Analysis of a Paypal phishing kit
They are plenty of phishing kits in the wild that try to lure victims to provide their credentials. Services like Paypal are nice targets and we can find new fake pages almost daily. Sometimes, the web server isn’t properly configured and the source code is publicly available. A few days ago, I was lucky to find a ZIP archive containing a very nice phishing kit targeting Paypal. I took some time to have a look at it.
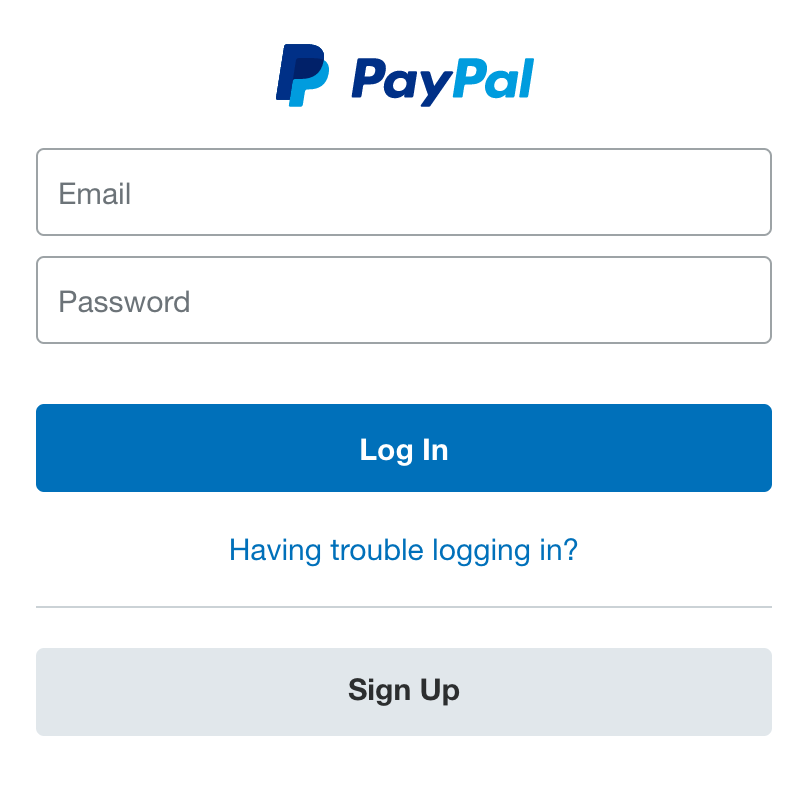
I presume that the kit is related to a spam campaign but I did not get the initial email. Based on the quality of the kit, I suspect the email to be properly written. As usual, it starts with the classic Paypal login page:
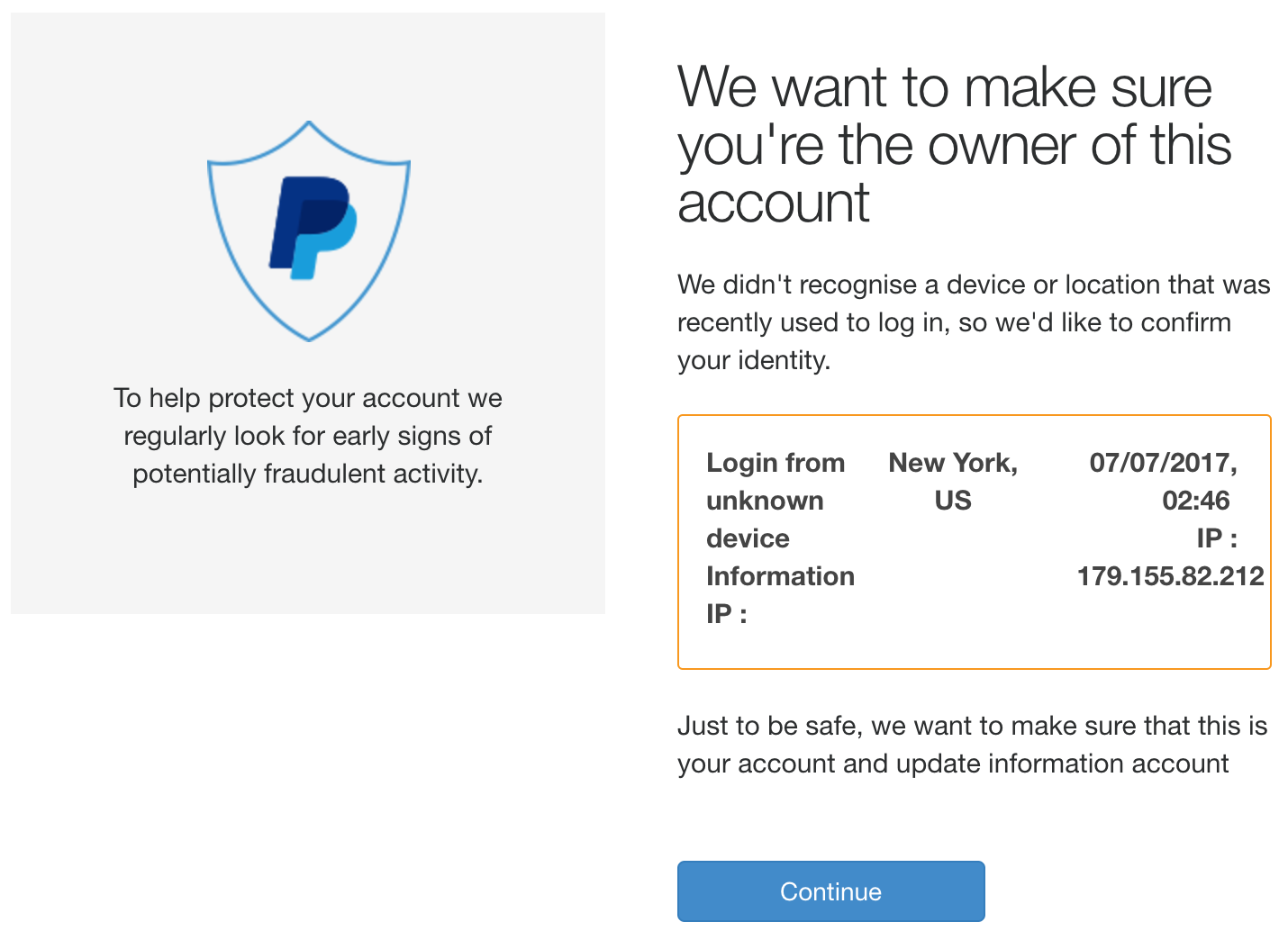
Then a fake verification page is displayed to warn the victim that a check of the account must be performed. Note that the values are hard coded.
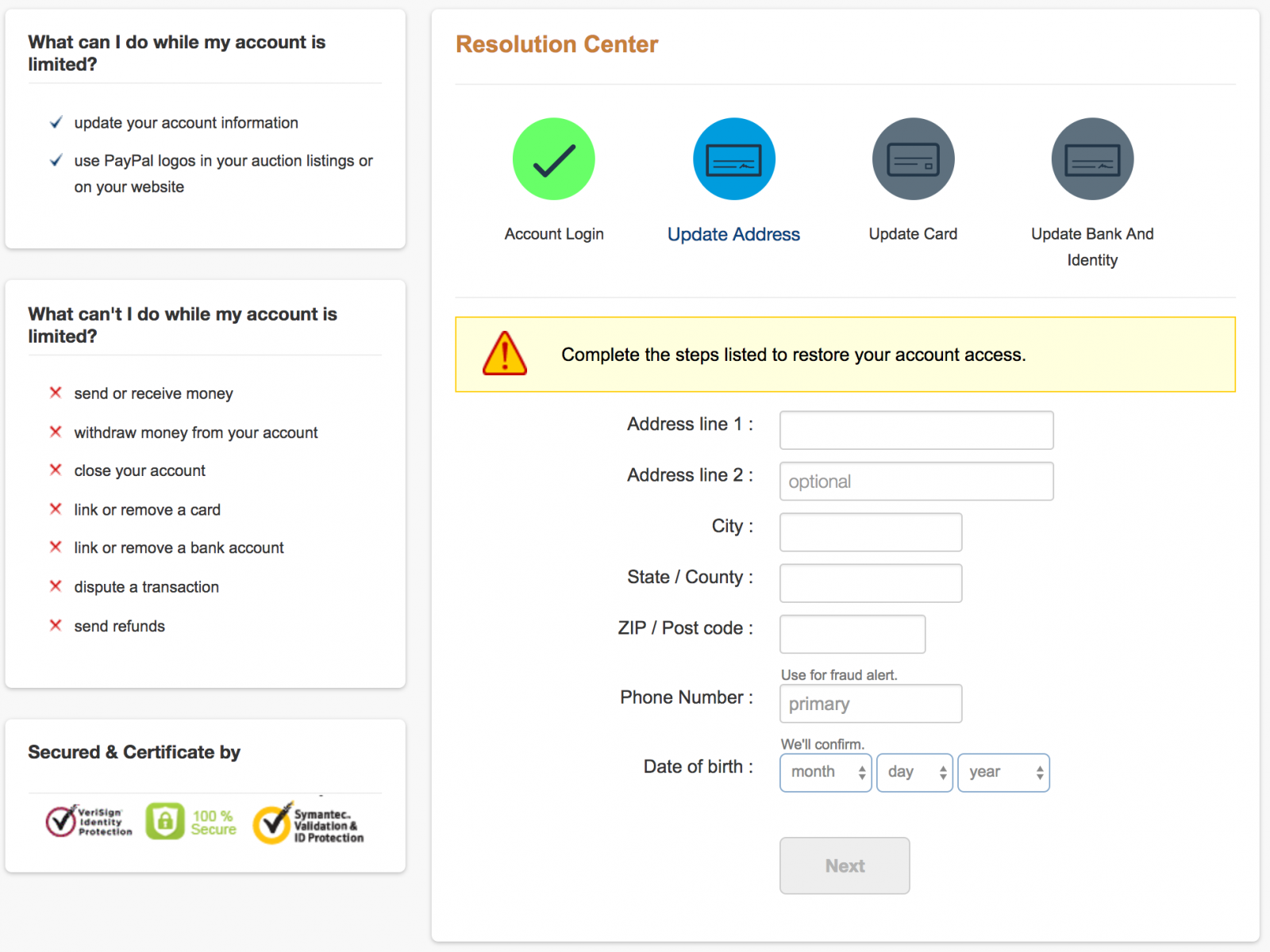
The next steps ask the victim to enter his/her details, including banking details.
Graphically, the different pages are very clean and use components from the Paypal website to reproduce a look and feel very close to the official pages. Let’s have a look at the code now.
First the timezone is set to Tokyo with the date_default_timezone_set() PHP function. Some comments in the code reveal that the attacker is speaking Indonesian (example: “masuk” means “sign in”). The victim’s IP address, user-agent are logged in a log file. Then, the kit protects itself against crawlers and security scanners or infosec companies. Before displaying the login page, they are controls performed via .htaccess to blocklist some IP addresses or User-Agents:
RewriteCond %{HTTP_USER_AGENT} ^googlebot [OR]
RewriteCond %{HTTP_USER_AGENT} ^TweetmemeBot [OR]
RewriteCond %{HTTP_USER_AGENT} ^BlackWidow [OR]
RewriteCond %{HTTP_USER_AGENT} ^ChinaClaw [OR]
RewriteCond %{HTTP_USER_AGENT} ^Custo [OR]
RewriteCond %{HTTP_USER_AGENT} ^DISCo [OR]
RewriteCond %{HTTP_USER_AGENT} ^Download\ Demon [OR]
RewriteCond %{HTTP_USER_AGENT} ^eCatch [OR]
RewriteCond %{HTTP_USER_AGENT} ^EirGrabber [OR]
order allow,deny
deny from x.123.119.163
deny from x.163.233.200
deny from x.169.29.56
deny from x.65.136.19
deny from x.2o7.com
deny from x.56.163.46
deny from x.56.163.64
deny from x.20.57.227
There is also a second check of the IP address included in the PHP code. If a valid IP address or User-Agent is detected, an HTTP error 404 (page not found) is returned. Geolocation of the victim is performed via www.geoplugin.net. To generate unique URLs, the phishing kit copies itself into a temporary directory (randomly generated). This helps to protect against basic filtering in IDS or firewalls.
After the victim provided his/her credentials, the nice feature is a connection attempt to Paypal to try to validate them. If it works, useful information is extracted from the HTML code. The following URLs are used to achieve this:
https://www.paypal.com/cgi-bin/webscr?cmd=_profile-address https://www.paypal.com/cgi-bin/webscr?cmd=_profile-phone
When the verification screens are displayed to the victim, fields are prefilled with the extracted information from Paypal. This is really evil! All fields are also validated to prevent garbage and increase the change to capture real data. Depending on the card number that the victim provided, a next screen is presented to fill bank details. Based on the source code, three countries are targeted: US, CA and UK. Depending on the bank, specific forms are displayed to request valid connection details. Here are the US bank listed in the code:
else if ($negara=="US") { echo '
<p class="field" >Bank Name :
<select id="bank" name="bnknameus" style="padding-left:4%;">
<option value="">Select Bank</options>
<option value="Ally Financial">Ally Financial</options>
<option value="American Express Company">American Express Company</options>
<option value="BB&T">BB&T</options>
<option value="Bank of America">Bank of America</options>
<option value="Bank of New York Mellon">Bank of New York Mellon</options>
<option value="Charles Schwab Corporation">Charles Schwab Corporation</options>
<option value="Capital One">Capital One</options>
<option value="Citizens Financial Group">Citizens Financial Group</options>
<option value="Citigroup">Citigroup</options>
<option value="Fifth Third Bank">Fifth Third Bank</options>
<option value="Goldman Sachs">Goldman Sachs</options>
<option value="HSBC Bank USA">HSBC Bank USA</options>
<option value="JPMorgan Chase">JPMorgan Chase</options>
<option value="Morgan Stanley">Morgan Stanley</options>
<option value="PNC Financial Services">PNC Financial Services</options>
<option value="SunTrust Banks">SunTrust Banks</options>
<option value="State Street Corporation">State Street Corporation</options>
<option value="TD Bank">TD Bank, N.A.</options>
<option value="US Bancorp">U.S. Bancorp</options>
<option value="Wells Fargo">Wells Fargo</options>
<option value="otherus">Other</options>
</select>
At the end of the “verification process”, an email is sent to the attacker with all the victim's details. The destination is a gmail.com account. Here is an example of data exfiltrated to the attacker:
++-----[ $$ [-]Cikampek-T34m[-] $$ ]-----++
.++=====[ Tukang Credit ]=====++.
Cardholder Name : Test Test
Card Number : 4111 1111 1111 1111
Expiration Date : 05 / 2019
Cvv2 : 111
BIN/IIN Info : - - -
Sort Code : - -
Account number :
BSB - OSID : -
Credit Limit :
Mother's name :
Account Name :
Address Line 1 : Address1
Address Line 2 :
City/Town : City
State : State
Zip/PostCode : 1000
Country :
Phone Number : 0123456789
SSN : - -
ID Number :
DOB : 3 / 3 / 1991
.++=========[ End ]=========++.
.++=======[ PC Info ]=======++.
From : 172.16.0.20 On Wed, 16 Aug 2017 08:00:07 +0200
Browser : Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_5) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/60.0.3112.90 Safari/537.36
.++=========[ End ]=========++.
++-----[ $$ [N]e[V]e[R] [GIVE UP] $$ ]-----++
If most phishing kits remain simple and can be easily spotted by the victims, some of them are really well developed and harder to catch, especially if the URL used is nicely chosen and distributed via HTTPS. This kit was huge with more than 300 files in a 1.8MB ZIP file. Take care!
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments