Adobe Acrobat Spam Going Strong - More to Come?
We received several reports of spam email messages that advertise a new version of Adobe Acrobat, attempting to entice the recipient into clicking a link to a suspicious website. (Thanks, Steve and Bill.)
Since Adobe announced a new version of Adobe Reader a few days ago, we expect to see an increase in spam proclaiming security advantages of the new version and encouraging people to upgrade. It's likely that the new messages will even highlight the improved security of the new version (Adobe Reader X) as an element of social engineering.
At the moment, Adobe Acrobat/Reader spam is not yet using the Reader X designation, but talks about "Adobe Acrobat 2010":
Subject: Download Your New Adobe PDF Reader For Windows And Mac
INTRODUCING UPGRADED ADOBE ACROBAT 2010
Dear Customers,
Adobe is pleased to announce new version upgrades for Adobe Acrobat 2010.
hxxp://www.adobe -acrobat-solutions.com
Advanced features include:
...
Variations of these messages have been around for a few months, as Adobe confirmed on September 13. The spam that we've seen have used mostly the same text in the body of the email message, but changed email Subject lines and destination URLs:
September:
Subject: Upgrade New Adobe Acrobat 2010 PDF Reader Alternative, hxxp://www.pdf -adobe-download.com
October:
Subject: Adobe Upgrade Notification, hxxp://www.adobe -upgrades.com
Subject: Action Required : Download Your New Adobe Acrobat Reader, hxxp://www.adobe -acrobat-new-download.com
Subject: New Adobe Acrobat PDF Reader Alternative, hxxp://www.official -adobe-software.com
November:
Subject: Action Required : Active Your New Adobe PDF Reader, hxxp://http://www.adobe -pro-software.com
Subject: Action Required : Upgrade Your New Adobe PDF Reader, hxxp://www.adobe -pro-upgrade.com
Subject: Download Your New Adobe PDF Reader For Windows And Mac, hxxp://www.adobe -acrobat-solutions.com
Note that suspicious domains used as part of this campaign tend to include "adobe" as part of its name, along with incorporating hyphens.
The domains that are still active were registered with Regional Network Information Center, JSC dba RU-CENTER and specified ns3.nic.ru, ns4.nic.ru, and ns8.nic.ru as their DNS servers. Contact details for the domain sometimes specified "PDF Reader Solutions" as the registrant, and were probably fake.
The sites advertised as part of the spam campaign attempt to convince the person to provide his or her credit number to obtain PDF reader/writer software using a form that's hosted on secureonline.ru. We haven't checked whether the software is actually malicious, but we're doubtful of its intentions.
Here's what the landing pages linked from spam messages looked like:

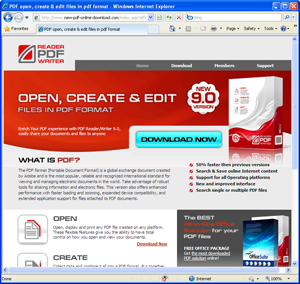
Here's what the subsequent pages, which requested user data, looked like:

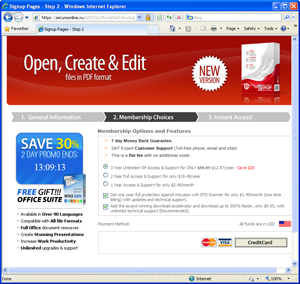
To see full-size images, visit the screen shot gallery at http://www.dropmocks.com/mKDOP.
Consider letting users in your organization know about these Adobe spam activities, so that they don't attempt to download and install software coming from an untrusted source.
Update: Brian Krebs published a story describing that the spamming campaign described in this note is part of criminal efforts that have been targeting "e-mail marketing companies that manage opt-in campaigns for some of the biggest corporate brands in existence."
-- Lenny Zeltser
Lenny Zeltser leads a security consulting team and teaches how to analyze and combat malware. He is active on Twitter and recently launched a security blog.


Comments