Using ChatGPT to Deobfuscate Malicious Scripts
Today, most of the malicious scripts in the wild are heavily obfuscated. Obfuscation is key to slow down the security analyst's job and to bypass simple security controls. They are many techniques available. Most of the time, your trained eyes can spot them in a few seconds but it remains a pain to process manually. How to handle them? For soe of them, you have tools like numbers-to-strings.py[1], developed by Didier, to convert classic encodings back to strings. Sometimes, you can write your own script (time consuming) or use a Cyberchef recipe. To speed up the analysis, why not ask some help to AI tools? Let's see a practical example with ChatGPT.
Yesterday, I found a malicious Python script (SHA256:b31d0148ab14678600dbdfb86183831431872de738f21032e51339c31f83d743) with a low VirusTotal score of 2/61[2]. When I had a look at it, it was obfuscated with the following techniques. All interesting strings were hex-encode, compressed and Base64-encoded:
if config.get(__import__('base64').b64decode(__import__('zlib').decompress(b'x\xda\x0b5\n+\x8e\xca\xb1\xccO\x0c\x0f\xca\x01\x00\x1as\x045')).decode()):
Thread(target=self.hide).start()
if config.get(__import__('base64').b64decode(__import__('zlib').decompress(b'x\xda\x0br\xcf\xa9\x8a\x0c\xf7*\x8e\n\xb3\xcc\x8e\n\x8f\xcaI\xca\r\xcaIN\xb7\xb5\x05\x00k\xba\x08\x89')).decode()):
Thread(target=self.defender).start()
First of all, it's not readable in the code above but some strings were in UTF-16:
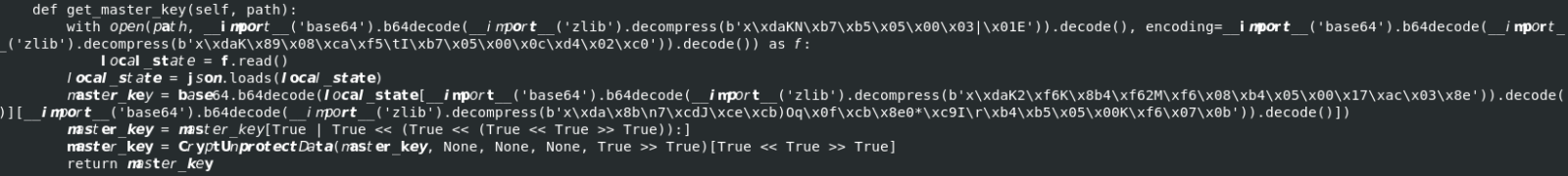
There was a huge amount of obfuscated strings (443 in total). Let's try tro process them with ChatGPT:
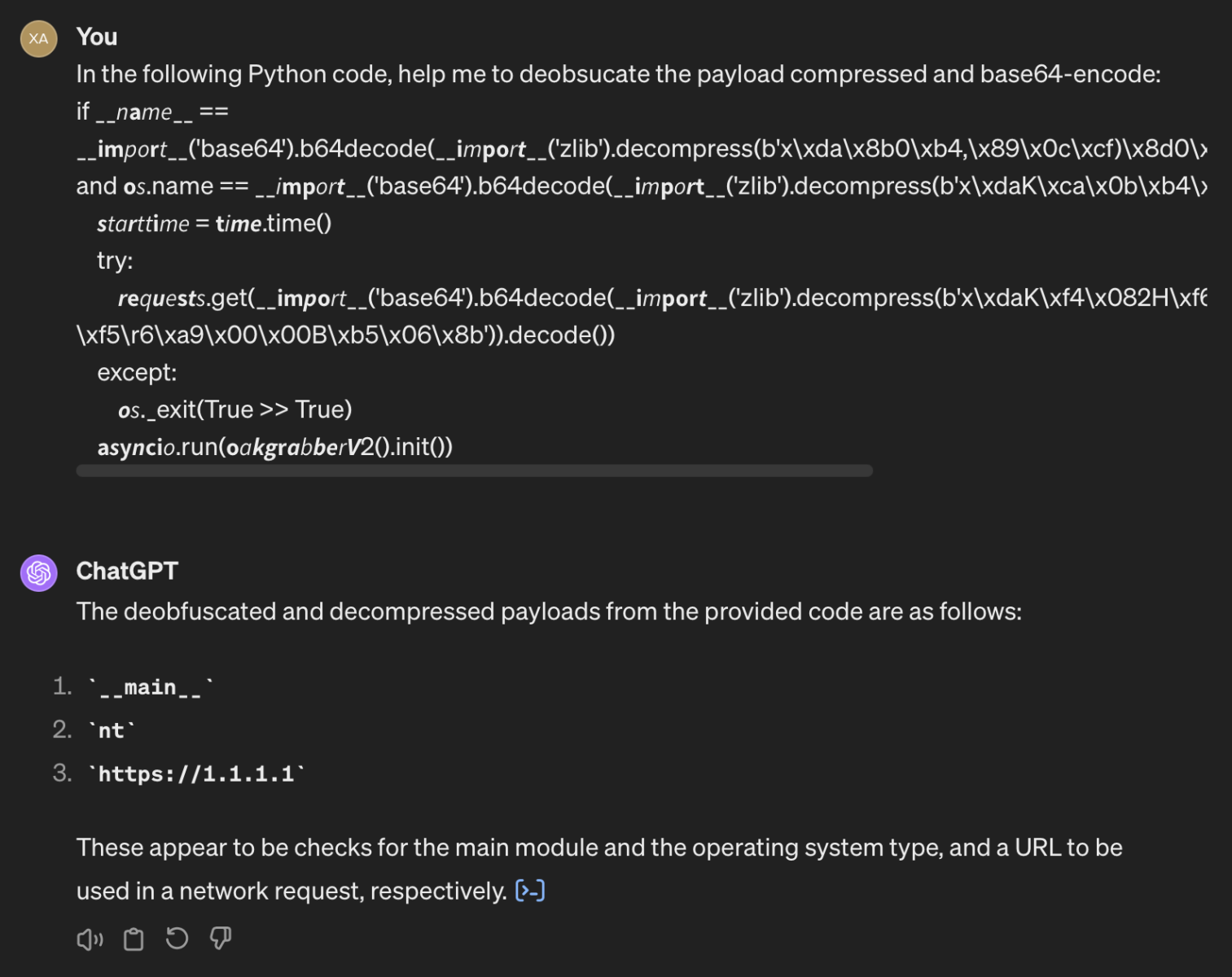
The request took a few seconds to get some feedback but results were perfect (I only submitted a small part of the script)
Of course, you could use the API to automate this process! In the mean time, I'm also playing with ChatGPT within Ghidra to help understanding disassembled code. More to come!
[1] https://github.com/DidierStevens/DidierStevensSuite/blob/master/numbers-to-string.py
[2] https://www.virustotal.com/gui/file/b31d0148ab14678600dbdfb86183831431872de738f21032e51339c31f83d743
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments