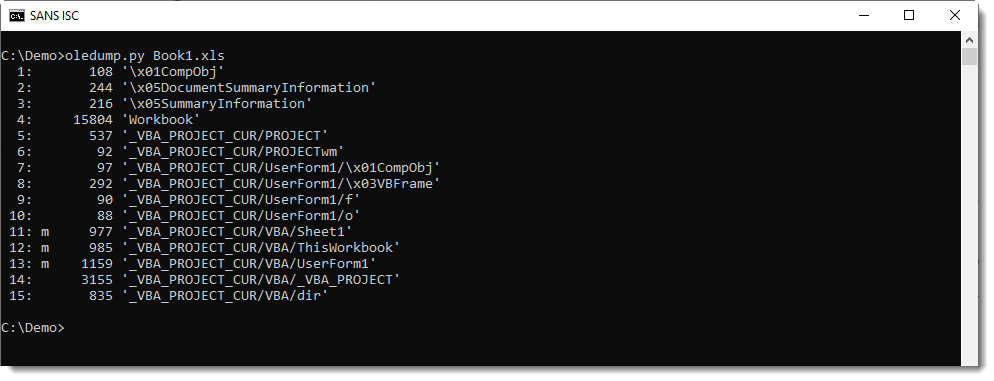
Here is the content of these streams:
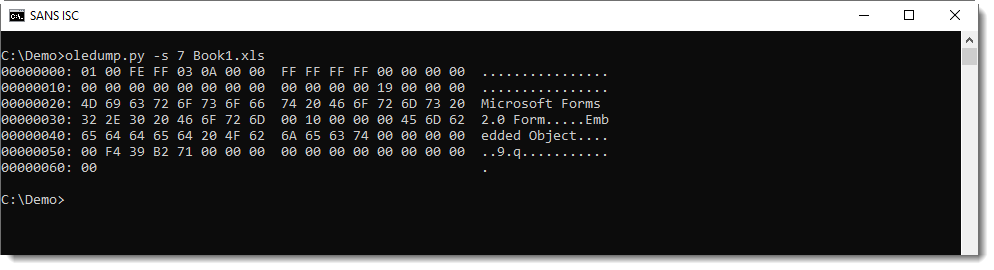
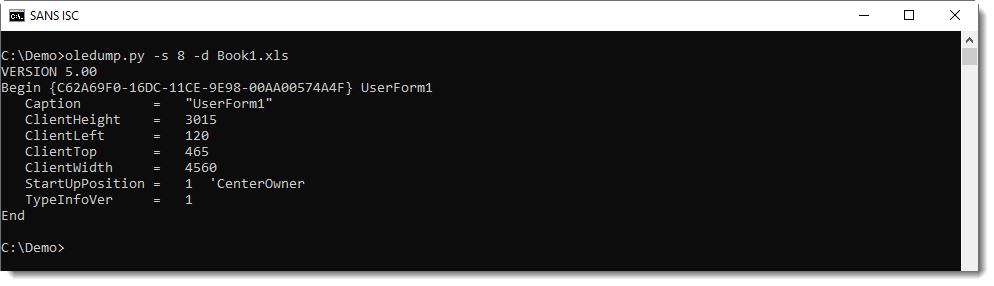
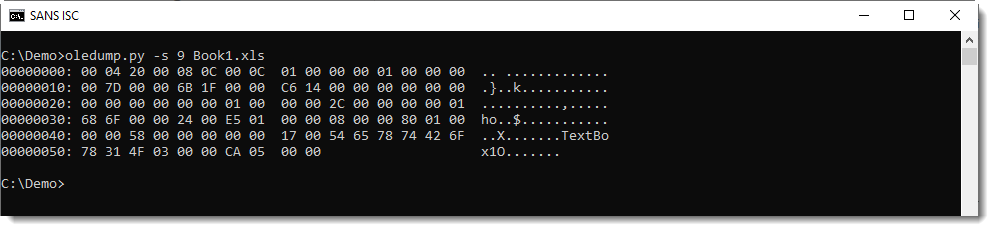
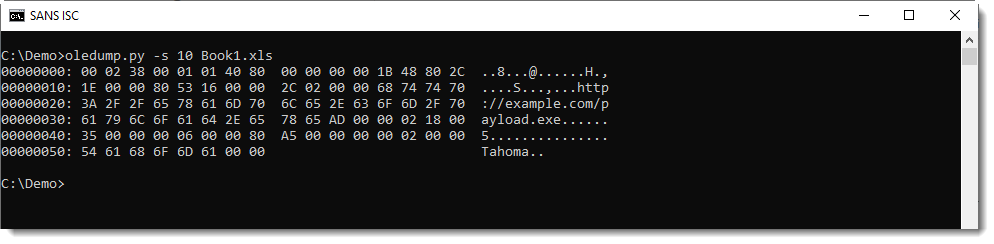
When you take a close look, you'll notice that stream f contains the names of the components (TextBox1) and stream o contains the property values (the URL in our case).
Plugin plugin_stream_o can extract values of textboxes:
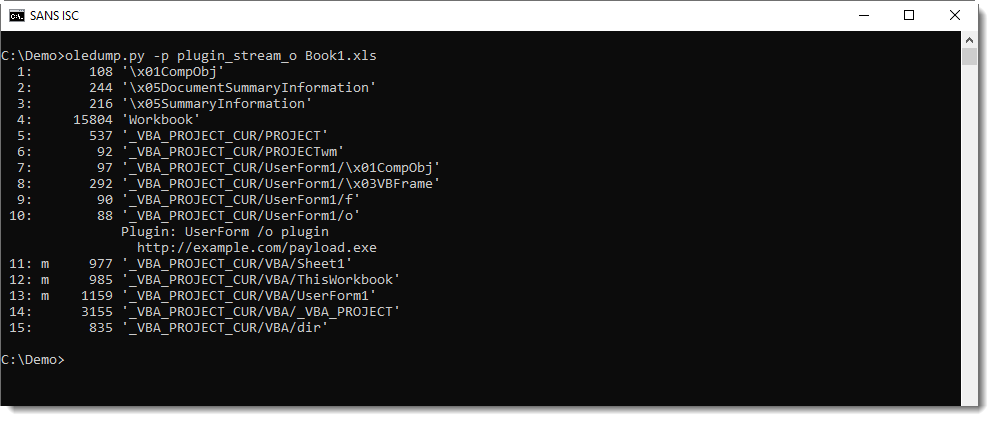
When you encounter optional streams in Office documents, make sure to take a look inside: they might contain payloads.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com


Comments