Analysis of a Salesforce Phishing Emails
Over the past week, I have noticed several phishing emails linked to Salesforce asking to confirm the recipient’s email address.
Sample Header

The body of the email is quite simple. Reviewing the email View Message URL by hovering over the URL or changing email to text mode and comparing it against the correct Salesforce website URL, it clearly shows the client is getting phished.
Email Body
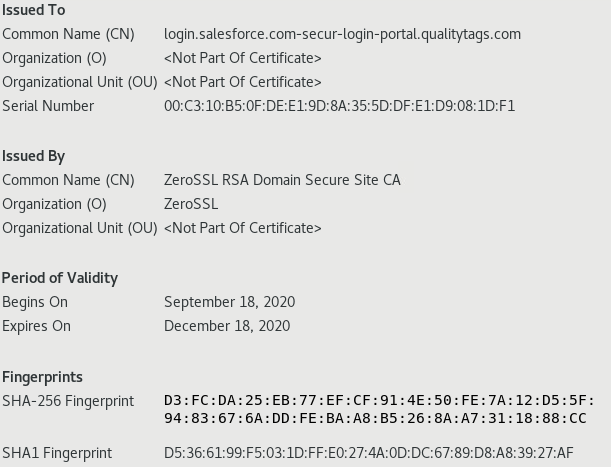
The next thing on the verification list for this email is the SSL certificate of the site; it was created yesterday (18 Sep 2020) and this email was received today (see sample header). The certificate is authenticated by ZeroSSL which is considered an alternative to Let's Encrypt where you can also create for free a certificate valid for 90 day.
ZeroSSL Certificate Information
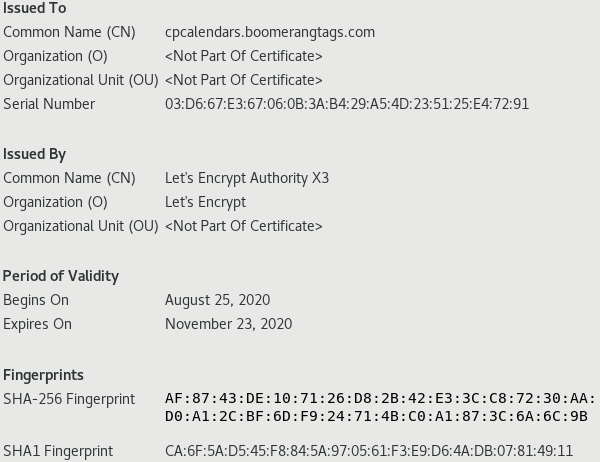
The root domain associated with login.salesforce.com-secur-login-portal.qualitytags[.]com and www[.] qualitytags[.]com are both resolving to 162.241.159.57 but www[.] qualitytags[.]com is using a Let's Encrypt certificate setup on the 25 Aug 2020 good for 90 days.
Let's Encrypt Certificate Information
These few simple steps can be used to verify the legitimacy of a website by examining the certificate information, its URL and manually do a quick search to confirm the website URL contained in the email is the same as the true website. The From: email address from the header (info@saggioventures[.]com) doesn't match the domain name which would be another clue that something is suspicious. If unsure, it is a good idea to report it to the security team for analysis.
[1] https://zerossl.com
[2] https://letsencrypt.org
[3] https://isc.sans.edu/ipinfo.html?ip=162.241.159.57
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu


Comments