What is "THAT" Address Doing on my Network
Disclosure: ISC does not endorse any one particular vendor. That said, you may recognize what type of firewall I use :)
So this all started with a strange log entry with SYN packet going to a RFC1918 [1] Address. Now, that address is not in regular use on my network, all the more puzzling.
Below is the log entry in question, which indicates it is from my main gaming rig (i7-9700K, 128GB DDR4, (2) GTX1080 SLI, M.2 1TB). This desktop is only really used for gaming, not much browsing and very little else (Discord, etc). So lower risk (at least I thought).
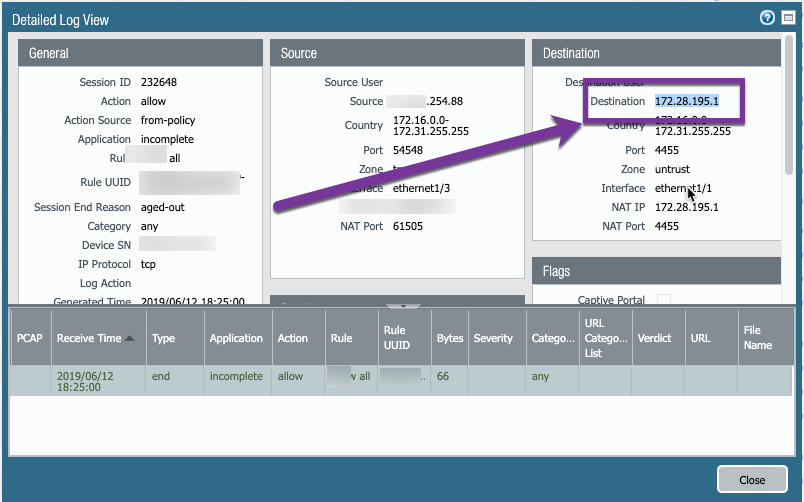
First step I took, was to take a look at a PCAP from the Firewall's view, so I setup my filter on the IP in question as a destination.
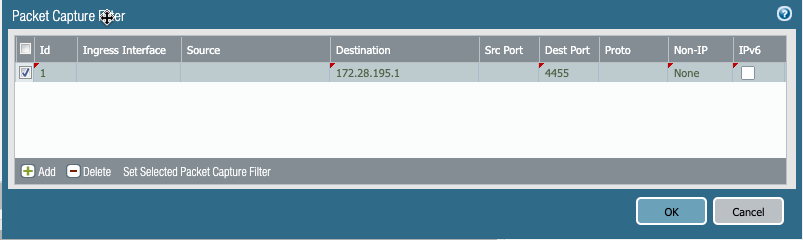
Started the capture.
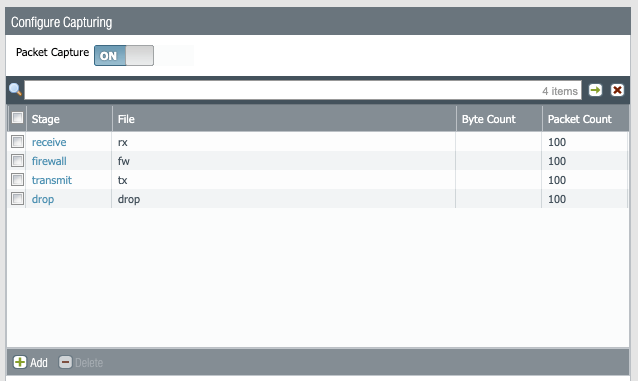
As expected, not much there, just a SYN packet.
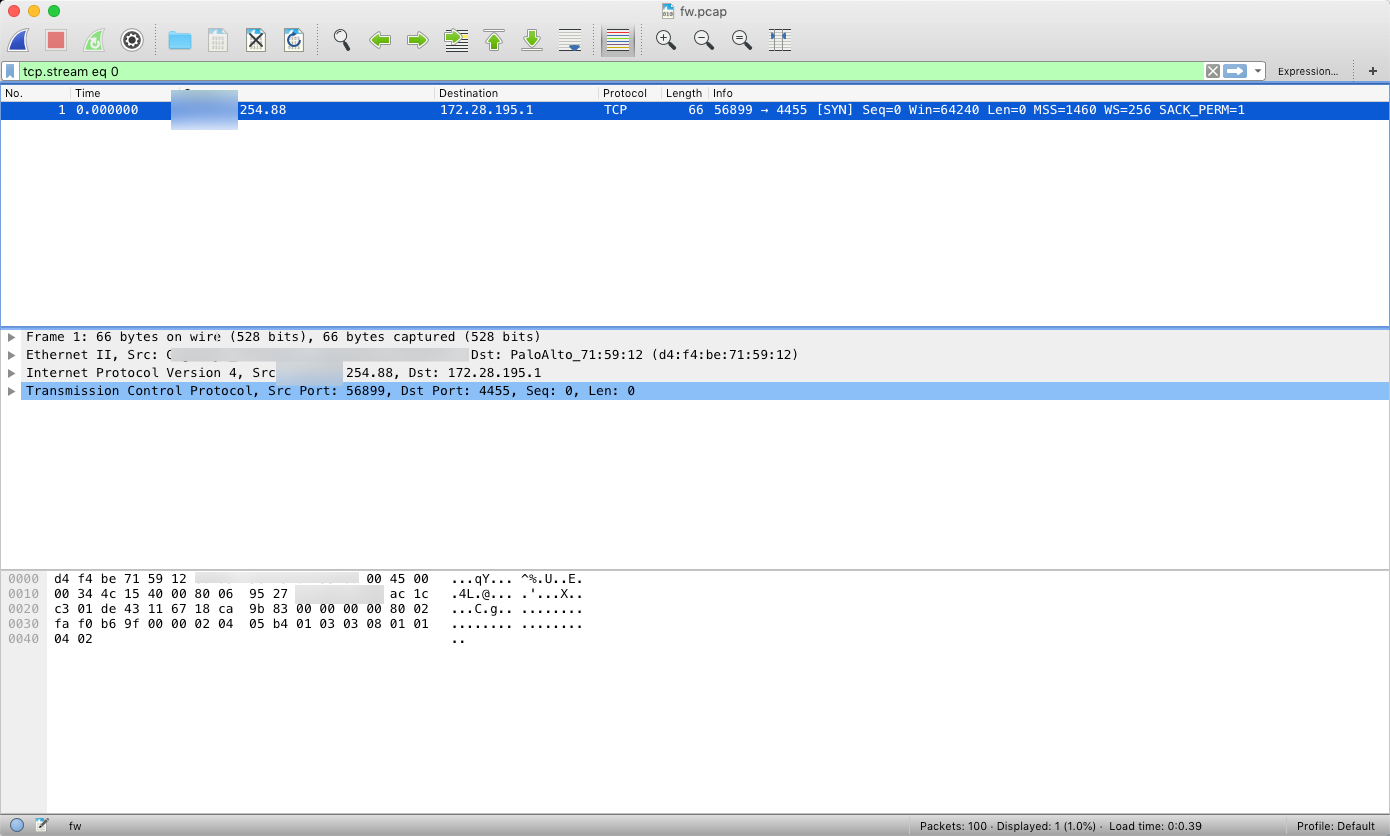
What to do now? To the TCPView [2] BatMAN!!! It took a few moments for the "offending" process to pop up, so this capture was in real-time (or in other words, I clicked the "Capture" button when I saw it).
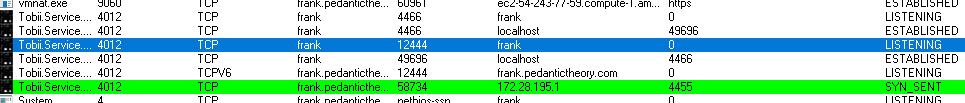 And yes, my gaming rig is FRANK, and the beauty of letting you see part of my domain name? Is there is an english joke in there somewhere :). So Found the Tobii service as the 'offender.' Tobii Gaming [3] makes eye tracking hardware (fantastic aiming assistant and helps me keep up with those that use mouse/keyboard). This hardware I happen to use when playing some games *cough* Division 2 *cough* so that got less interesting. We need a few more things, but we are starting to draw a conclusion.
And yes, my gaming rig is FRANK, and the beauty of letting you see part of my domain name? Is there is an english joke in there somewhere :). So Found the Tobii service as the 'offender.' Tobii Gaming [3] makes eye tracking hardware (fantastic aiming assistant and helps me keep up with those that use mouse/keyboard). This hardware I happen to use when playing some games *cough* Division 2 *cough* so that got less interesting. We need a few more things, but we are starting to draw a conclusion.
Now to break out Process Hacker [4] and dump it out of memory.
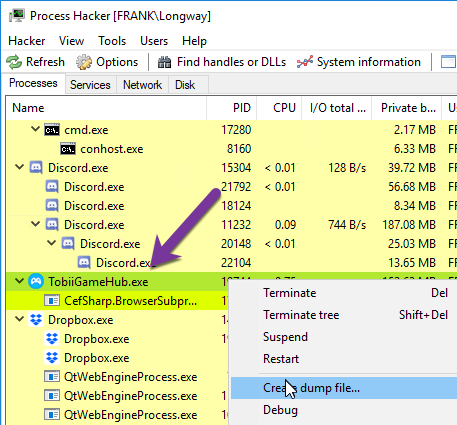
Once dumped, we went straight to our reliable 'super expensive' tools grep and strings (that's sarcasm, they are open source :)...
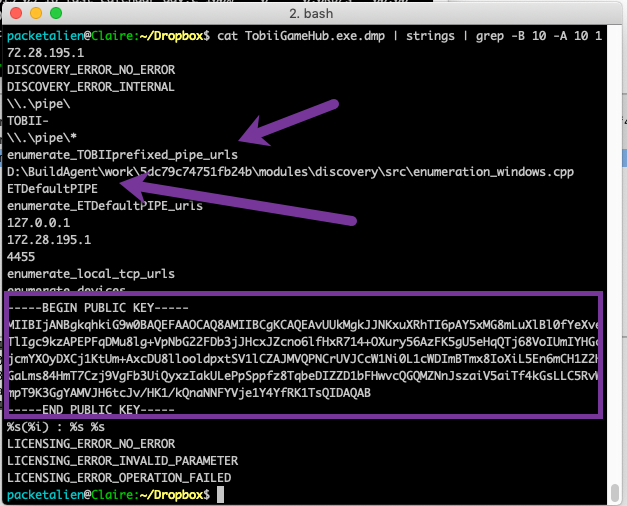
Running a dump using a couple of switches with grep after sending the dmp through strings, we can see on either side of the IP.
cat <file>| strings | grep -B 10 -A 10 <ip>
It did produce an interesting artifact, a public key, but cemented the conclusion that this was likely developer code left over in the compile. Let me know what you think? Now that we've taken a look, I plan to update the Tobii engine and suspect that this problem will go away. If there is anyone from Tobii that is reading, thanks for the support!
Summary
Not 'every' indicator has to nessessarily be evil and with some basic tools, you can start to put a story together on things. In this case, just the PCAP engine on my firewall, Process Hacker and TCPView, then on my *nix platform, cat, strings and grep. Remember, humans (for now) write most code and we all write perfect code right?
[1] https://tools.ietf.org/html/rfc1918
[2] https://docs.microsoft.com/en-us/sysinternals/downloads/tcpview
[4] https://processhacker.sourceforge.io/


Comments
Anonymous
Jun 13th 2019
6 years ago
Anonymous
Jun 13th 2019
6 years ago