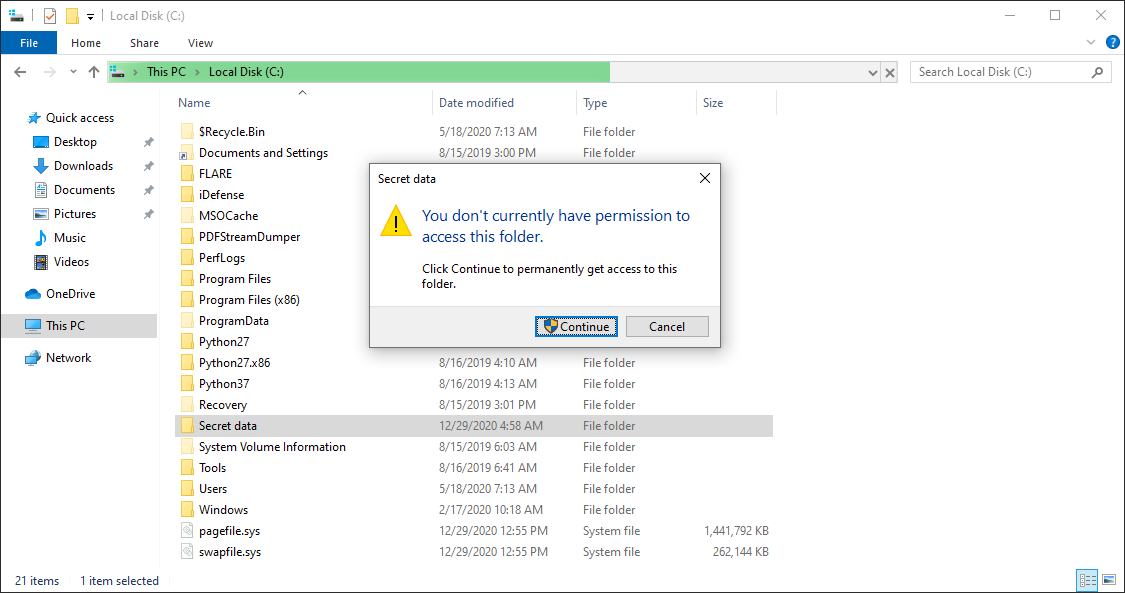
Want to know what's in a folder you don't have a permission to access? Try asking your AV solution...
Back in February, I wrote a diary about a small vulnerability in Windows, which allows users to brute-force names of files in folders, which they don’t have permission to open/list[1]. While thinking on the topic, it occurred to me that a somewhat-complete list of files placed in a folder one can’t access due to lack of permissions might potentially be obtained by scanning the folder with an anti-malware solution, which displays files which are currently being scanned.
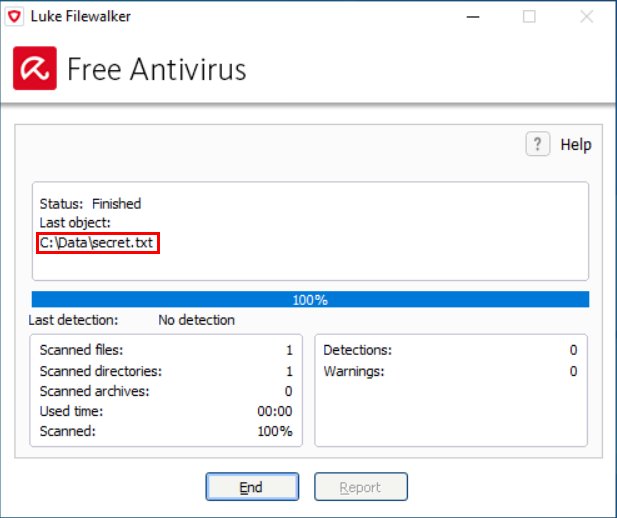
As you may see in the example above, names of scanned files are indeed displayed by some of the anti-malware solutions out there. And since most anti-malware tools run by necessity with high (i.e. SYSTEM level) privileges, and it is customary to allow any user to initiate a scan of arbitrary folder, this may easily lead to unexpected information disclosure (that is, unless the authors of the tool explicitly decided to stop users from scanning folders, for which they don’t have access permissions).
Admittedly, the impact of this would be rather low – unless the anti-malware solution logged the name of each scanned file in a way which would enable a user to read the entire log afterwards, it would be limited to disclosure of the names of files which the user would be able to see/record during the scan itself. Still, it might provide a way by which many anti-malware solutions might be used to bypass confidentiality controls set at the file system level.
Back in February, I decided to do a short test in order to see how large a portion of AV solutions might actually be abused this way. Since I didn’t intend to do a comprehensive analysis of all tools out there, I’ve limited the test to only 25 anti-malware tools from different vendors mentioned in the Wikipedia article on Comparison of antivirus software[2].
The results were quite interesting. Eight of the tools (i.e. approximately one third) didn’t scan contents of any folder, which was inaccessible to the user who initiated the scan, while the remaining seventeen did. Of these, eight did display the names of analyzed files during a scan.
One further point to note is that any of the 17 tools, which enabled users to scan arbitrary folders, might have been used in conjunction with Sysinternals Process Monitor[3] to discover names of all files in any folder (i.e. one would run ProcMon, initiate scan of a folder and then list all files in the relevant path which the anti-malware solution read).
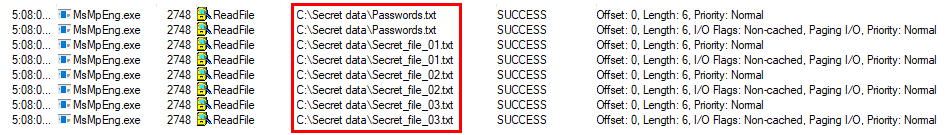
Of course, as this would require local administrator permissions on the part of the user, it is hardly a major issue, since the user could simply change the permissions on the target folder in order to gain access to its contents. Using anti-malware tool in conjunction with ProcMon would however not result in creation of any suspicious audit trail, which might be left behind, were one to simply change the access permissions.
Although the confidentiality impact of the behavior described above was quite low, I contacted all vendors, whose tools I have determined might be abused in this manner. My assumption was that for those anti-malware tools, which enabled users to scan folders they didn’t have access to, this was the result of an intentional design decision on the part of their authors, but I wanted to be sure.
Not every company replied, but for most of those which did, my assumption proved to be correct as the behavior of their tools was confirmed to be intentional. In only two cases the behavior was deemed to constitute a potential security risk and the vendors decided to change it in subsequent updates.
Even though it is only a low impact issue, it is good to know that it exists. After all, if the results of the test were representative for anti-malware solutions at large, low privileged users might potentially be able to use about each third one to partially bypass file system permissions preventing them from listing contents of folders and local admins could completely bypass them with the help of anti-malware in two out of three cases.
[1] https://isc.sans.edu/forums/diary/Discovering+contents+of+folders+in+Windows+without+permissions/25816/
[2] https://en.wikipedia.org/wiki/Comparison_of_antivirus_software
[3] https://docs.microsoft.com/en-us/sysinternals/downloads/procmon


Comments