Management of DMARC control for email impersonation of domains in the .co TLD - part 2
by Manuel Humberto Santander Pelaez (Version: 1)
In my previous DMARC diary, I was discussing how DMARC control is handled on all CO domains from April 2023 and provided the detail about this control for com.co domains.
In this diary we are going to talk about the results obtained for the 3465 gov.co domains and the 4115 edu.co domains. Let's see:
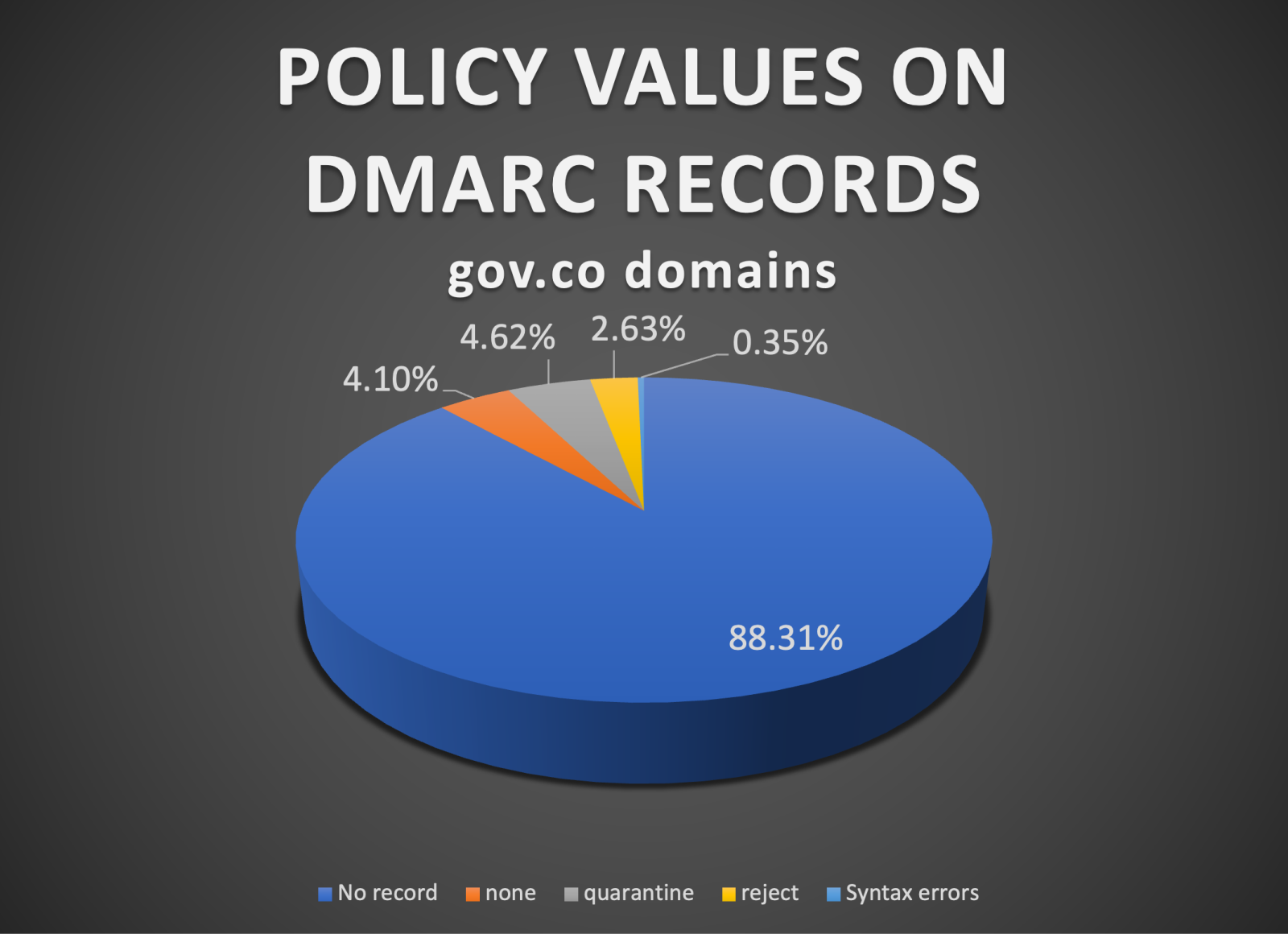
This indicates that 92.41% have no DMARC protection at all, 4.62% have a quarantine policy, 2.63% have a reject policy, and 0.35% have DMARC records with syntax errors.
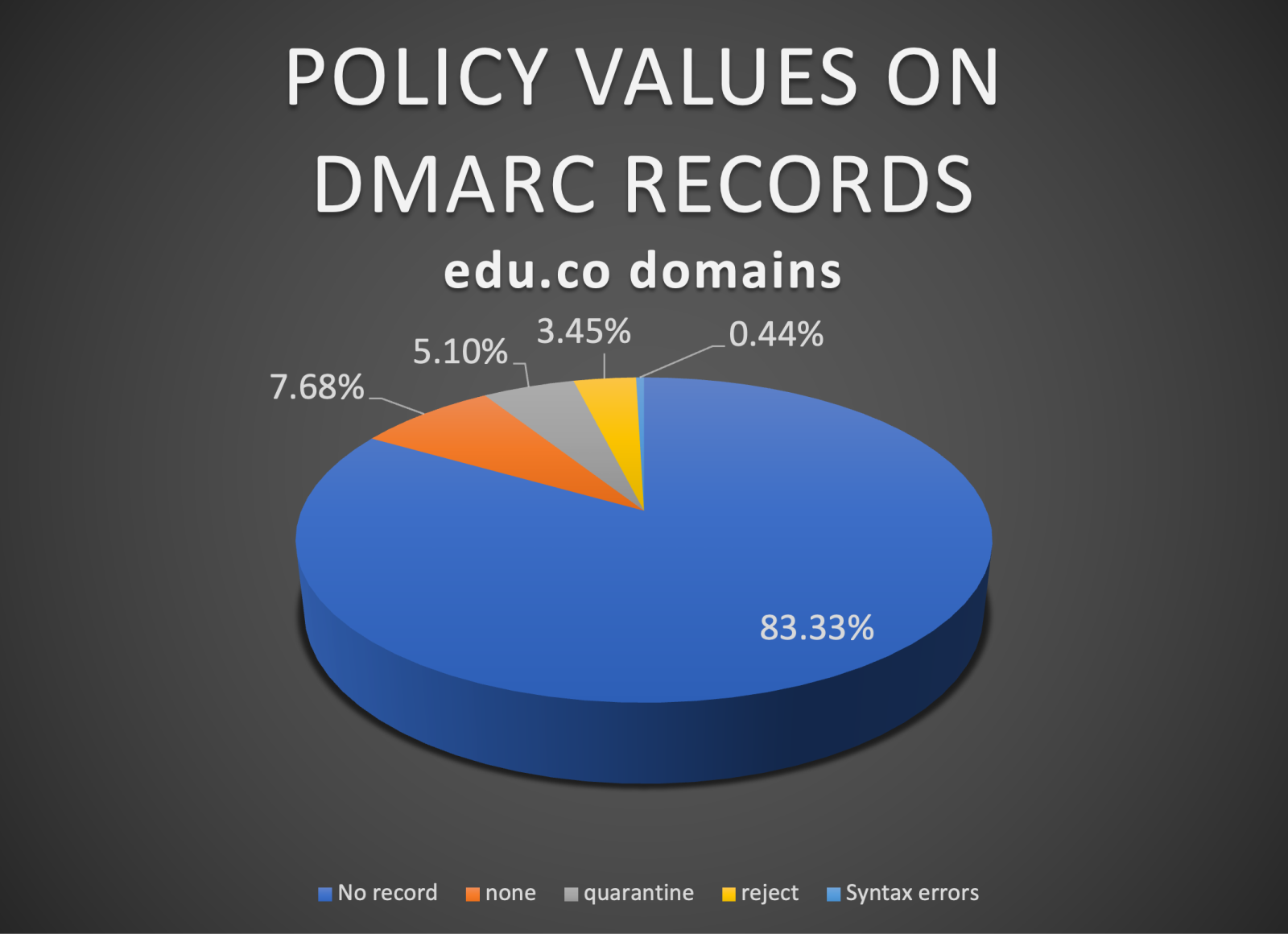
This indicates that 91.01% do not have any DMARC protection, 5.1% have a quarantine policy, 3.45% have a reject policy and this time the syntax errors in the DMARC record increased to 0.44%.
We can conclude the following about this topic:
- From the evaluated domains com.co, gov.co and edu.co, the one with the highest level of risk is gov.co, since the non-coverage of the control reaches 92.41%.
- The syntax errors in the DMARC DNS register are relevant as it constitutes a risk that can be avoided with even automated tasks. For some companies there is awareness on how important are security controls. However, human error becomes a relevant factor of vulnerability.
- The massification of controls based on DNS is so simple that it can easily be included in operational procedures, which do not distract staff and provide great value to the cyber risk management of institutions.
Manuel Humberto Santander Peláez
SANS Internet Storm Center - Handler
Twitter: @manuelsantander
Mastodon:[email protected]
Linkedin:manuelsantander
email:[email protected]


Comments