Performing deception to OS Fingerprint (Part 1: nmap)
by Manuel Humberto Santander Pelaez (Version: 1)
How can you know which operating system is running on a specific remote host? The technique to answer this question corresponds to the fingerprinting of the operating system and is executed by sending a specific set of packages to the remote host and see how it behaves. Each operating system responds differently, which allows it to be identified.
This will be a set of two diaries covering how nmap and p0f performs OS fingerprinting.
This diary will cover nmap. For its content, a virtual machine will be used in VMWare with Ubuntu 16.04 operating system and a network capture, which can be downloaded from here. The following topology is being used:
Now we perform an nmap OS fingerprint scan to 192.168.42.131 using -O option:
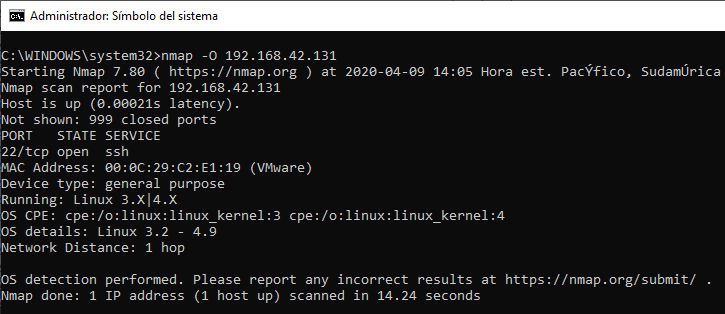
The only opened port we find is TCP/22. So, after performing a network capture, we can have a look to all the packets being sent to that specific port using the following wireshark filter: ip.src == 192.168.42.1 and ip.addr == 192.168.42.131 and tcp.port == 22
.png)
Now we proceed to break down packet number 2003. Below you can see its hex dump. Can you get the same values as me for the fields that I will describe below? Remember that the package includes the level 2 headers of the OSI model:
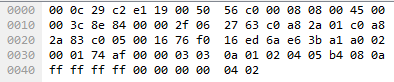
- Seq: As seen in wireshark, this is the relative TCP sequence number. Since this is the first packet, it is set to 0. The raw sequence number for the packet is 1995445997.
- Win: This is the TCP Window size. It is set to 1.
- Len: TCP segment length is 0. Total length for the IP Packet is 60 bytes. IP Header length is 20 bytes, TCP Header length is set to 40 bytes. TCP segment length = Length of IP Packet - IP Header Length - TCP Header Length = 60-20-40 = 0.
- WS: TCP Window Scale Factor. This TCP Option 3. Since TCP window is the receive buffer for incoming data that has not been processed yet by the application, sometimes it falls short due to it's maximum size of 65535 bytes. RFC 1323 allowed to expand the size of the Window by introducing a Window Scale. For this packet is 10, so the Window Scale Factor is 2^10=1024. Since original TCP Window size for this packet is 1 byte, the enhanced Window would be 1 byte * 1024 = 1024 bytes.
- MSS: Maximum Segment Size.
- TSVal and TSecr: This is TCP option 8. Time Stamp Value (TSVal) has the current value of the timestamp clock of the TCP sending the option, which can be in the range 1 ms to 1 sec per tick according to RFC 1323.Time Stamp Echo Reply (TSecr) contains the timestamp value that was sent by the remote host in the TSval field of a timestamps option
- SACK_PERM: This is TCP Option 4. SACK-permitted option alters the acknowledgment behavior of TCP. It is offered to the remote end during TCP connection establishment as an option to an opening SYN packet allowing selective acknowledgment of permitted data. The default TCP acknowledgment behavior is to acknowledge the highest sequence number of in-order bytes.
Let's verify the responses for some specific packets. There are no TCP answers for packet 2023 (TCP packet with no flags):
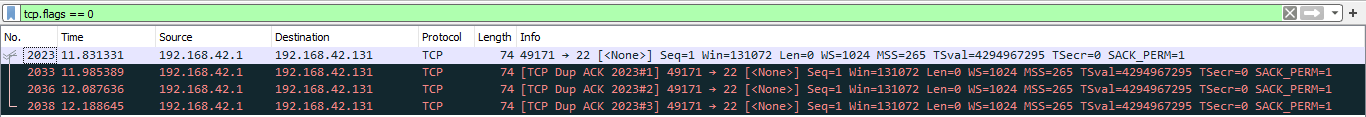
What about the answer for packet 2003?
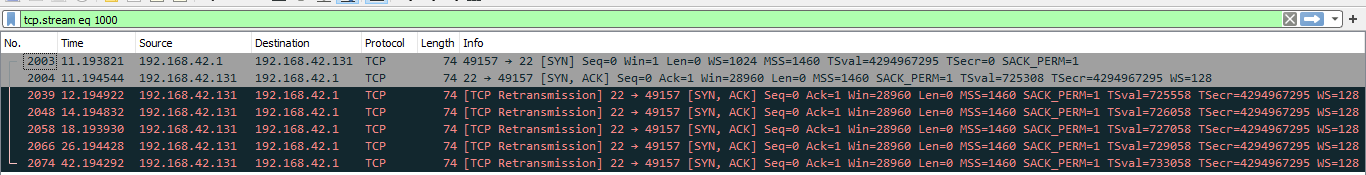
These answers are processed by nmap to determine what is the operating system of the remote host.
How can you forge the remote host answers to these specific nmap os fingerprint packets? Let's use OSFooler:
1. Download the tool:
2. Setup and install the tool. You need to have previously installed python-setuptools and python-nfqueue:
3. Update the tool with the latest nmap database:
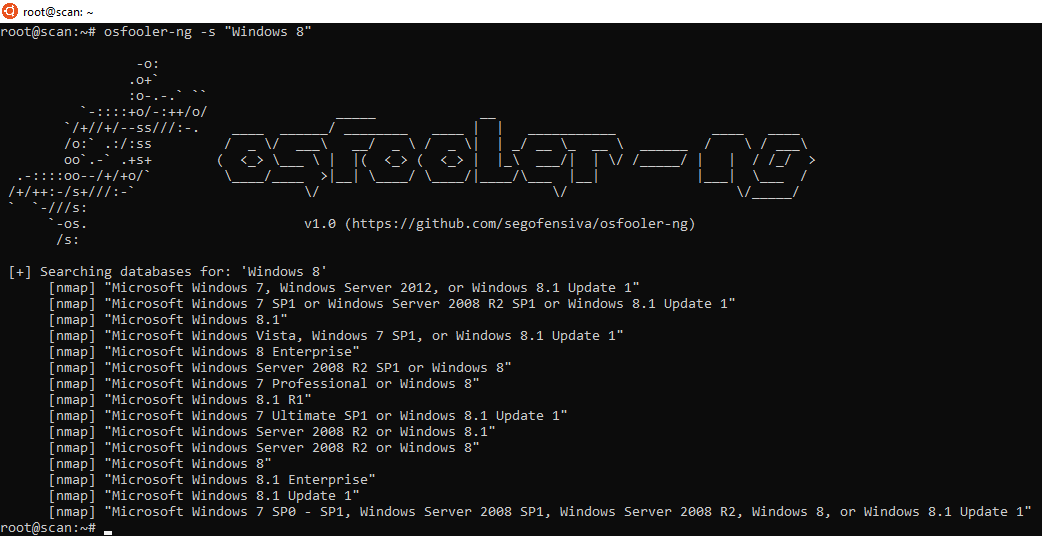
4. Let's find a fingerprint for Windows 8 to forge:
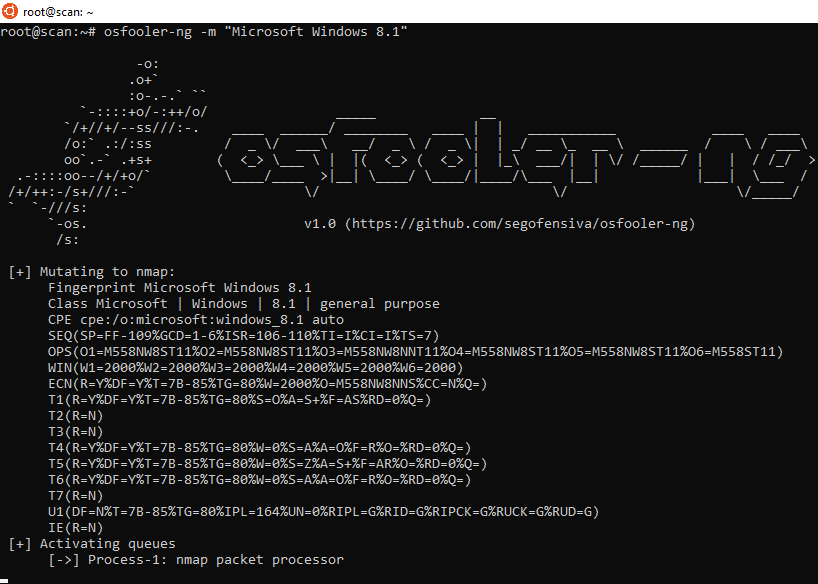
5. Let's forge the answers of the linux machine to make it look a Windows 8.1:
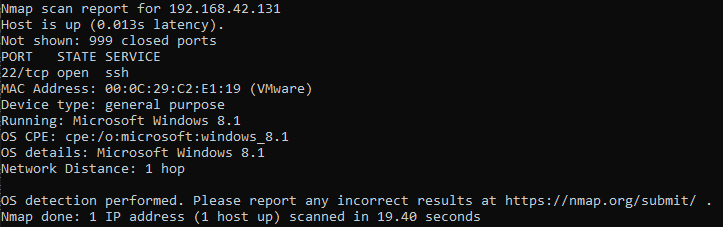
6. To nmap, the linux machine now looks like a Windows 8.1:
Do you know any other interesting tools to fool OS fingerprint? Feel free to comment this diary or contact us.
Manuel Humberto Santander Pelaez
SANS Internet Storm Center - Handler
Twitter:@manuelsantander
Web:http://manuel.santander.name
e-mail: msantand at isc dot sans dot org


Comments