Hancitor distributed through coronavirus-themed malspam
Introduction
The criminal group behind Hancitor malware has been quiet during the past few weeks. For the past year or so, this group has stuck with DocuSign-themed malspam to distribute Hancitor (like this example from January 2020). However, today @mesa_matt reported a new wave of Hancitor malspam using a coronavirus theme. Today's diary reviews two quick infection runs using information from @mesa_matt's Twitter thread on Wednesday 2020-03-11.
My thanks to everyone on Twitter who keeps an eye on Hancitor and tweets about it.
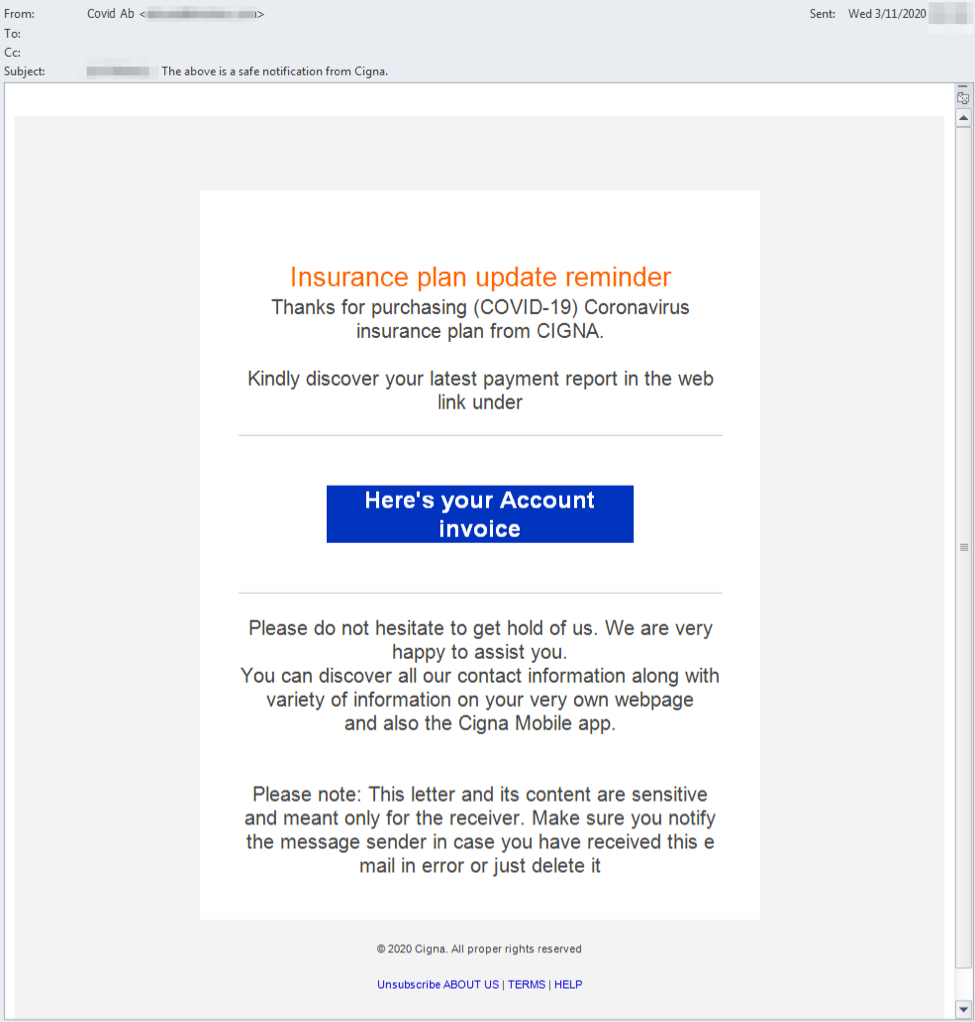
Shown above: Screenshot of the malspam from a tweet by @mesa_matt on 2020-03-11.
Infection traffic
We're still seeing the same sequence of events from previous Hancitor runs so far this year.
- Step 1: Link from malspam
- Step 2: leads to another URL that returns a zip archive
- Step 3: Extract VBS from zip archive
- Step 4: VBS drops and executes Hancitor DLL
- Step 5: Hancitor-style post-infection traffic
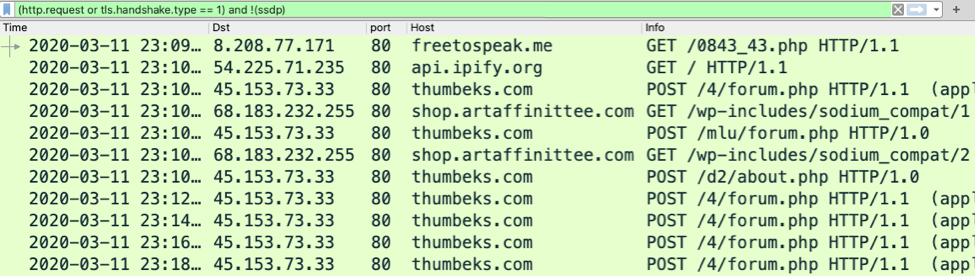
Shown above: Traffic from an infection filtered in Wireshark.
Indicators of Compromise (IoCs)
Traffic from an infected Windows host:
- URL from link in the malspam (various URLs from step 1, not in my pcaps)
- 8.208.77[.]171 port 80 - freetospeak[.]me - GET /0843_43.php
- port 80 - api.ipify[.]org - GET /
- 45.153.73[.]33 port 80 - thumbeks[.]com - POST /4/forum.php
- 45.153.73[.]33 port 80 - thumbeks[.]com - POST /mlu/forum.php
- 45.153.73[.]33 port 80 - thumbeks[.]com - POST /d2/about.php
- 68.183.232[.]255 port 80 - shop.artaffinittee[.]com - GET /wp-includes/sodium_compat/1
- 68.183.232[.]255 port 80 - shop.artaffinittee[.]com - GET /wp-includes/sodium_compat/2
Malware from my infected lab hosts:
SHA256 hash: 4f6d4d8f279c03f1ddfa20f95af152109b7578a2bec0a16a56ff87745585169a
- File size: 230,431 bytes
- File location: hxxp://freetospeak[.]me/0843_43.php
- File name: SE-670131329809_5500.zip
- File description: zip archive downloaded from link in malspam distributing Hancitor (1st run)
SHA256 hash: 6897a3b85046ba97fb3868dfb82338e5ed098136720a6cf73625e784fc1e1e51
- File size: 1,130,515 bytes
- File name: SE670131329809.vbs
- File description: VBS file extracted from downloaded zip archive (1st run)
SHA256 hash: 8a9333204db83c2571463278cb6a6241ae5f215b2166bf4af5693d611049d5a9
- File size: 228,383 bytes
- File location: hxxp://freetospeak[.]me/0843_43.php
- File name: QU-555033076467_5558.zip
- File description: zip archive downloaded from link in malspam distributing Hancitor (2nd run)
SHA256 hash: 8da0eb3a2378d218043e9f3188e59e3158f1fd01bbcd979f05197c74c2fb7a1c
- File size: 1,125,138 bytes
- File name: QU555033076467.vbs
- File description: VBS file extracted from downloaded zip archive (2bd run)
SHA256 hash: 291a4eb06358eca87fbc1f133ee162b6c532f4ec3e6f39c2646cde5de60e80f9
- File size: 253,952 bytes
- File location: C:\Users\[username]\AppData\Local\Temp\adobe.txt
- File description: Hancitor DLL dropped after executing above VBS files (both runs)
For further information:
- Twitter thread from @mesa_matt with a screenshot of a malspam example: link
- Initial info on Pastebin for Hancitor malspam from @mesa_matt Twitter thread: link
- Any.Run sandbox analysis for URL used to kick off my infection runs: link
- File hashes on Pastebin for this Hancitor from paste by JAMES_INTHE_BOX: link
Final words
Pcaps of my infection traffic along with the associated malware can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments