Heartbleed, BlueKeep and other vulnerabilities that didn't disappear just because we don't talk about them anymore
Since new critical vulnerabilities are discovered and published nearly every day, it is no wonder that we (i.e. security professionals and security-oriented media) tend to focus on these and don’t return to the ones that came before too often. Unless there is a massive exploitation campaign, that is. This doesn’t present any problems for organizations, which manage to patch vulnerabilities on time, but for many others the “historical” vulnerabilities, which are not talked about anymore, still pose clear and present danger.
In my last post, we looked at the number of machines connected to the internet, which are still affected by CVE-2020-0796, also known as SMBGhost. Since the number was surprisingly high[1], it got me thinking about how high the numbers might be for other (and older) high-impact vulnerabilities.
Since I don’t have access to any tool, which would come even close to the ability of the Carna botnet to scan the entire internet in reasonable time[2], I’ve decided to go with Shodan once again and ask it for the numbers of machines vulnerable to specific CVEs.
To this end, I’ve put together a list of about a hundred high-impact vulnerabilities, which were discovered before 2020 and which might potentially be scanned for by Shodan. The list was mostly made up of relevant vulnerabilities from different “Top CVEs” lists[3,4] and vulnerabilities I found to be interesting in my previous searches. The list was therefore far from comprehensive, but I do believe the results for the top 10 most common vulnerabilities it included are worth a look.
| CVE | Number of affected systems | CVSSv3 |
|---|---|---|
| CVE-2019-0211 | 3357835 | 7.8 |
| CVE-2019-12525 | 1219716 | 9.8 |
| CVE-2015-1635 | 374113 | N/A, CVSSv2 10.0 |
| CVE-2019-13917 | 268409 | 9.8 |
| CVE-2019-10149 | 264655 | 9.8 |
| CVE-2019-0708 | 246869 | 9.8 |
| CVE-2014-0160 | 204878 | 7.5 |
| CVE-2019-9787 | 83951 | 8.8 |
| CVE-2019-12815 | 80434 | 9.8 |
| CVE-2018-6789 | 76344 | 9.8 |
The numbers reported by Shodan were generally higher than I would have expected. Nevertheless, although it is true that Shodan results aren’t necessarily fully up to date or completely accurate, I’ve tried to validate a small subset of the detections manually with relevant Nmap scripts (those, which were not too intrusive) and most of my findings agreed with the results Shodan provided.
Although all the CVEs listed in the table are certainly noteworthy, the ones which I was particularly surprised to see, given their prior media coverage, were:
- CVE-2015-1635, a RCE in IIS web server, for which it – quite fortunately – appears that no one published a full exploit so far – all the available PoCs seem to lead “only” to information leakage and DoS[5],
- CVE-2019-10149, an RCE in Exim MTA, which was mentioned in – among other places – an NSA advisory warning against its active exploitation by a Russian APT group earlier this year[6], and perhaps most surprisingly
- CVE-2019-0708, dubbed BlueKeep, along with a historical favorite
- CVE-2014-0160, also known as Heartbleed.
Especially the results for the last two vulnerabilities show that even very well-known vulnerabilities are sometimes left unpatched for years on end.
Unfortunately, I don’t have data for the historical development of the number of machines affected by Hearbleed, but I can offer you a look at how the numbers changed for BlueKeep over the last 12 months.
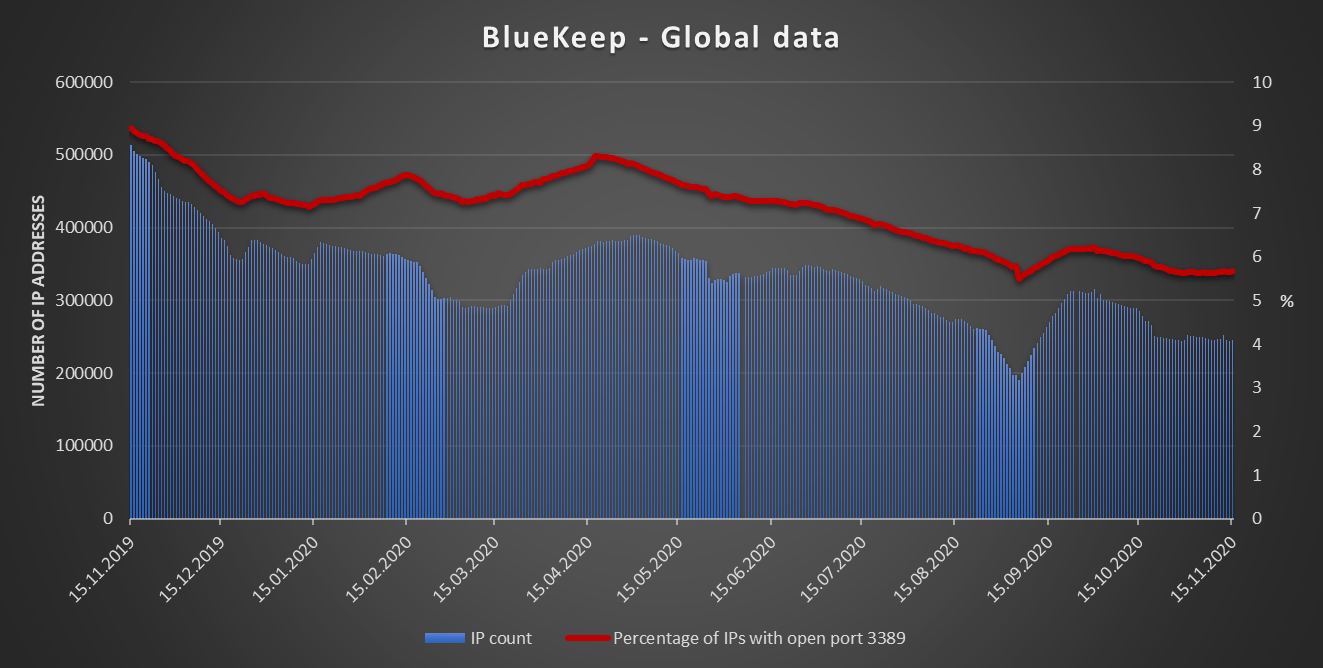
Although, as the chart shows, there has been a significant absolute as well as relative decline in the number of BlueKeep-affected machines accessible from the internet, there still appear to be over 240 000 of them. Given how dangerous and well known BlueKeep is, it rather begs the question of how many other, less well-known critical vulnerabilities are still left unpatched on a similar number of systems.
And since any of these might potentially come back to haunt us one day, this would seem to be a question worth asking…
[1] https://isc.sans.edu/diary/26732
[2] https://en.wikipedia.org/wiki/Carna_botnet
[3] https://www.cvebase.com/cve/pocs
[4] https://us-cert.cisa.gov/ncas/alerts/aa20-133a
[5] https://www.trendmicro.com/en_us/research/15/e/iis-at-risk-an-in-depth-look-into-cve-2015-1635.html
[6] https://us-cert.cisa.gov/ncas/current-activity/2020/05/28/nsa-releases-advisory-sandworm-actors-exploiting-exim


Comments
Anonymous
Nov 18th 2020
5 years ago
Edit: apparently sans doesn't like emojis, emoticons it is then.
Anonymous
Nov 19th 2020
5 years ago