June 2021 Forensic Contest: Answers and Analysis
Introduction
Thanks to everyone who participated in our June 2021 forensic contest originally posted two weeks ago. We received 10 submissions through our contact page, and four people found all three infections in the pcap. Unfortunately, we could only pick one winner. In this case, our winner was chosen through a random process among the four eligible people. Join us in congratulating this month's winner, Dimitri! Dimitri will receive a Raspberry Pi 4 kit.
You can still find the pcap for our June 2021 forensic contest here.
Answers
Three infected Windows clients show signs of infection within the Active Directory (AD) environment from the packet capture (pcap). The infected Windows hosts are:
- IP address: 10.6.15.93
- MAC address: 00:23:54:a2:1f:b4
- Host name: DEKSTOP-A1CTJVY
- User account: raquel.anderson
- Infected with: AgentTesla
- Date/Time of infection activity: 2021-06-16 15:44 UTC
- IP address: 10.6.15.119
- MAC address: 00:23:54:e3:a3:55
- Host name: DESKTOP-NIEE9LP
- User account: tommy.vega
- Infected with: Hancitor, Cobalt Strike, and Ficker Stealer
- Date/Time of infection activity: 2021-06-16 14:37 UTC
- Note: Malicious Word doc was sent through ststephenskisugu[.]church at 14:35 UTC
- IP address: 10.6.15.187
- MAC address: 00:23:54:72:c9:13
- Host name: DESKTOP-YS6FZ2G
- User account: horace.maddox
- Infected with: Qakbot (Qbot)
- Date/Time of infection activity: 2021-06-16 15:37 UTC
- Note: Malicious zip archive was sent through solarwindsonline[.]com at 15:30 UTC
To help in your analysis of this activity, please review the Requirements section in our original diary for this month's contest.
Creating Pcaps for Individual Hosts
As stated in our original post, the infected Windows hosts are part of an AD environment, and its characteristics are:
- LAN segment range: 10.6.15.0/24 (10.6.15.0 through 10.6.15.255)
- Domain: saltmobsters.com
- Domain Controller: 10.6.15.5 - Saltmobsters-DC
- LAN segment gateway: 10.6.15.1
- LAN segment broadcast address: 10.6.15.255
To find IP addresses for Windows clients in this AD environment, use Statsistics --> Endpoints to bring up Wireshark's Endpoints window.
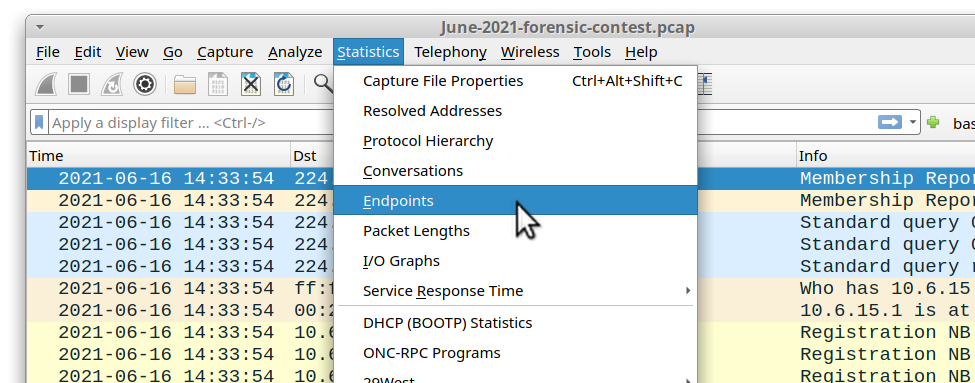
Shown above: Getting to the Endpoints window in Wireshark.
The Endpoints window shows all endpoints in the pcap. Click on the IPv4 tab and sort by address to find IP addresses in the 10.6.15.0/24 range.
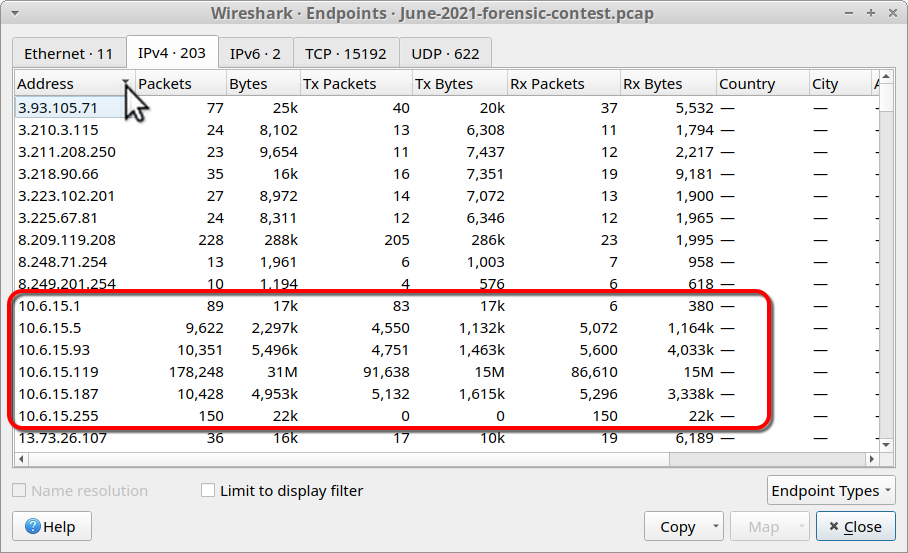
Shown above: Sorting by Address under the IPv4 tab and finding the 10.6.15.0/24 addresses.
This should reveal six internal IP addresses within the 10.6.15.0/24 LAN segment ior saltmobsters.com:
- 10.6.15.1 (gateway)
- 10.6.15.5 (Domain controller, Saltmobsters-DC)
- 10.6.15.93
- 10.6.15.119
- 10.6.15.187
- 10.6.15.255 (broadcast address)
10.6.15.1, 10.6.15.5, and 10.6.15.255 are already accounted for, we should filter on each of the three remaining IP addresses and export traffic for each one into a separate pcap.
First, filter on ip.addr eq 10.6.15.93 then use File --> Export Specified Packets... to save the displayed traffic in a new pcap as shown below.
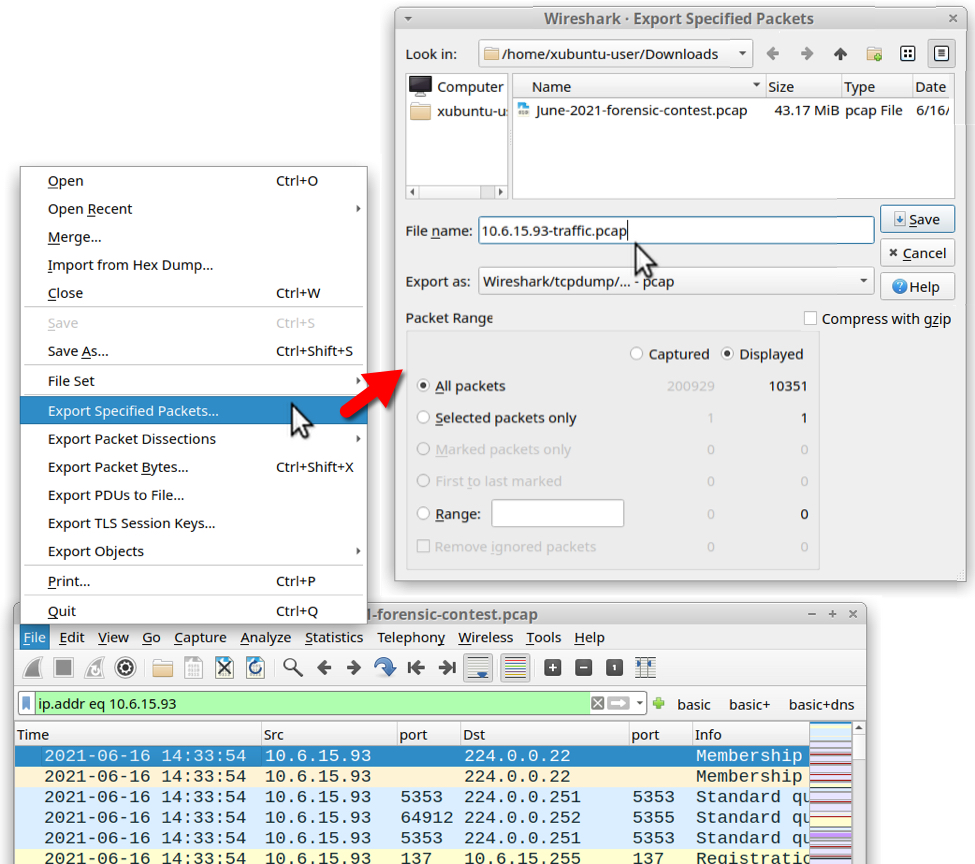
Shown above: Filtering on 10.6.15.93 and saving the traffic to a new pcap.
Do the same thing for 10.6.15.119 and 10.6.15.187. Now you should have three new pcaps that contain traffic from each of the Windows clients.
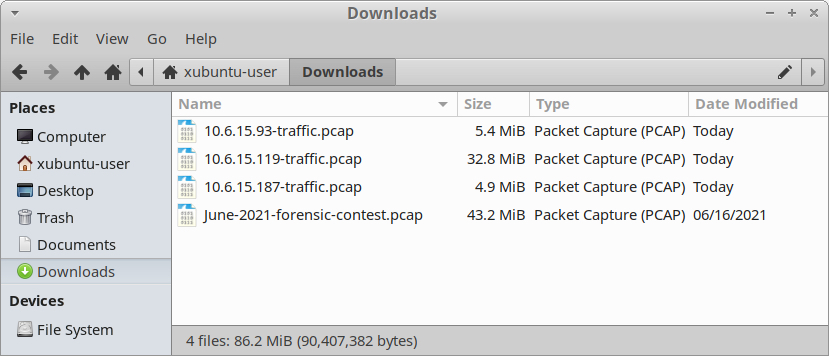
Shown above: Three pcaps from Windows clients extracted from the June 2021 contest pcap.
Infection Traffic for Agent Tesla (AgentTesla)
Let's review traffic from 10.6.15.93. We can quickly determine host information by filtering on Kerberos.CNameString and viewing a customized column for CNameString as described in this tutorial. The host information is:
- IP address: 10.6.15.93
- MAC address: 00:23:54:a2:1f:b4
- Host name: DEKSTOP-A1CTJVY
- User account name: raquel.anderson
You can find host information for the other two IP addresses using this method. Note: When setting up this environment, I misspelled DESKTOP in the host name for DEKSTOP-A1CTJVY.
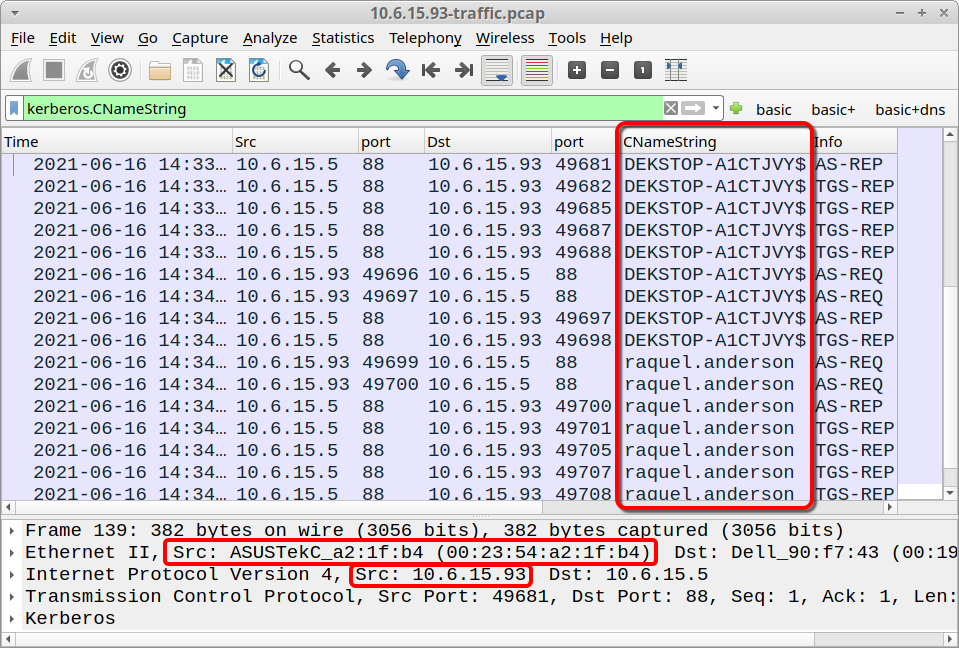
Shown above: Host information for 10.6.15.93.
There's nothing unusual in web traffic from 10.6.15.93, except for a dns query to turtleoil1998b[.]com that resolves to 45.142.212[.]61, but no TCP connection is established with that IP. This traffic is related to the TA551 (Shathak) campaign, and it was pushing Ursnif (Gozi/ISFB) during this timeframe. My personal research has confirmed turtleoil1998b[.]com was a domain used by TA551 to host malware DLL files for Ursnif on 2021-06-16.
Despite a lack of interesting web traffic, 10.6.15.93 generated unusual SMTP activity. Filter on smtp, and the display will show unencrypted SMTP traffic over TCP port 587 to an external IP address. This is not normal activity from a Windows client.
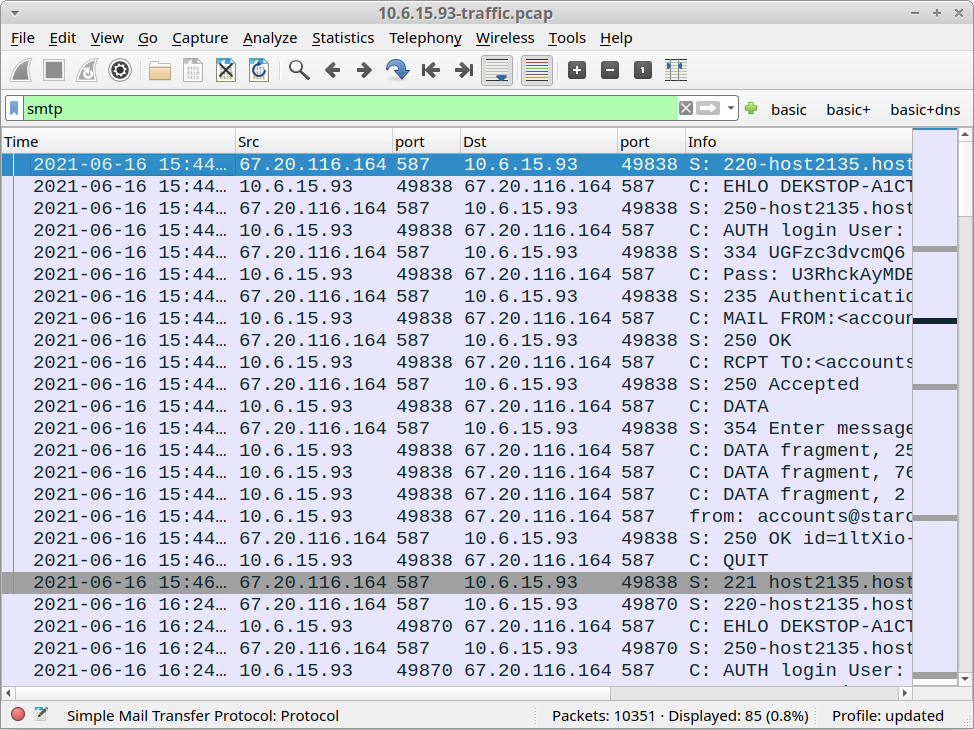
Shown above: SMTP traffic seen from 10.6.15.93.
Follow the TCP stream for any of the first few frames in the SMTP results. Your TCP stream should reveal an email to [email protected] with usernames and passwords from the Windows host. This is definitely malicious traffic.
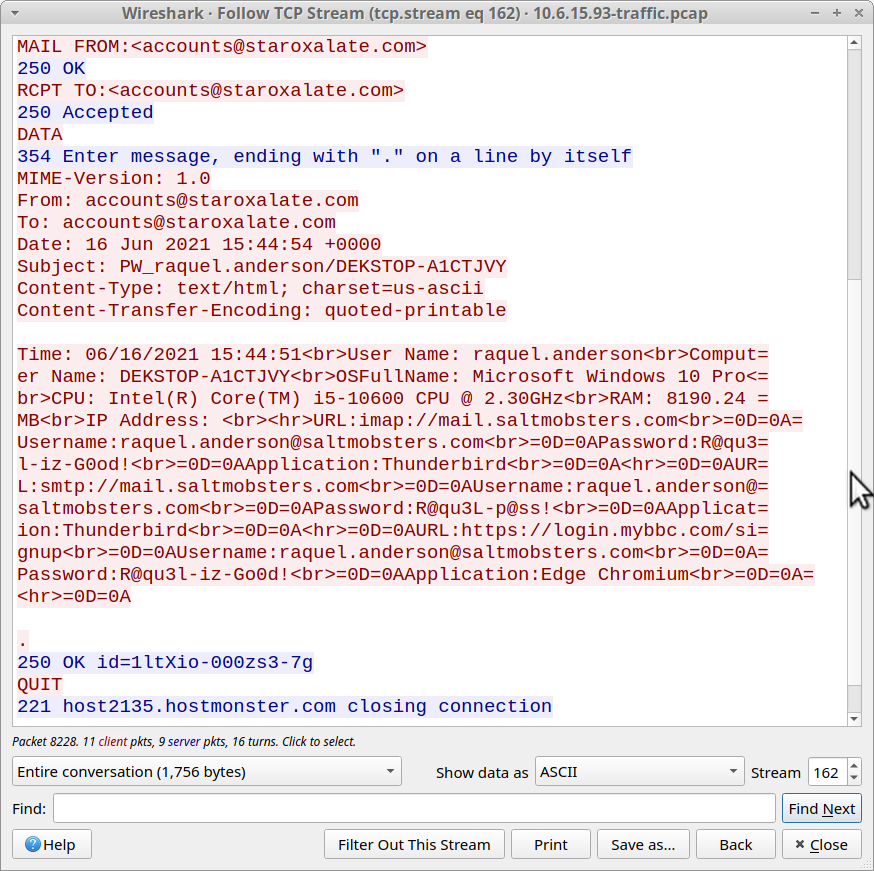
Shown above: TCP stream of unencrypted SMTP traffic with info from the infected host.
This activity matches what I've seen for AgentTesla malware. It triggered an alert for AgentTesla-generated SMTP when I tested it in my lab environment.

Shown above: EmergingThreats (ET) alert for AgentTesla.
The infected Windows host at 10.6.15.93 sent four emails to [email protected].
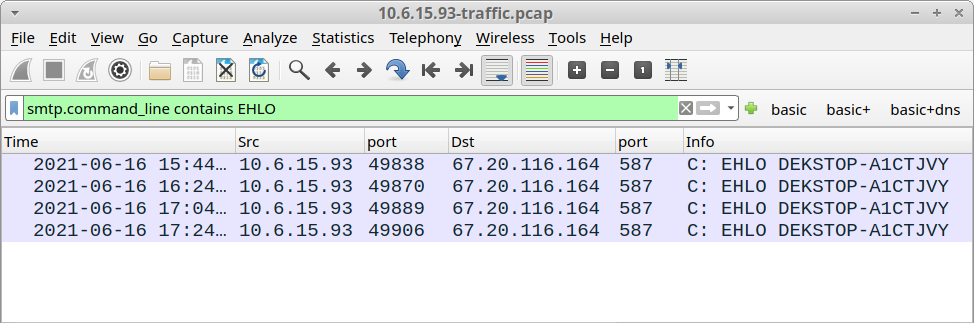
Shown above: Four different emails sent from 10.6.15.93.
The first message has passwords from the infected Windows host, and its subject line starts with PW. The next three messages have keylogging data, and their subject lines start with KL.
Infection Traffic for Hancitor, Cobalt Strike, and Ficker Stealer
Traffic from 10.6.15.119 fits patterns for Hancitor, Cobalt Strike, and Ficker Stealer as described in this Wireshark Tutorial. In recent weeks, Hancitor has used Google Feedproxy links as the initial URL to kick off an infection chain. The initial Google Feedproxy link in this pcap redirected to a URL from, ststephenskisugu[.]church as part of this infection chain.
Indicators for the remaining activity are listed below.
Hancitor traffic:
- port 80 - api.ipify.org - GET /
- 194.226.60[.]15 port 80 - hadevatjulps[.]com - POST /8/forum.php
Hancitor-infected host retrieves follow-up malware:
- 8.209.119[.]208 port 80 - srand04rf[.]ru - GET /16.bin
- 8.209.119[.]208 port 80 - srand04rf[.]ru - GET /16s.bin
- 8.209.119[.]208 port 80 - srand04rf[.]ru - GET /f7juhkryu4.exe
Cobalt Strike traffic:
- 162.244.83[.]95 port 80 - 162.244.83[.]95 - GET /VOoH
- 162.244.83[.]95 port 443 - 162.244.83[.]95:443 - GET /4Erq
- 65.60.35[.]141 port 80 - 65.60.35[.]141 - GET /pixel
- 65.60.35[.]141 port 443 - 65.60.35[.]141:443 - GET /g.pixel
Ficker Stealer traffic:
- port 80 port api.ipify.org - GET /?format=xml
- 185.66.15[.]228 port 80 - pospvisis[.]com - TCP traffic (not HTTP)
EXE retrieved from the traffic:
- SHA256 hash: dee4bb7d46bbbec6c01dc41349cb8826b27be9a0dcf39816ca8bd6e0a39c2019
- File size: 272,910 bytes
- File location: hxxp://srand04rf[.]ru/f7juhkryu4.exe
- File description: Windows EXE for Ficker Stealer
Infection Traffic for Qakbot (Qbot)
Traffic from 10.6.15.187 fits patterns for Qakbot (Qbot) malware. Indicators are:
- 192.186.204[.]161 port 80 - solarwindsonline[.]com - GET /miss-alicia-abbott/Oliver.Williams-84.zip
- 192.186.204[.]161 port 80 - solarwindsonline[.]com - GET /miss-alicia-abbott/documents.zip
- 103.28.39[.]29 port 443 - khangland[.]pro - HTTPS traffic
- 104.244.121[.]13 port 443 - jaipurbynite[.]com - HTTPS traffic
- 149.28.99[.]97 port 2222 - attempted TCP connections
- 95.77.223[.]148 port 443 - attempted TCP connections
- 207.246.77[.]75 port 2222 - HTTPS/SSL/TLS traffic
The initial URL for solarwindsonline[.]com was reported to URLhaus as returning a zip archive for Qakbot. Unfortunately, due to packet loss in our pcap, we cannot export the zip archive that appears in this traffic.
However, this malware sample is an Excel spreadsheet associated with Qakbot that generates traffic to khangland[.]pro and jaipurbynite[.]com. Tria.ge sandbox analysis of the sample shows it generates the following HTTPS URLs when macros are enabled:
- hxxps://khangland[.]pro/v8gEDeSB/sun.html
- hxxps://jaipurbynite[.]com/stLdQs9R53/sun.htm
These two URLs fit patterns associated with Qakbot infections in recent weeks. 207.246.77[.]75:2222 is also known for malicious traffic associated with Qakbot.
Final Words
This month's quiz was significantly more difficult than our previous two forensic contests, so thanks to all who participated.
Congratulations again to Dimitri for winning this month's competition!
You can still find the pcap here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net



Comments