Secunia's DNS/domain hijacked?
We received quite a bit of reports of people saying that Secunia’s web site has been defaced. And indeed, when I visit Secunia’s web site from my machine (located in Europe), I see a defaced web site as below:
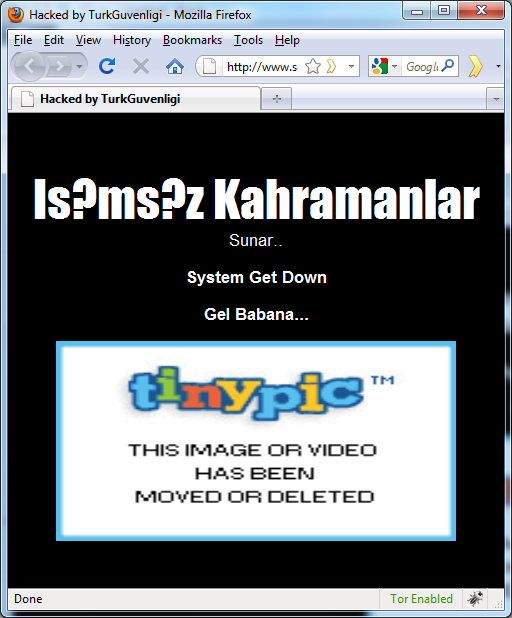
However, after double checking it appears that their DNS records have been modified. The “defaced” web site is located (for me) at the following IP address:
$ host www.secunia.com
www.secunia.com is an alias for secunia.com.
secunia.com has address 81.95.49.32
secunia.com mail is handled by 0 secunia.com.
Checking my passive DNS system, I can see that previously www.secunia.com was at 213.150.41.226.
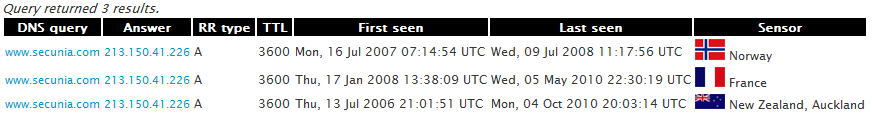
And, as suspected, after checking manually we can see that the original Secunia’s web site is still there:
$ telnet 213.150.41.226 80
Trying 213.150.41.226...
Connected to secunia.com (213.150.41.226).
Escape character is '^]'.
GET / HTTP/1.0
Host: secunia.com
HTTP/1.1 200 OK
Date: Thu, 25 Nov 2010 08:46:29 GMT
Server: Apache
...
<meta name="Title" content="Secunia.com">
<link rel="stylesheet" type="text/css" href="/css/secunia.css">
Checking WHOIS entries will show more, but this "defacement" again shows how DNS is a critical resource.
--
Bojan
INFIGO IS
| Web App Penetration Testing and Ethical Hacking | London | Mar 2nd - Mar 7th 2026 |


Comments
Redirection of DNS traffic
10:15 CET on the 25th November 2010
Entry written by Thomas Kristensen.
On Thursday 25th November at 00:40AM CET the authoritative DNS hosting was redirected for 1 hour 10 minutes.
This has resulted in traffic temporarily being redirected to a non-Secunia site.
Due to standard DNS caching at some Internet Service Providers, some users may still be redirected.
The incident is currently being investigated and we will update our blog with relevant information.
Customers may contact our Customer Support Center at [email protected] or call +45 7020 5144 with any questions.
Kind regards,
Thomas Kristensen
CSO
Techvet
Nov 25th 2010
1 decade ago
Steve Shockley
Nov 25th 2010
1 decade ago
If the domain registrar had supported DNSSEC, that wouldn't have offered any additional security here, because the attacker's DNS zone could have carried a genuine signature.
Someone may even have been able to sign up for an email-validated SSL certificate from a trusted CA during the hijack, since the activation email (as well as Secunia's other email) may have been directed to an attacker's server. That could be a risk to customers of their PSI/CSI product.
Better be very careful with your domain registrar accounts; they're a huge vulnerability, and far too much trust seems to be put into them. I'm surprised this doesn't happen more often.
I guess this weakness in the system exists for political reasons, to allow governments or law enforcement to shut down a site via the domain registrar. The Tor network's ".onion" TLD seems like a superior design, where the domain name itself is a public key where only the operator holds the corresponding private key. It occurs to me now that a similar TLD on the 'real' Internet might be quite awesome.
Steven Chamberlain
Nov 25th 2010
1 decade ago
Steven Chamberlain
Nov 25th 2010
1 decade ago