ISC snapshot: r-cyber with rud.is
R packages for cybersecurity research, DFIR, risk analysis, metadata collection, document/data processing, and more
I recently delivered my DFIR Redefinded: Deeper Functionality for Investigators in R presentation at the Computer Technology Investigators Network (CTIN) Conference on the Microsoft campus. This is content I provide when and where I can with the hope of inspiring others to experience what happened for me as a direct result of reading Bob Rudis and Jay Jacobs Data-Driven Security. At the risk of being a bit of fan boy, I will tell you that my use of R as part of my information security and assurance practice came via this book and Bob’s rud.is blog.
Bob “has over 20 years of experience defending companies using data and is currently Chief Data Scientist at Rapid7, where he specializes in research on internet-scale exposure.” He embraces the “In God we trust. All others must bring data” approach to his craft, and it’s righteous. One on the products of this approach is r-cyber, a collection of “R packages for use in cybersecurity research, DFIR, risk analysis, metadata collection, document/data processing and more.”
I’ve covered Bob’s work before but wanted to give you a quick primer on some of the useful offerings found via r-cyber. My most recent review included a look at Bob’s Shodan package. A recent post at rud.is reminds us that “RStudio makes for an amazing incident responder investigations console given that you can script in multiple languages, code in C[++], and write documentation all at the same time using R ‘projects’ with full source code control.”
Let’s put a bit of that claim to good use via the Jupyter Notebook I created, available for you here.
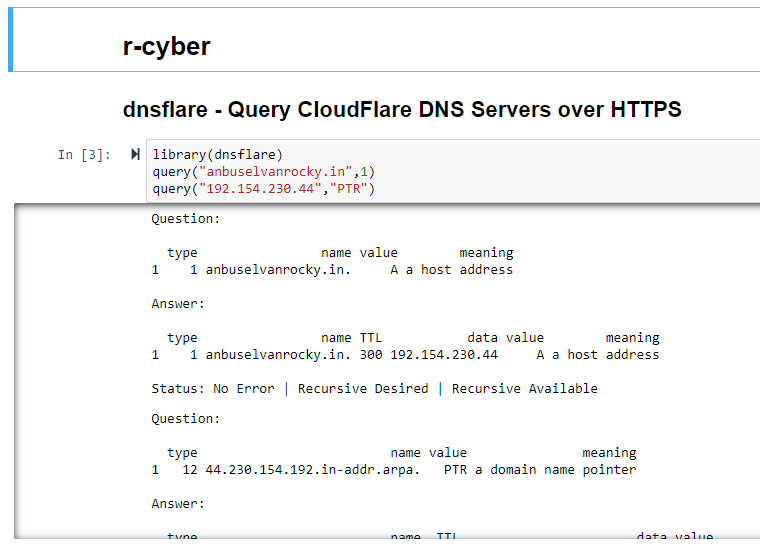
You’re investigating a suspicious domain that you’ve flagged as part of reported phishing attempts received by users in your care, and checking your DNS logs reveals client lookups for a suspicious domain, anbuselvanrocky.in. Start with a quick query of CloudFlare’s DNS API with the dnsflare script.
library(dnsflare)
query("anbuselvanrocky.in",1)
query("192.154.230.44","PTR")
The result follows in Figure 1.
Figure 1: dnsflare results
Given your assertion that this domain, anbuselvanrocky.in, is likely up to no good, find our what the urlscan.io API has to say for the urlscan script.
library(urlscan)
library(tidyverse)
x <- urlscan_search("domain:anbuselvanrocky.in")
as_tibble(x$results$task) %>%
bind_cols(as_tibble(x$results$page)) %>%
mutate( time = anytime::anytime(time), id = x$results$'_id' ) %>%
arrange(desc(time)) %>%
select(url, country, server, ip, id) -> xdf
ures <- urlscan_result(xdf$id[2], include_dom = TRUE, include_shot = TRUE)
ures
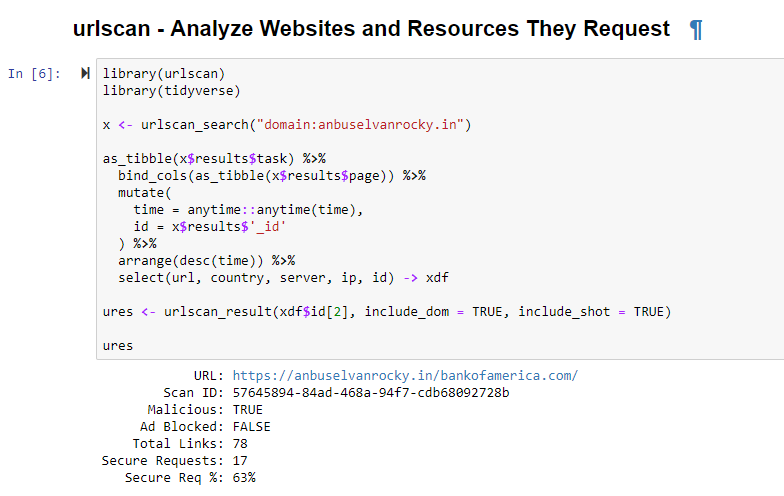
The result is seen in Figure 2.
Figure 2: urlscan results
Note two components in the result that quickly validate your suspicions.
1) URL: https://anbuselvanrocky.in/bankofamerica.com
2) Malicious: TRUE
Sure does smell like phish. Were you to visit urlscan.io via your web browser rather than utilize the API via urlscan R you would see all kinds of confirmation for your concerns.
Yep, BoA phishing.
Now that you’re standing on a stronger investigator’s footing, use the threatcrowd script, which leverages the ThreatCrowd search engine API, to sweep the data available for an IP address related to your investigation.
library(threatcrowd)
search_ips("103.72.163.150")
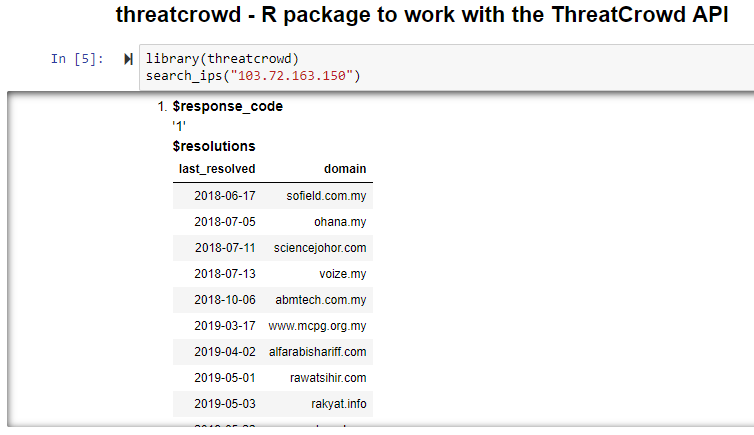
Figure 3 represents all the squirrelly domains resolved to that IP and, as expected, they’re suspicious at best.
Figure 3: threatcrowd results
There are 91 other offerings via rud.is/b/r-cyber, this is but a snapshot to whet your appetite. I am certain Bob will optimize the collection further and set additional organizational structure. Subscribe to the site for updates and follow Bob via @hrbrmstr. Cheers…until next time.
.PNG)


Comments