Ransomware in Node.js
Happy new year to all! I hope that you enjoyed the switch to 2020! From a security point of view, nothing changed and malicious code never stops trying to abuse our resources even during the holiday season. Here is a sample that I spotted two days ago. It’s an interesting one because it’s a malware that implements ransomware features developed in Node.js[1]! The stage one is not obfuscated and I suspect the script to be a prototype or a test… It has been submitted to VT from Bahrein (SHA256:90acae3f682f01864e49c756bc9d46f153fcc4a7e703fd1723a8aa7ec01b378c) and has currently a score of 12/58[2].
The first stage is a VBScript that decodes the ransomware, setup persistence and deploys a local Node.js instance running the generated files in %USERPROFILE%\AppData\Local:
\GFp0JAk\lLT8PCI.js \GFp0JAk\node_modules\graceful-fs\fs.js \GFp0JAk\node_modules\graceful-fs\package.json \GFp0JAk\node_modules\graceful-fs\graceful-fs.js \GFp0JAk\node_modules\graceful-fs\legacy-streams.js \GFp0JAk\node_modules\graceful-fs\polyfills.js
Node.js is downloaded from hxxps://nodejs[.]org/download/release/latest-v8.x/win-x86/node.exe and saved as %USERPROFILE%\AppData\Local\GFp0JAk\GFp0JAk.exe
Persistence is added via Registry keys:
oShell.RegWrite "HKCU\Software\Microsoft\Windows\CurrentVersion\Run\Microsoft Office", "wscript " & strVbs,"REG_SZ" oShell.RegWrite "HKCU\Software\Microsoft\Windows\CurrentVersion\Run\Startup", strExe & " " & outWorkingDir & "\" & strEntPoint & " decryptStatic","REG_SZ" oShell.RegWrite "HKCU\Software\Microsoft\Windows\CurrentVersion\Run\Windows", "cmd /c start /min " & outWorkingDir & "\How-to-buy-bitcoins.html","REG_SZ"
The script main loop performs the following tasks every 40 seconds:
- Checks if node.exe has been successfully downloaded and, if not, it downloads and dumps it to the disk
- Dumps the Node.js module and files to disk (see the list above)
- Deploys the Node.js code.
Once done, an “initdone” file is created and the desktop layout reset (icons & positions) by deleting the registry key:
HKCU\Software\Microsoft\Windows\Shell\Bags\1\Desktop
Now, let’s have a look at the Node.js code, the ransomware itself.
This code is obfuscated but easy to process with a Javascript beautifier. Here is some interesting extracted information:
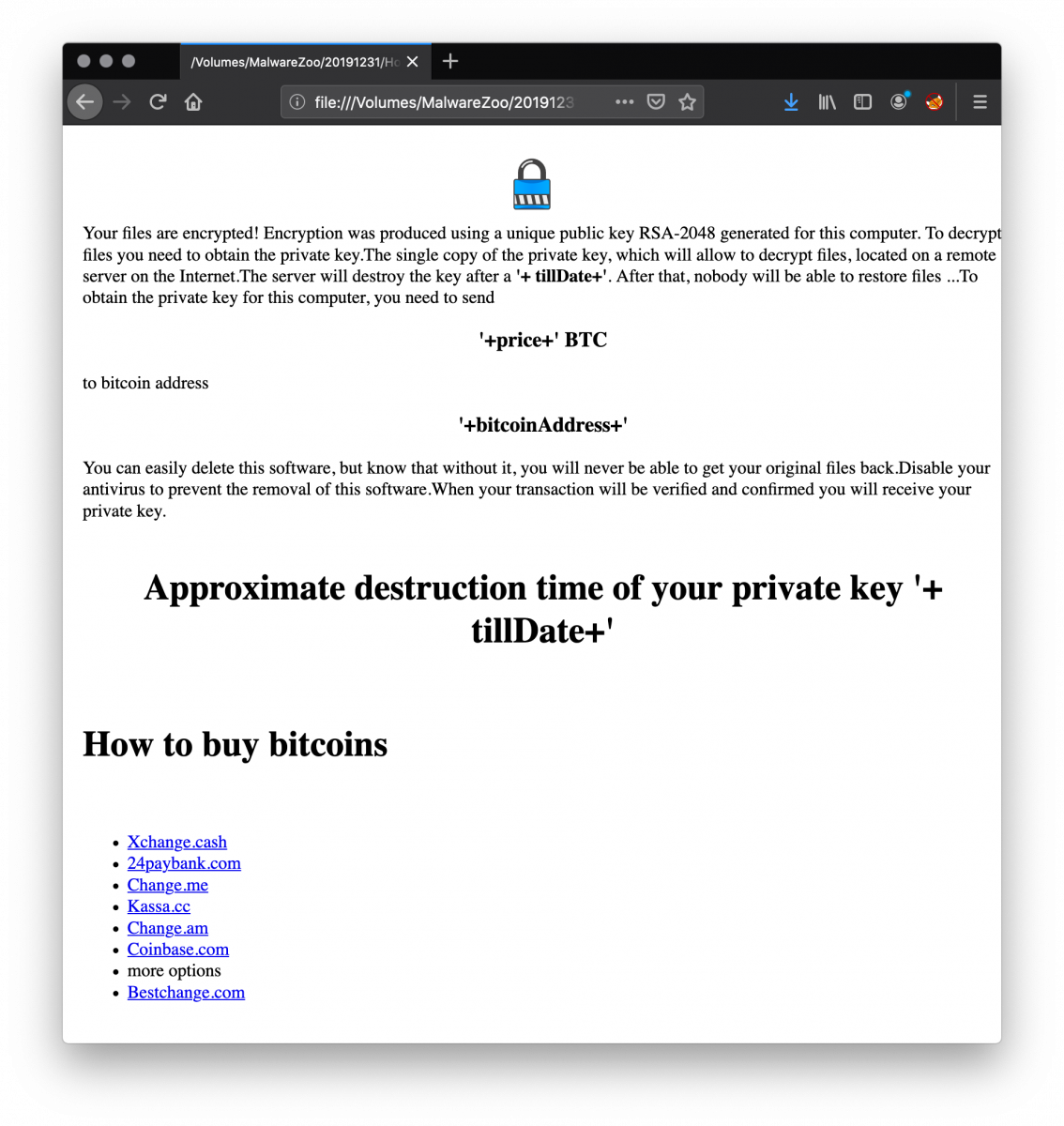
Ransom price: 0.4 BTC
Bitcoin wallet: 18aBKwKJvMCkZmpkcCbW9b9y9snAmU3kgo[3]
Encryption is performed via a public/private key pair.
Files to encrypt are scanned via this function:
scan = function() {
var b = [];
b.push(userprofile + ""\\
Desktop "");
b.push(userprofile + ""\\
Documents "");
b.push(userprofile + ""\\
Downloads "");
b.push(userprofile + ""\\
Contacts "");
b.push(userprofile + ""\\
Pictures "");
b.push(userprofile + ""\\
Music "");
b.push(userprofile + ""\\
Videos "");
b.push(userprofile + ""\\
AppData\\ Local\\ Microsoft\\ Outlook "");
for (var a = 0; 25 > a; a++) {
var c = String.fromCharCode(66 + a) + "": "",
d = c + ""\\
"" + testFile;
if (fs.existsSync(c)) try {
fs.writeFileSync(d, ""
"", ""
utf - 8 ""), b.push(c), removeFile(d)
} catch (e) {}
}
return b
};
The ransomware notification is also generated on the fly:
I did not find a contact email address for the victims and the encrypted file extension is empty in the code. If you have more information about this sample, please share it!
[1] https://nodejs.org/en/
[2] https://www.virustotal.com/gui/file/90acae3f682f01864e49c756bc9d46f153fcc4a7e703fd1723a8aa7ec01b378c/detection
[3] https://www.blockchain.com/btc/address/18aBKwKJvMCkZmpkcCbW9b9y9snAmU3kgo
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments