Macros? Really?!
Yes indeed! While the past 15 years or so were mostly devoid of any significant macro viruses, macro-based malware is now making a "successful" comeback. Last week, we saw a significant Dridex malware run that was using macros in Excel files (.XLSM), and earlier this week, the crooks behind the banking spyware "Vawtraq" started to spam the usual "Fedex Package" and "Tax Refund" emails, but unlike in other malspam runs, the attachment was no longer a ZIP with an EXE or SCR inside, but rather a file in Microsoft Office .DOC format. File extension based blocking on the email gateway is not going to save your bacon on this one!
For Vawtraq, if the recipient opens the DOC, the content looks garbled, and the only readable portion is in (apparently) user-convincing red font, asking the recipient to enable macros. You can guess what happens next if the user falls for it...: A VBS and Powershell file get extracted from the DOC, and then download and run the Vawtraq malware executable. The whole mess has very low detection in anti-virus, yesterday's Vawtraq started with zero hits on VirusTotal, and even today, one day later, it hasn't made it past 7/52 anti-virus engines detecting the threat yet. Thus, odds are you will need to revert to manual analysis to determine if a suspicious Office document is indeed malicious, and to extract any indicators from it that can help to discover users on your network who have been "had".
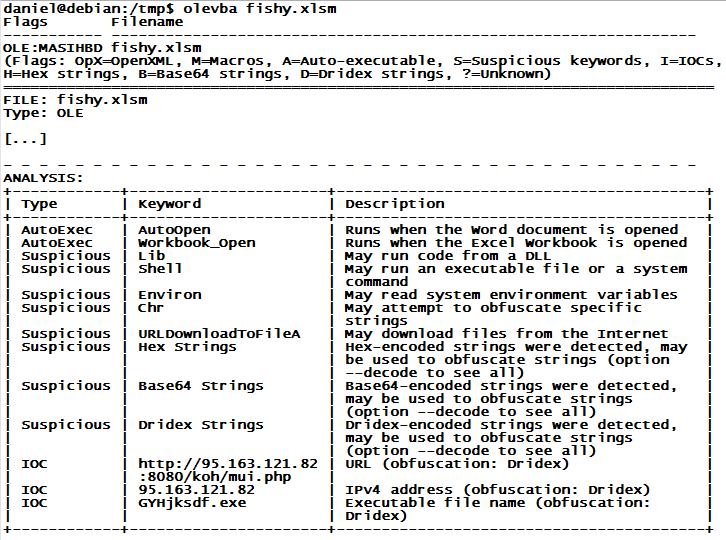
Besides Didier Stevens' "oledump" that we covered last month, my favorite toolkit for this analysis is the python-oletools package by Philippe Lagadec. "olevba" in particular does a great job at parsing out all the obfuscated code, and is often even able to extract actionable indicators of compromise (IOC), like URLs and IP addresses. The example below is an abbreviated "olevba" analysis of a recent Dridex run, and it nicely shows how the next stage URL and EXE name are pulled out in one quick swoop. Give it a try!


Comments
Extraction is sufficient for these scripts to run?
REALLY?
Here[tm] (and there too) are *.VB{S,E} and *.PS1 stored outside of secure locations like %ProgramFiles% and %SystemRoot% blacklisted per Software Restriction Policies and wont run at all!
Anonymous
Feb 19th 2015
1 decade ago
Anonymous
Feb 19th 2015
1 decade ago
I have found some that simply call a file from an IP or URL with some name of file.php or something to throw you off, and as it downloads the file it stores it and renames it to an exe or bat or ps1, or whatever it likes.
Sometimes the Word Doc, Excel Spreadsheet, etc, will create a .bat, .ps1, .vbs in the TEMP directory.
I have going through the code and all the VBS does is create those files based on the OS. If you are running XP/Vista or older create and run the .bat or .vbs. If you are running 7 or newer then create and run the .ps1 file.
There is a bunch of interesting things about these macro enabled documents and I have been researching a way to stop them.
If anyone wants to more about my findings, feel free to reach out to me.
I have yet to test this, but I am thinking to prevent users from simply executing the macros, one needs to Disable Macros Without Notification.
Interesting!
Anonymous
Feb 23rd 2015
1 decade ago