Current PayPal phishing campaign or "give me all your personal information"
One of my colleagues sent me a new PayPal phishing e-mail today. Although it was fairly usual, as phishing e-mails go, since the campaign is still active and since it shows the current "let’s take all that we can get" mentality of the attackers quite well, I thought it was worth a short diary.
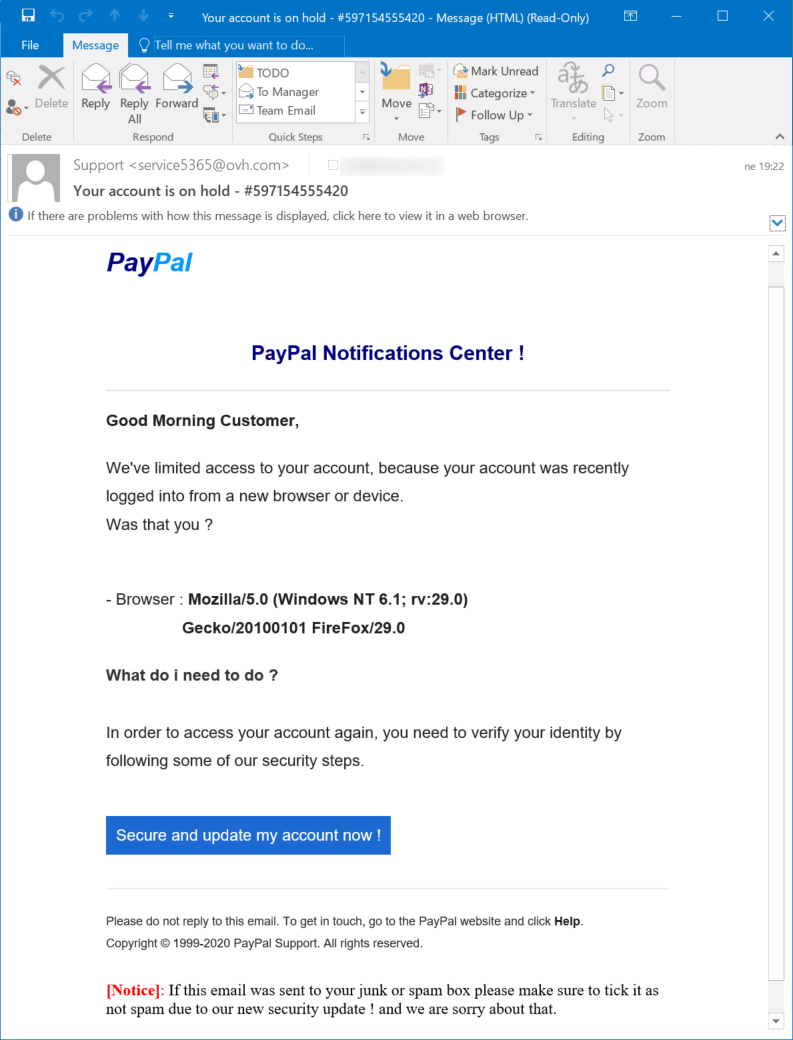
As you may see above, the e-mail used the standard phishing hook of "your account was locked". The link in the message pointed to a bit.ly address, which pointed to a redirection mechanism, which finally pointed the browser to the phishing page itself (see IoCs at the end for the URLs).
The first page looked like the usual PayPal login screen. The only slightly interesting point related to it is that its authors didn’t even bother to write a regex or any other check for the e-mail field.
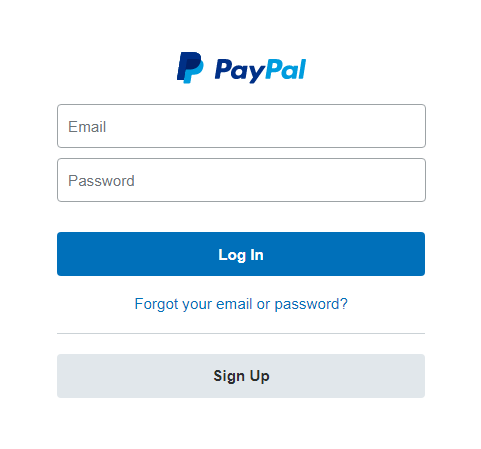
After "logging in" the usual general information gathering form was displayed.
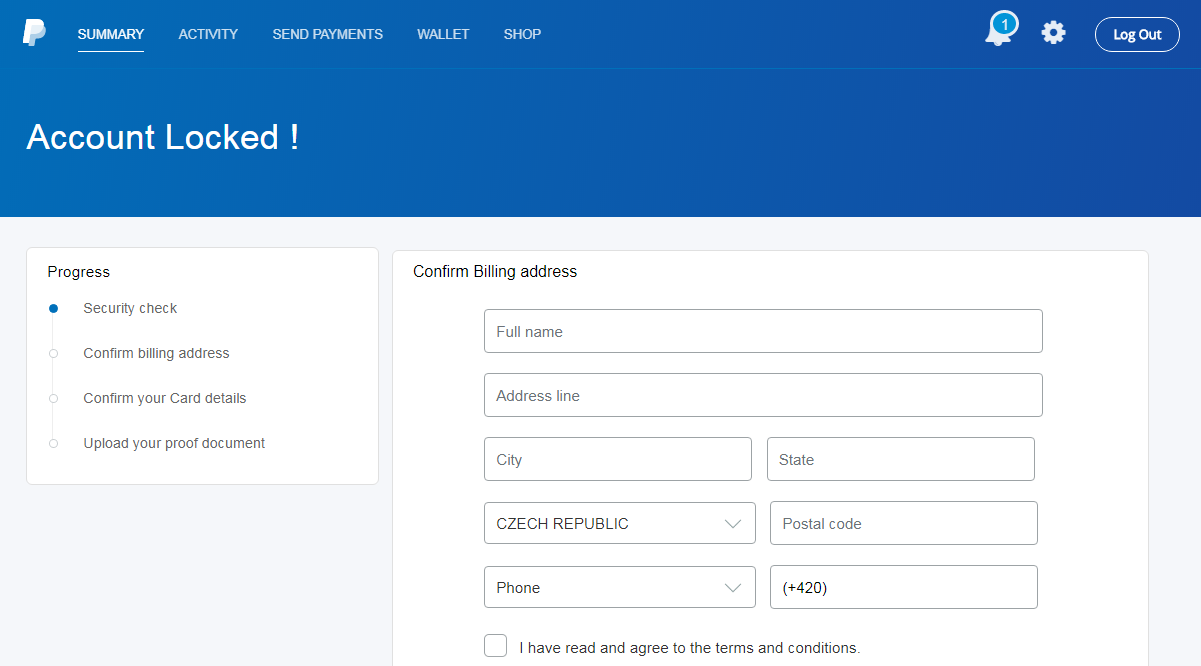
This page was followed by another usual form - this time one for filling in credit card details.
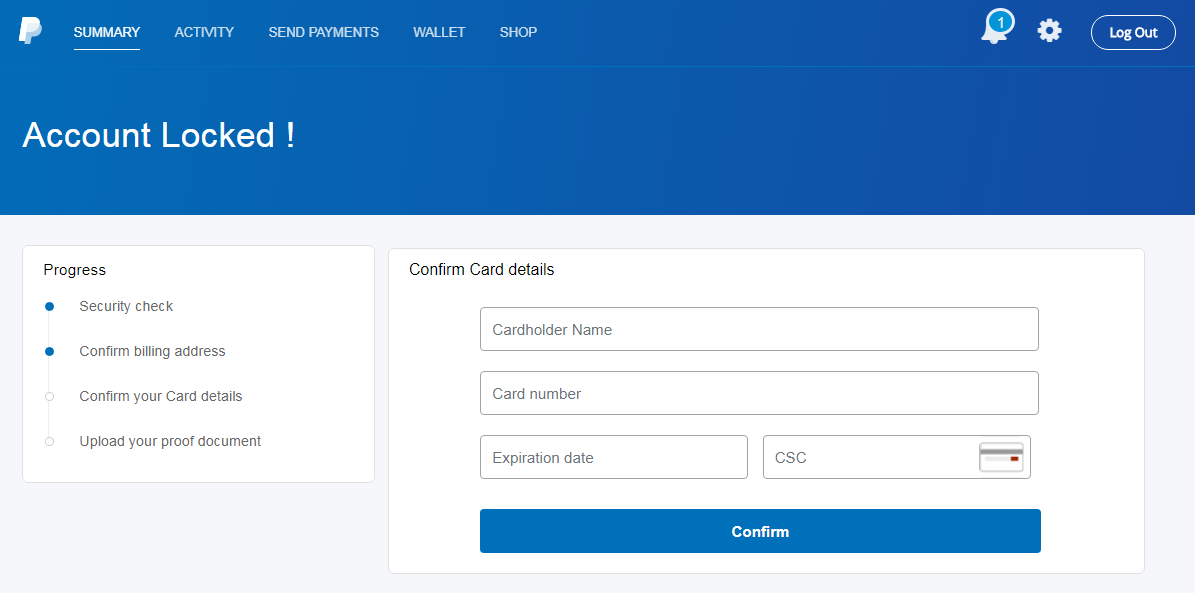
So far, it looked like any other phishing campaign ever sent. However, the pages that followed illustrated quite well that it was a modern campaign. That is because over the years, phishing authors seem to have learned that once they hook a phish, they should try to get all the information they can from them. This is the reason why many current campaigns don’t stop after getting the usual credit card information, but go further.
In this case, the phishers continued by trying to get the user to fill in a social security number and the card PIN.
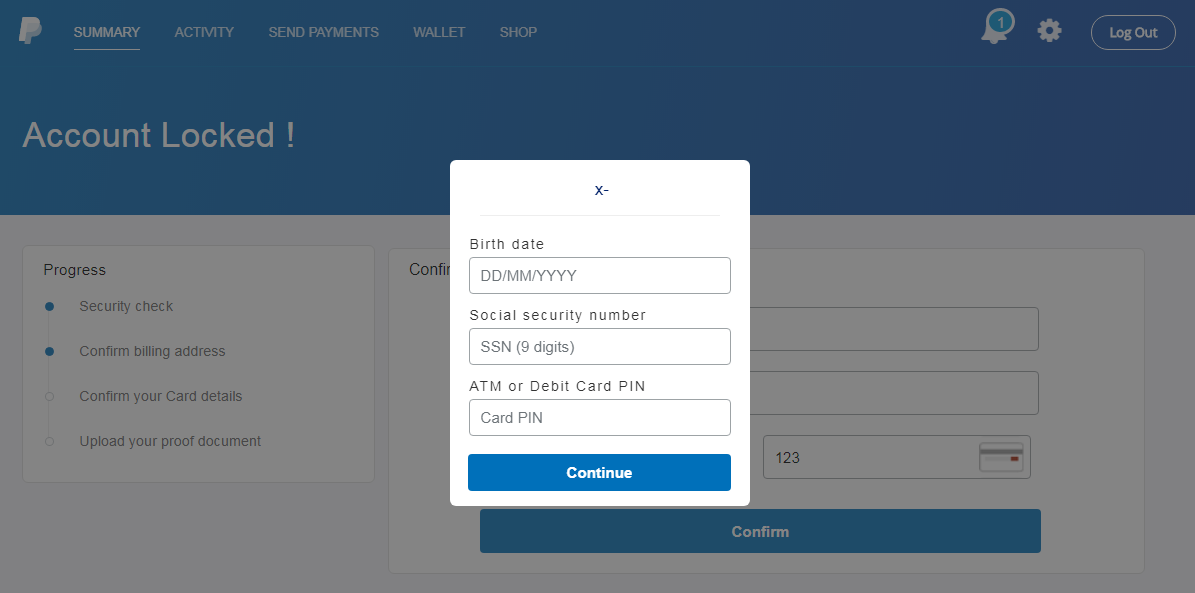
They didn’t stop even there however, and on the last page asked the user to upload a photo of a valid ID or credit card. What might be a bit unfortunate from the standpoint of a potential victim is that after the user uploads a file, the page is refreshed but no confirmation is displayed. This means that a less vigilant user might upload multiple photos of documents while thinking that their previous attempts were invalid for some reason.
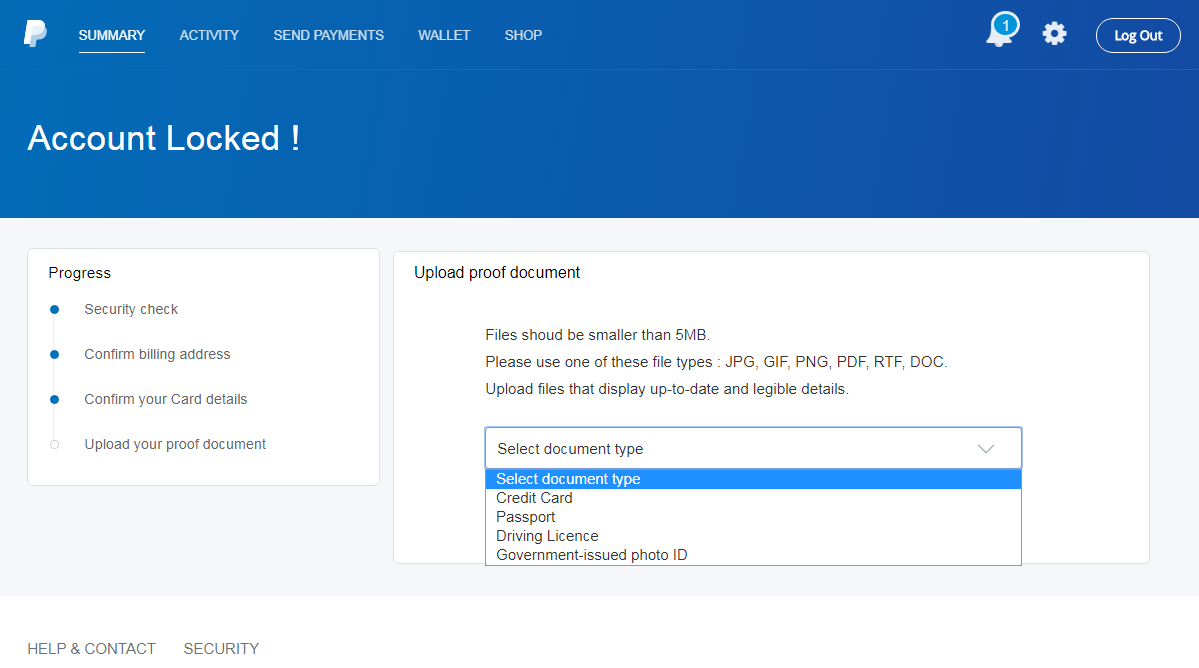
Although I reported the phishing to PayPal, it may be a while before they manage to take it down. In the meantime, you may use the following URLs to have a look at the phishing page yourselves and/or check whether someone in your organization wasn’t the target of the same campaign.
Indicators of Compromise (IoCs)
https://bit.ly/2SwO61R
https://nadhirotultaqwa.com/usrah/redirect.php
https://www.leemou.com/files/selector/



Comments
The https certificate used by www.leemou[.]com reveals a number of domains that the certificate is valid for:
leemou[.]com
autodiscover.leemou[.]com
cpanel.leemou[.]com
leemou.pistachio.my
mail.leemou[.]com
webdisk.leemou[.]com
webmail.leemou[.]com
www.leemou[.]com
www.leemou.pistachio[.]my
For example hxxps://webmail.leemou[.]com/ is alive and kicking. It provides a selector for a huge number of GUI languages.
However, the sites I looked at, did not look like phishing sites because no images were shown. This may be to convince the hosting provider that the site is legit and should not be taken down or the certificate provider ("cPanel, Inc. Certification Authority") to not revoke the certificate. Of course, the sites may look different when viewed with another browser, a browser with other characteristics, depending on source IP (geo location) etcetera.
Bitwiper
Anonymous
Feb 10th 2020
5 years ago