Detecting irregular programs and services installed in your network
by Manuel Humberto Santander Pelaez (Version: 1)
When the corporate network becomes target, auditing for security policy compliance can be challenging if you don't have a software controlling irregular usage of administrator privilege granted and being used to install unauthorized software or to change configuration by installing services that could cause an interruption in network service. Examples of this possible issues are additional DHCP Servers (IPv4 and IPv6), Dropbox, Spotify or ARP scanning devices.
We can use nmap to detect all protocols that sends broadcast packets and are supported by packetdecoders.lua:
- Ether
- ARP requests (IPv4)
- CDP - Cisco Discovery Protocol
- EIGRP - Cisco Enhanced Interior Gateway Routing Protocol
- OSPF - Open Shortest Path First
- UDP
- DHCP
- Netbios
- SSDP
- HSRP
- DropBox
- Logitech SqueezeBox Discovery
- Multicast DNS/Bonjour/ZeroConf
- Spotify
The following example shows how to use nmap with the broadcast listener script and we can see the result of a device with dropbox installed, a device sending ARP request (a router in this case) and a device sending DHCPv6 requests:
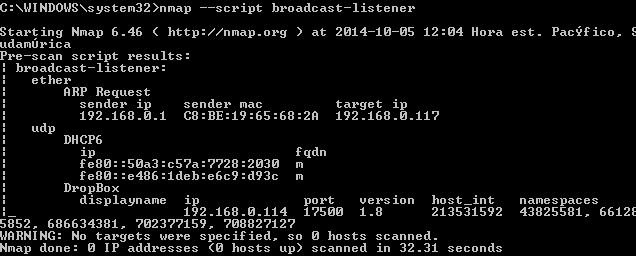
You can run this program periodically to track common security issues in your network, just in case your IPS could be missing something ;)
Manuel Humberto Santander Pelaez
SANS Internet Storm Center - Handler
Twitter:@manuelsantander
Web:http://manuel.santander.name
e-mail: msantand at isc dot sans dot org


Comments