Analysis Of An "ms-msdt" RTF Maldoc
Malicious document "aaa.rtf" is an RTF file that downloads a html file that uses the ms-msdt handler to get a PowerShell script executed. This is explained in our diary entry "New Microsoft Office Attack Vector via "ms-msdt" Protocol Scheme (CVE-2022-30190)".
To analyze RTF files, I use my tool rtfdump.py.
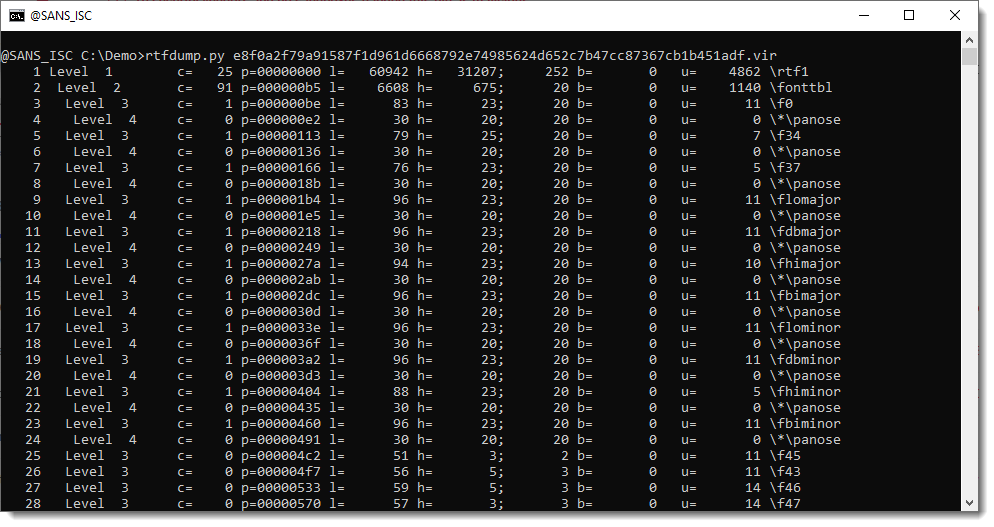
In the list of RTF entities, there's an object with an objclass + URL and objdata embedded object:
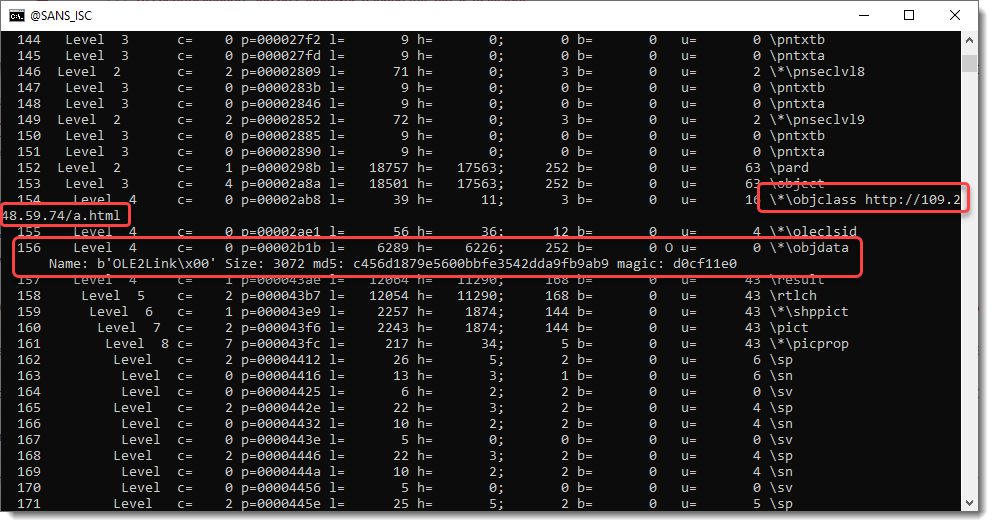
Here is the URL of the objclass:
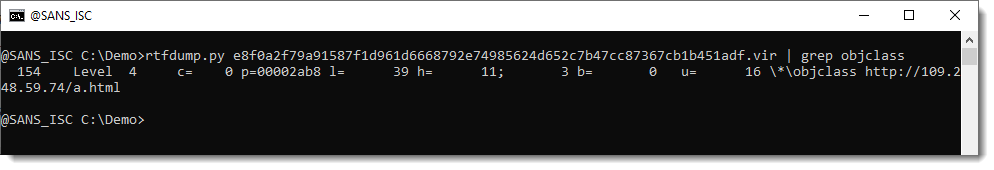
And here are the objects:
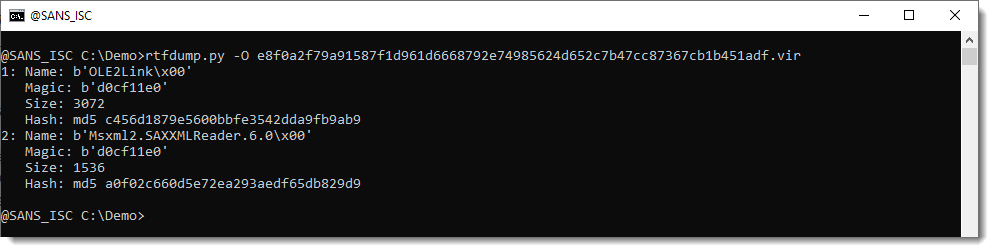
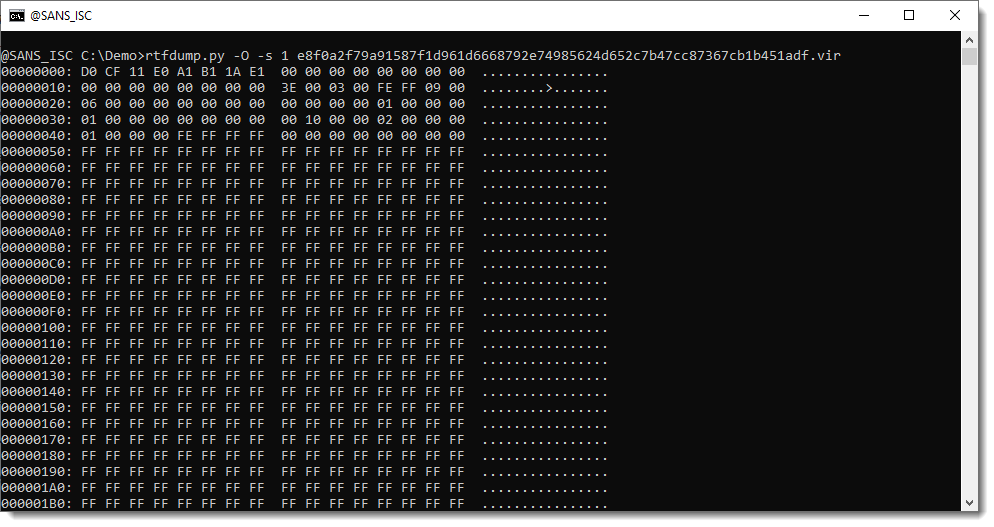
The first object is an OLE file that can be piped into oledump.py for analysis:
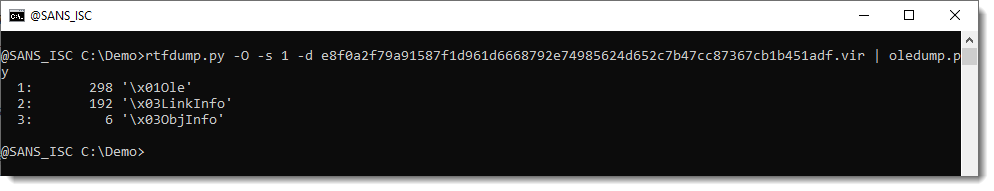
The \1Ole and \3LinkInfo streams contain URLs:
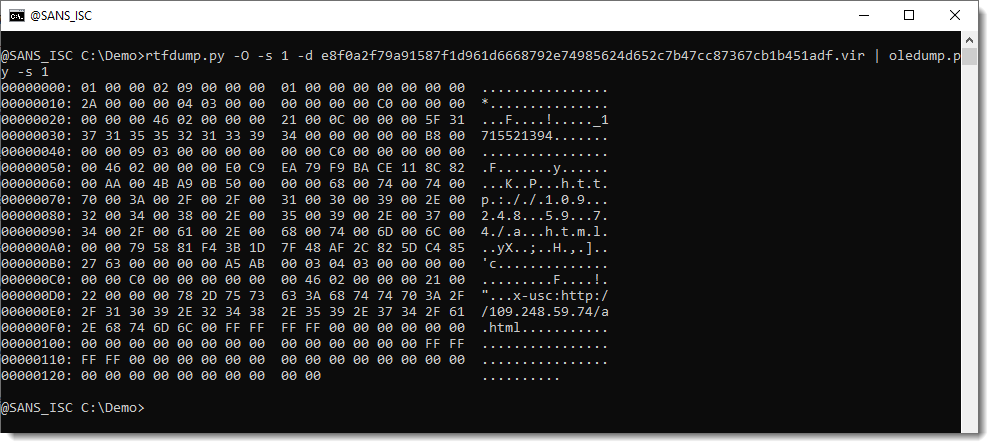
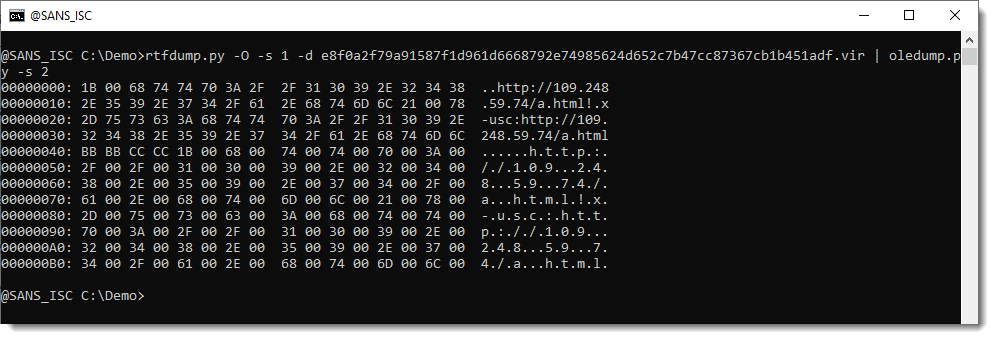
The structure of these streams is documented by Microsoft. But parsing is not necessary for this sample, we can also just extract the strings:
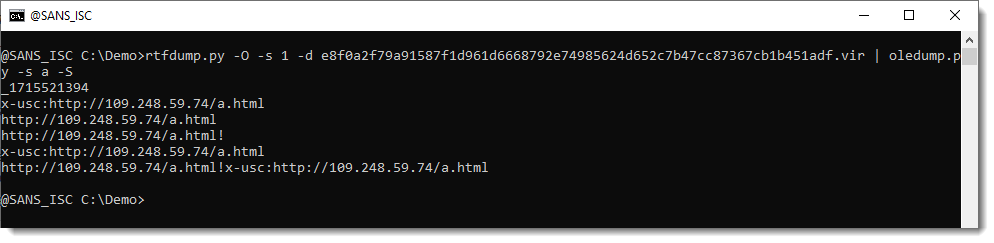
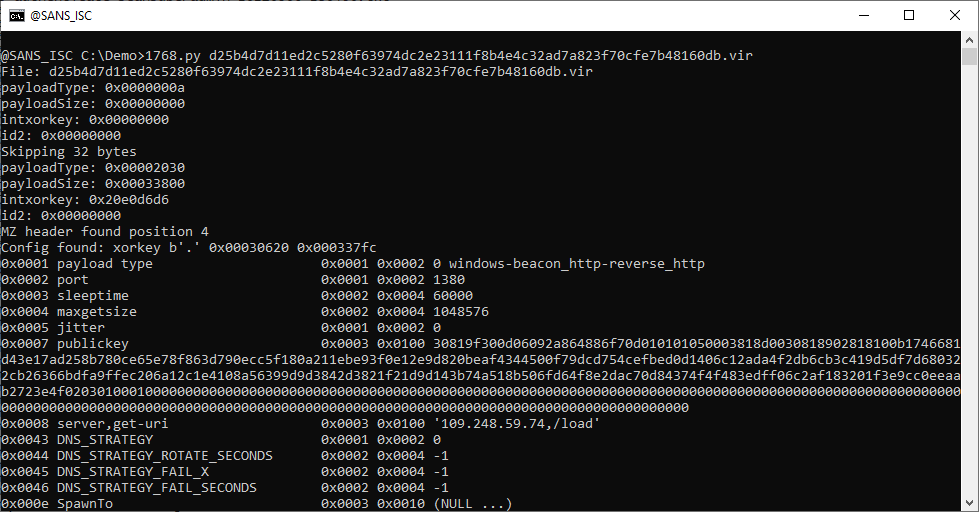
Looking on VirusTotal for the relations of this maldoc, I found PowerShell scripts and a Cobalt Strike beacon:
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com


Comments