How your pictures may affect your website reputation
In a previous diary[1], I explained why the automatic processing of IOC’s (“Indicator of Compromise”) could lead to false positives. Here is a practical example found yesterday. I captured the following malicious HTML page (MD5: b55a034d8e4eb4504dfce27c3dfc4ac3)[2]. It is part of a phishing campaign and tries to lure the victim to provide his/her credentials to get access to an Excel sheet. Nothing very dangerous for most people. It’s a simply obfuscated Javascript code:
<script type="text/javascript">
<!--
document.write(unescape("%3c%68%74%6d%6c%3e%3c%68%65%61%64%3e ... ")
//-->
</script>
When loaded in the browser, it first displays a warning:
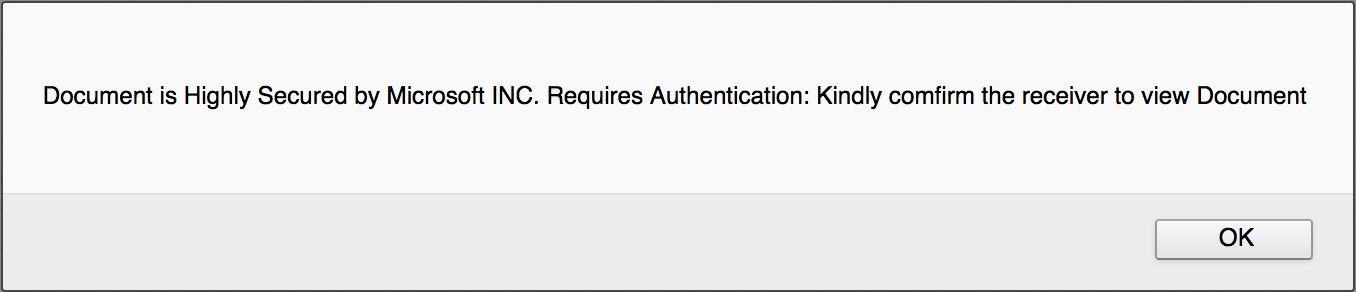
Then, it renders the fake Excel sheet with a popup to enter an email address and password:
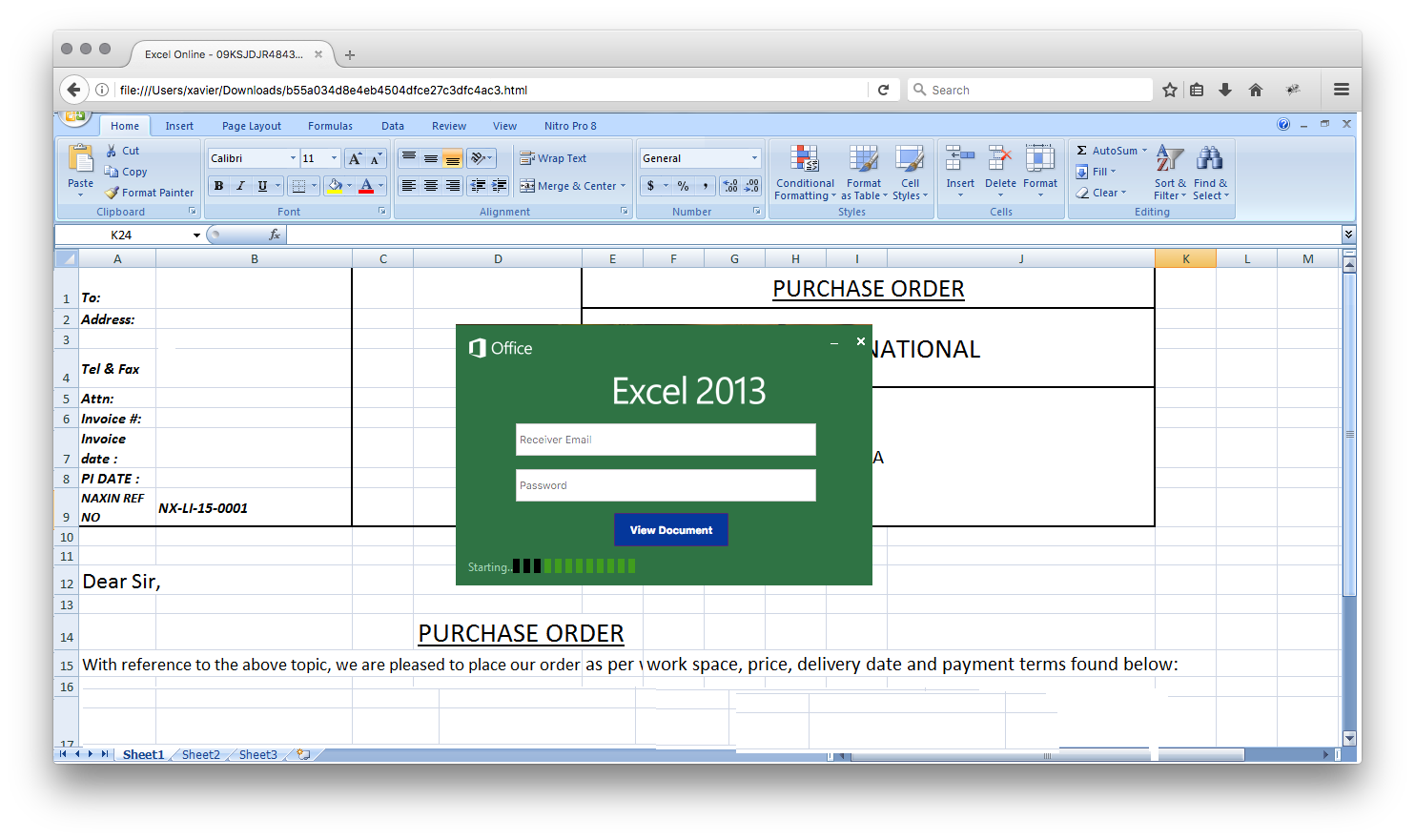
If you analyse this page manually or using a sandbox system, you will see that it performs three HTTP Request to download pictures. My Cuckoo sandbox detected the following HTTP requests (sorry for the small fonts):
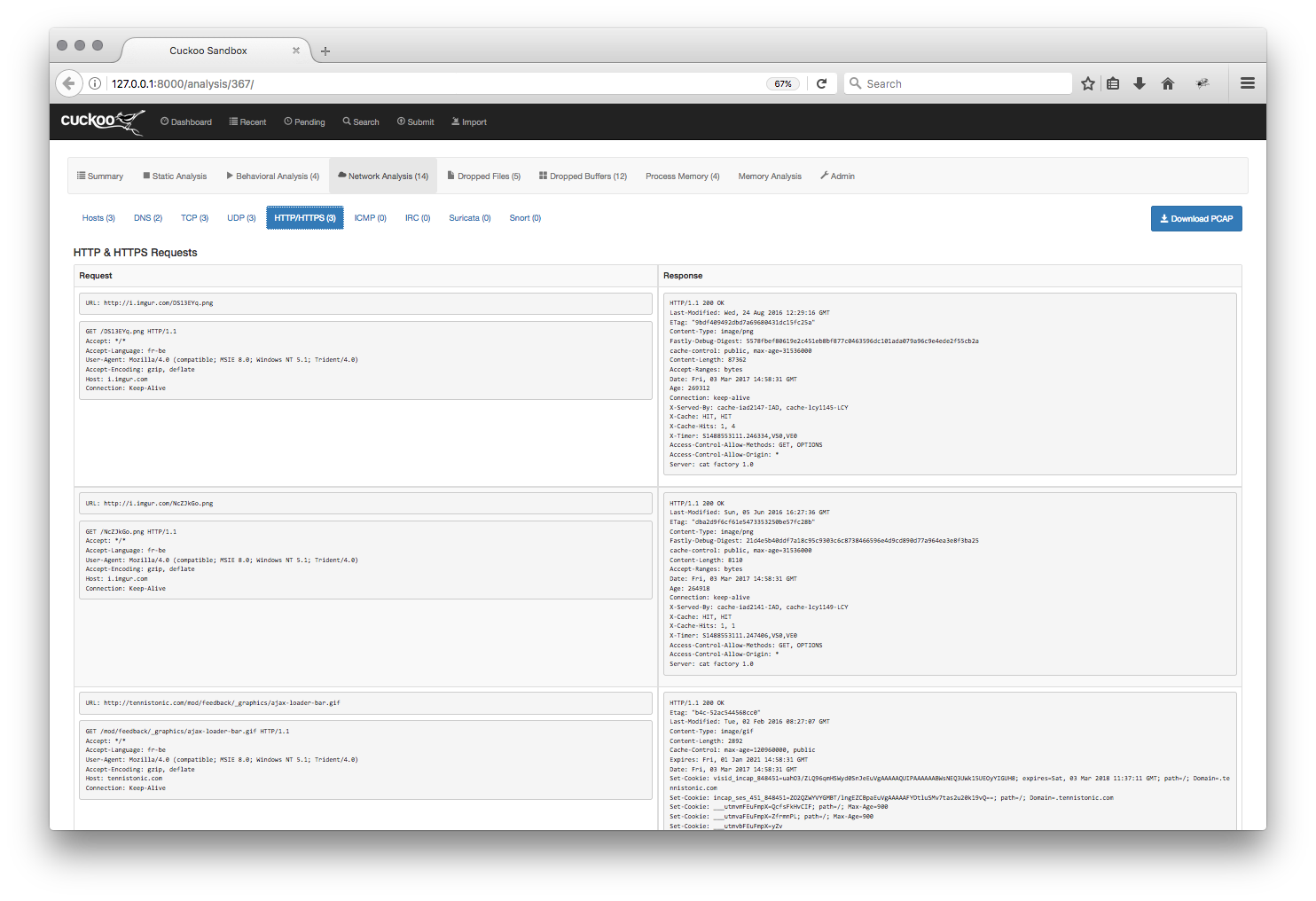
The detected URLs are:
- hxxp://i.imgur.com/NcZJkGo.png : The dialog box
- hxxp://i.imgur.com/DS13EYq.png : The fake Excel sheet
imgur.com is a picture exchange platform and is regularly used to host such material. But the third request is different and looks totally legit:
- hxxp://tennistonic.com/mod/feedback/_graphics/ajax-loader-bar.gif
This last image is an animated GIF that displays a loading bar (close to the “Starting" string on the picture above).
There exists plenty of versions of this loader bar[3] and attackers like them. It’s not unusual to see one on a malicious page to make it look more “dynamic”. The problem is that automation can categorize the website tennistonic.com as malicious and affect its reputation. If a tool decides to put the URL in a list of IOC's, access to it can be blocked when IOCs are used as a blocklist. I also tested this page with a FireEye appliance and the site tennistonic.com popped up in the logs!
A good practice is to prevent hot-linking of images. Basically, you configure your web server to serve images only of the referer is correct:
RewriteEngine on
RewriteCond %{HTTP_REFERER} !^$
RewriteCond %{HTTP_REFERER} !^http(s)?://(www\.)?rootshell.be [NC]
RewriteRule \.(jpg|jpeg|png|gif)$ - [NC,F,L]
Take care!
[1] https://isc.sans.edu/forums/diary/IOCs+Risks+of+False+Positive+Alerts+Flood+Ahead/21977/
[2] https://www.virustotal.com/en/file/ff9ca701cfe7fdccd7aa60d6368c1adc1c4282c030b05a2790bc9a968e870c13/analysis/
[3] https://www.google.be/search?q=ajax-loader-bar.gif
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments
Wouldn't it be nice to get cooperation from the webmaster at that site:
1. change all internal references to that GIF to reference a differently-named GIF (with the same content);
2. replace the original GIF by a large (640-by-480) image showing the text "If you see this image, you have accessed a ROGUE web-site. Please close your web-browser.
See: www.example.com/antiphishing for a full explanation".
Possible?
I know that at least one 3-letter CDN bank detects "deep-linking" to its images, and substitutes a "warning" image.
Anonymous
Mar 4th 2017
8 years ago