Port 1801 Traffic: Microsoft Message Queue
I planned a bit a more conclusive story here, but after running into issues decoding the packets and running out of time between looking at student papers, I figured I would leave it up to the audience ;-) Maybe someone here better understands the Microsoft Message Queue (MSMQ) protocol.
Yesterday's Microsoft patch Tuesday included a single critical vulnerability, a code execution vulnerability in MSMQ. I noted in the podcast that we see some "background hum" on port 1801, the port used by MSMQ.
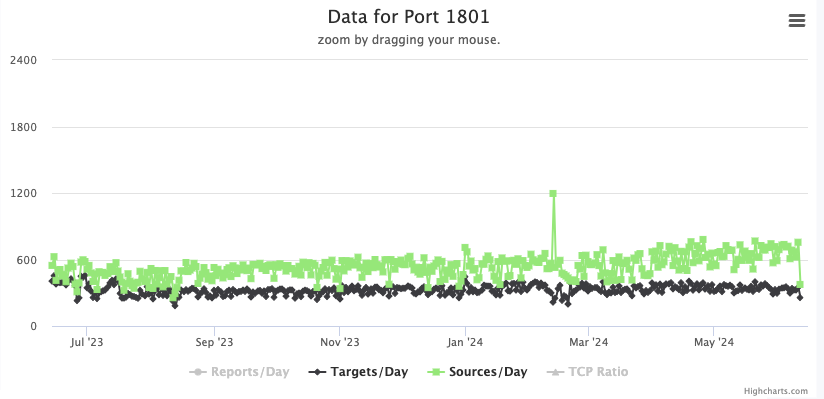
So I fired up some netcat listeners on port 1801, and after a short wait, this is what I got:
(this is the TCP payload. I removed IP and TCP header)
0000 10 c0 0b 00 4c 49 4f 52 3c 02 00 00 ff ff ff ff ....LIOR<.......
0010 00 00 02 00 d1 58 73 55 50 91 95 95 49 97 b6 e6 .....XsUP...I...
0020 11 ea 26 c6 07 89 cd 43 4c 39 11 8f 44 45 90 78 ..&....CL9..DE.x
0030 90 9e a0 fc 4e ca de 1d 10 03 00 00 00 00 00 00 ....N...........
The entire payload had 572 bytes, but I removed the trailing 0-bytes.
Any idea? The bit of decoding I did so far suggests that this is MSMQ, and likely just checking if I am running a MSMQ server. What response should I return?
thanks!
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |


Comments