Extra Tip For Triage Of MALWARE Bazaar's Daily Malware Batches
Here's an extra tip to my diary entry "Simple Tips For Triage Of MALWARE Bazaar's Daily Malware Batches".
You can also use YARA rules together with my zipdump tool:
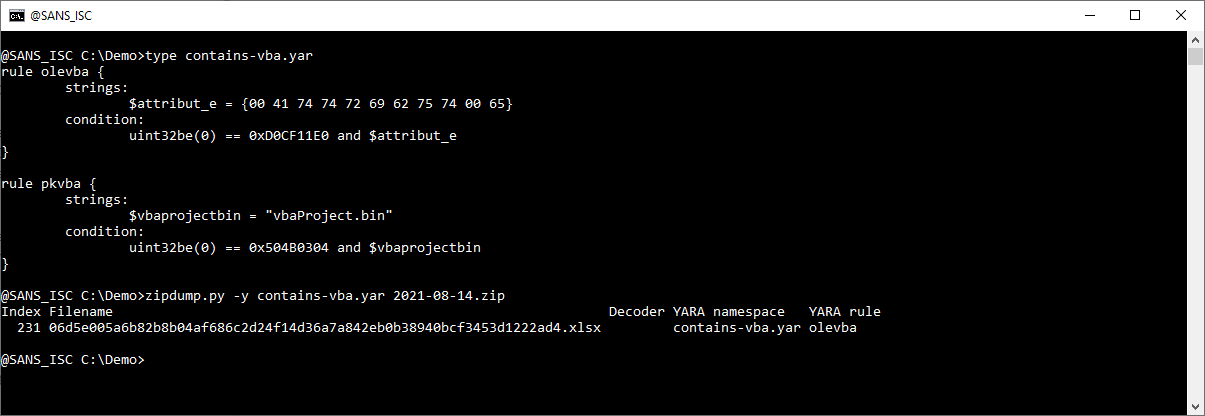
I'm using 2 simples rules to detect Office documents with VBA macros:
rule olevba {
strings:
$attribut_e = {00 41 74 74 72 69 62 75 74 00 65}
condition:
uint32be(0) == 0xD0CF11E0 and $attribut_e
}rule pkvba {
strings:
$vbaprojectbin = "vbaProject.bin"
condition:
uint32be(0) == 0x504B0304 and $vbaprojectbin
}
Rule olevba is for binary (ole) office documents, and rule pkvba is for OOXML documents.
Remark: these rules are designed for triage: they might generate false positives or negatives.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com


Comments